From U.S. executive orders to cyber laws, outstanding cybersecurity insurance policies are growing their inclusion of Third-Get together Danger Administration requirements, and for good cause – each group, it doesn’t matter what dimension, is impacted by third-party dangers.
Should you’re in search of a TPRM software program answer to reinforce the effectivity of your TPRM program, this put up will enable you consider the highest contenders out there.
Third-Get together Danger Administration vs. Vendor Danger Administration
Third-Get together Danger Administration (TPRM) addresses a broad market of third-party dangers, corresponding to these originating from the next third-party sources:
- Enterprise associates
- Contractors
- Third-party suppliers
- Enterprise partnerships
As a subset of TPRM, Vendor Danger Administration (VRM) additional narrows the main focus of threat mitigation efforts to third-party distributors, particularly the administration of cybersecurity and regulatory compliance dangers.
Learn about the top VRM solutions on the market >
The Scope of Third-Get together Danger Administration
As a result of Third-Get together Danger Administration encompasses all types of third-party dangers, TPRM options range in threat area scope. On the excessive finish of the spectrum, a TPRM platform may deal with all sixteen third-party dangers.

Trade-specific TPRM options are inclined to slender the main focus to threat domains which are prevalent within the trade. For provide chain leaders, TPRM platforms may deal with as much as 13 threat elements, disregarding low-relevance dangers like Competitors, Office Well being and security, and Competitors

For IT Leaders, a TPRM device may deal with as much as 10 threat domains:

For Authorized and Compliance Leaders, the danger area scope narrows additional to emphasis on ten threat classes.

What are the Options of the Finest Third-Get together Danger Administration Options?
A TPRM device addressing the broadest scope of trade use instances helps the next crucial Third-Get together Danger Administration necessities.
- Danger Identification – The correct detection of third-party dangers throughout threat profiles related to TPRM, corresponding to regulatory compliance, cyber framework alignment, and software program vulnerabilities.
- Danger Evaluation – Processes for evaluating the scope of detected third-party dangers and the projected influence of particular remediation duties.
- Danger Administration – A workflow addressing the whole threat administration lifecycle, from detection and evaluation, by means of to remediation.
- Danger Monitoring – Present a method of monitoring the efficacy of remediation efforts and the emergence of recent third-party dangers.
- Course of Automation – The applying of automation expertise to guide processes impeding TPRM effectivity, corresponding to third-party threat assessments and third-party vendor questionnaires.
Important Third-Get together Danger Administration Software program Metrics
Every answer on this listing will even be measured towards the next TPRM efficiency metrics:
- Consumer-Friendliness – A user-friendly TPRM platform that streamlines onboarding will enable you leverage funding returns quicker.
- Buyer Assist – Nice buyer assist will decrease TPRM program downtime when assist tickets are raised.
- Danger Scoring Accuracy – Correct threat ranking calculations guarantee service supplier inherent threat and residual dangers are promptly addressed earlier than they’re found by cybercriminals.
3 Finest TPRM Options In 2023
The highest three Third-Get together Danger Administration platforms enhancing TPRM program effectivity are listed under.
1. UpGuard
Efficiency In opposition to Key TPRM Options
Under is an outline of how UpGuard performs towards the seven key options of a super Third-Get together Danger Administration product.
(i). Third-Get together Danger Identification
UpGuard’s third-party threat detection characteristic works on a number of ranges. At a broad degree, this covers safety dangers related to third-party internet-facing property, detected by means of automated third and fourth-party mapping strategies – a course of involving the cybersecurity self-discipline, Attack Surface Management.
Watch this video for an outline of Assault Floor Administration and its position in managing third-party dangers.
At a deeper degree, UpGuard detects third-party dangers throughout the workflow of its threat evaluation framework, starting on the Proof Gathering stage and persevering with all through the continued monitoring element of the TPRM lifecycle.
Proof Gathering
Because the preliminary stage of the TPRM lifecycle, proof gathering entails combining threat info from a number of sources to kind a whole image of every third-party entity’s threat profile. UpGuard helps the evidence-gathering section of TPRM with the next capabilities.
- Assault Floor Scanning – Even earlier than an official partnership is finalized, customers get instantaneous entry to inherent threat insights for all monitored third-party assault surfaces by means of automated scanning outcomes.

- Belief and Safety Pages – Monitored third events could have publically accessible belief and safety pages with vital details about their information privateness requirements, cybersecurity packages, certifications, or any laws and frameworks being adhered to. The UpGuard platform will assign this info to all third events when it is accessible.

- Accomplished Safety Questionnaires – Any lately accomplished questionnaires will be appended as a part of the evidence-gathering course of or at a later stage as a part of a extra detailed threat evaluation.
- Further Proof – Any extra cybersecurity proof additional defining a third-party entity’s baseline safety posture, corresponding to certifications or different useful documentation.

Collectively, these options paint essentially the most complete image of a potential third social gathering’s threat profile through the evidence-gathering stage of the TPRM lifecycle.
Safety Questionnaires
UpGuard presents a complete library of safety questionnaires for figuring out third-party safety dangers stemming from regulatory compliance points and misalignment with widespread cyber frameworks. These questionnaires map to widespread trade requirements – together with GDPR, ISO 27001, PCI DSS, and so on. They’re fully customizable, making them adaptable to distinctive third-party threat administration processes and requirements.

Learn more about UpGuard’s security questionnaires >
Since regulatory compliance is a crucial threat area inside TPRM packages, UpGuard’s capacity to detect these dangers by means of its questionnaires is price highlighting. UpGuard robotically detects compliance gaps and assigns them a severity ranking primarily based on questionnaire responses. This class of third-party threat intelligence is a useful help to third-party compliance administration efforts.

Cybersecurity framework compliance can be price monitoring since alignment with requirements like NIST CSF could possibly be very helpful to TPRM efficiency.
Watch this video to learn the way UpGuard tracks alignment with NIST CSF and ISO 27001.
Safety Scores
The opposite characteristic forming a part of UpGuard’s complete third-party threat identification course of is its safety ranking device.
UpGuard’s safety scores assess every third-party entity’s assault floor by contemplating threat elements generally exploited by cybercriminals when making an attempt information breaches. These elements are divided throughout six classes of cyber dangers:
- Community Safety
- Phishing and Malware
- E-mail Safety
- Model and Popularity
- Web site Safety
- Questionnaire Dangers
UpGuard performs a passive safety configuration evaluation of all public digital property of monitored third-party entities throughout these threat classes. The result’s a quantified worth of every third-party relationship’s safety posture, expressed as a numerical rating starting from 0-950.
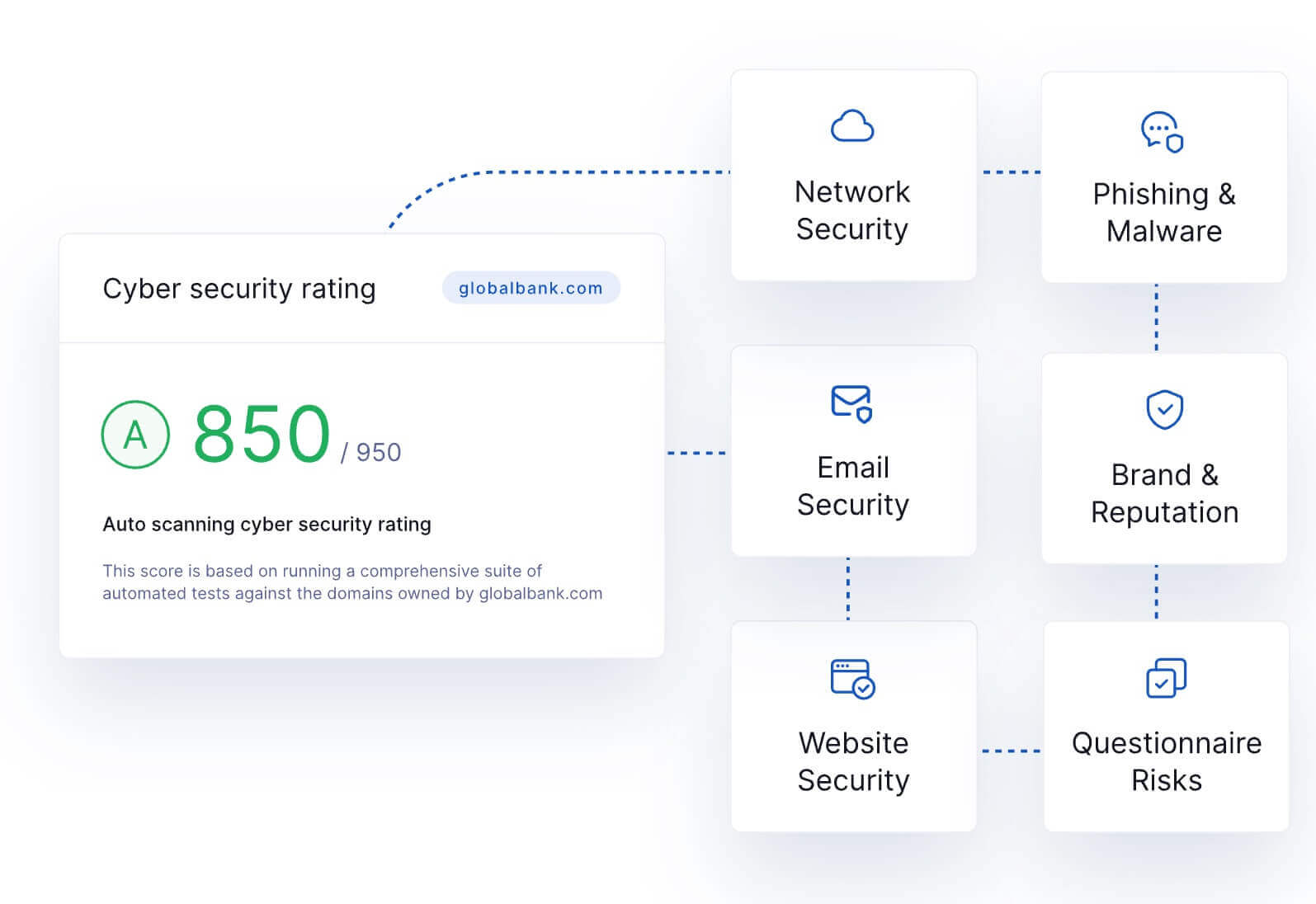
Learn more about UpGuard’s security ratings >
UpGuard’s safety scores provide real-time monitoring of third-party safety postures as part of a Third-Get together Danger Administration program.
UpGuard’s safety scores calculations adhere to the Principles for Fair and Accurate Security Ratings, to allow them to be trusted as goal indications of third-party cybersecurity efficiency.
By serving to threat remediation personnel decrease safety posture disruptions, UpGuard’s safety ranking expertise provides its third-party threat administration platform a major aggressive benefit.
All of those third-party threat identification processes feed into UpGuard’s third-party threat evaluation framework.
Watch this video for an outline of UpGuard’s threat evaluation course of.
(ii). Third-Get together Danger Evaluation
UpGuard’s third-party threat evaluation options purpose to streamline processes between threat detection and remediation. One methodology that is achieved is thru UpGuard’s remediation influence projections, the place the influence of chosen remediation duties on a company’s safety posture is estimated earlier than committing to a remediation plan.

Remediation projections assist safety groups prioritize duties with the best potential advantages on TPRM efficiency and the group’s total safety posture. Such foresight into the advantages of a remediation plan additionally retains safety groups ready for surprising stakeholder requests for updates on particular TPRM tasks.
UpGuard additionally performs its third-party threat evaluation by means of its vendor threat profiling characteristic, providing a single-pane-of-glass view of your group’s whole threat publicity.

Clicking on every threat unveils a risk overview that additionally lists impacted domains and IP addresses for a deeper evaluation of the origins of a particular threat.

With UpGuard, you possibly can monitor the danger profile of your subsidiaries and your subsidiary’s subsidiaries.
UpGuard additionally presents a Vulnerability module that filters an entity’s threat profile to listing all detected vulnerabilities. Choosing a vulnerability unveils a deeper degree of knowledge related to the publicity – a really useful help when urgently requiring assets for addressing zero-day occasions.


UpGuard also can robotically detect dangers primarily based on third-party safety questionnaire responses. These dangers may spotlight cyber framework alignment gaps or crucial regulatory violation dangers that should be rapidly addressed to keep away from expensive violation fines.

UpGuard’s safety questionnaire library maps to the requirements of widespread frameworks and laws. Together with NIST CSF, ISO 27001, PCI DSS, and plenty of extra.
Learn more about UpGuard’s security questionnaires >
Watch this video for an outline of how UpGuard tracks alignment with NIST CSF and ISO 27001.
Watch this video to learn the way UpGuard simplifies third-party threat administration with options streamlining vendor collaboration.
(iii). Third-Get together Danger Monitoring
Standard third-party threat monitoring strategies primarily acknowledge and monitor dangers detected throughout scheduled threat assessments. The issue with only a point-in-time method to threat monitoring is that any third-party dangers rising between evaluation schedules aren’t accounted for, which may go away a company unknowingly uncovered to doubtlessly crucial provider dangers throughout this era.

UpGuard solves this crucial downside by combining the deep threat insights from point-in-time threat evaluation with steady assault floor monitoring to supply real-time consciousness of the state of third-party assault surfaces, even between evaluation schedules.

(iv). TPRM Course of Automation
UpGuard’s AI Toolkit applies automation expertise to streamline what’s generally thought to be essentially the most irritating element of a Third-Get together Danger Administration program – third-party safety questionnaires.
With UpGuard’s AI Improve options, third-party entities now not have to obsess over the wording of questionnaire responses. Now, detailed and concise responses can immediately be generated from an enter so simple as a set of bullet factors, serving to responders focus solely on speaking worth. Not solely does this considerably scale back the time required to finish questionnaires, it additionally improves the general high quality of questionnaire responses, minimizing the necessity for back-and-forth clarification discussions.
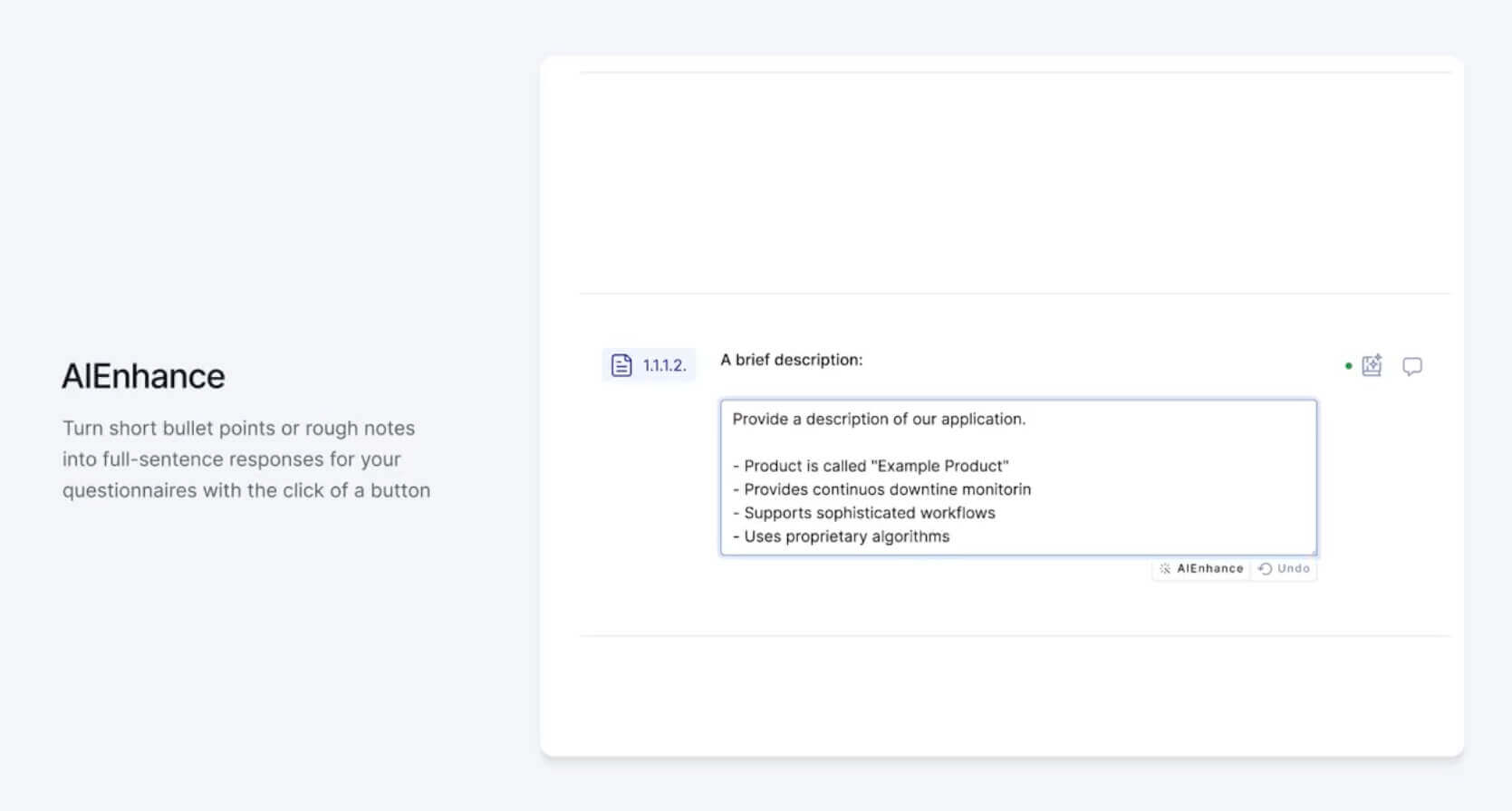
To additional scale back questionnaire completion instances, UpGuard’s AI Autofill characteristic attracts upon a database of earlier responses to supply third events with urged responses for approval. This characteristic presents a very important aggressive benefit for TPRM packages because it permits questionnaires to be submitted in simply hours.

With UpGuard’s AI Autofill options, safety questionnaires will be submitted in hours as an alternative of days (or weeks).
Watch this video to study extra about UpGuard’s AI Toolkit.
Key TPRM answer Efficiency Metrics
Under is an outline of how UpGuard measures towards the three major metrics of exemplary TPRM product efficiency.
(i). Consumer Friendliness
The UpGuard platform is taken into account among the many most intuitive and user-friendly TPRM answer choices.
“Highly effective and deep insights into exterior threat posture Easy and intuitive person interface. Nice assist.”
– 2023 Gartner assessment
“I actually worth how easy it’s to put in and function UpGuard. This system presents a whole cybersecurity reply and has an intuitive person interface.”
– 2023 G2 assessment
Download UpGuard’s G2 report >
(ii). Buyer Assist
UpGuard’s excessive customary of buyer assist has been verified by unbiased person critiques.
“Our account supervisor is all the time responsive when we now have questions, and assist supplies a response inside 24 hours every time.”
– 2023 Gartner assessment (read review)
“UpGuard presents the very best assist after onboarding. UpGuards CSM representatives are very skilled & immediate in responding to the problems raised. Tech assist can be nice.”
– 2023 G2 assessment (read review)
(iii). Third-Get together Danger Scoring Accuracy
UpGuard’s safety ranking adheres to the Principles for Fair and Accurate Security Ratings, providing peace of thoughts concerning the goal accuracy of their measurements and the objectivity of TPRM efficiency towards trade requirements.
Impartial person critiques additionally confirm the trustworthiness of UpGuard’s third-party risk-scoring methodologies.
“UpGuard presents essentially the most up-to-date and correct details about third events. Its third-party monitoring functionality is helpful for many medium to giant enterprises.”
2023 G2 assessment (read review)
2. SecurityScorecard
Efficiency In opposition to Key TPRM Options
Under is an outline of how SecurityScorecard performs towards the seven key options of a super Third-Get together Danger Administration device.
(i). Third-Get together Danger Identification
SecurityScorecard detects safety dangers related to the interior and third-party assault floor for a complete illustration of threat publicity. Found dangers map to widespread trade requirements, such as NIST 800-171, serving to safety groups establish alignment gaps and their particular causes.

Compliance threat discovery on the SecurityScorecard platform.
Nevertheless, many of the cyber threat checks on the SecurityScorecard platform are refreshed weekly, a major delay that might impede safety ranking accuracy.
UpGuard refreshes its IPv4 internet house scans each 24 hours.
See how UpGuard compares with SecurityScorecard >
(ii). Third-Get together Danger Evaluation
SecurityScorecard helps third-party threat evaluation with options like remediation influence projections and board abstract reporting.
Remediation Impression Strategies
On the SecurityScorecard platform, safety groups can see the projected influence of remediation duties on a company’s safety posture. This foreknowledge helps threat administration groups perceive the place to prioritize their remediation efforts to maximise the influence of restricted assets.

Cyber Board Abstract Stories
Board abstract stories will be immediately generated with a single click on. These stories robotically pull related TPRM information from all TPRM processes, permitting stakeholders to additionally take part in third-party threat evaluation discussions.

A snapshot of SecurityScorecard’s board abstract report.
UpGuard additionally presents a cyber board report era characteristic, with the choice of exporting stories into editable PowerPoint slides – a characteristic that considerably reduces board assembly preparation time (and stress).

(iii). Third-Get together Danger Administration
SecurityScorecard manages third-party dangers by means of Atlas, a platform for managing safety questionnaires and calculating third-party threat profiles.

Nevertheless, SecurityScorecard’s third-party threat administration options aren’t supplied inside a completely built-in TPRM workflow, which may trigger downstream TPRM course of disruptions, limiting the scalability of your TPRM program.
UpGuard, then again, streamlines the whole TPRM workflow for max scalability, integrating options supporting each stage of the TPRM lifecycle, together with:
- New vendor onboarding
- Third-party and vendor threat assessments
- Ongoing third-party ecosystem monitoring
- Annual third-party entity assessment
- Third-party offboarding
UpGuard is among the few cloud-based TPRM SaaS instruments supporting the end-to-end TPRM lifecycle.
(iv). Third-Get together Danger Monitoring
SecurityScorecard presents steady third-party threat monitoring by means of its safety ranking characteristic – a device for quantifying third-party safety posture and monitoring its efficiency over time.
SecurityScorecard primarily represents third-party safety posture as a letter grade representing the probability of a 3rd social gathering struggling a knowledge breach, starting from F (almost definitely to be breached) to A (least prone to be breached)
SecurityScorecard ranking calculations take into account threat elements like DNS Well being, Social Engineering dangers, Software Safety, Endpoint Safety, and Software program Patching Cadences.

(iv). TPRM Course of Automation
SecurityScorecard leveraged automation expertise to expedite safety questionnaire completions. Utilized to its whole library of questionnaire templates mapping to widespread laws and requirements, SecurityScorecard’s automation expertise may scale back questionnaire completion instances by 83% by suggesting responses primarily based on beforehand submitted questionnaires.
By implementing automation expertise into its questionnaire processes, SecurityScorecard may assist scale back questionnaire completion instances by 83%.
Key TPRM answer Efficiency Metrics
Under is an outline of how SecurityScorecard measures towards the three major metrics of exemplary TPRM product efficiency.
(i). Consumer Friendliness
The SecurityScorecard platform doesn’t have a popularity for being essentially the most intuitive or user-friendly.
“The device was not as user-friendly as its opponents. It’s for extra tech-heavy customers. This device is not splendid for collaboration with different enterprise models corresponding to authorized/contract mgmt.”
– G2 assessment (read review)
(ii). Buyer Assist
SecurityScorecard’s buyer assist staff could be very attentive to troubleshooting queries.
“SS has a responsive assist staff. which is crucial to me on time-sensitive tasks.”
– G2 assessment (read review)
(iii). Danger Scoring Accuracy
SecurityScorecard’s threat scores don’t all the time replicate the precise state of a third-party assault floor, an issue fuelled by the platform’s delay in refreshing cyber threat checks, which normally takes about one week.
“Looks as if there may be some false positives. Additionally, restricted particulars on threat particulars.”
– Gartner assessment (read review)
“Based on third-party suggestions, sadly, it provides many false positives.”
– G2 assessment (read review)
3. Bitsight
Efficiency In opposition to Key TPRM Options
Under is an outline of how BitSight performs towards the seven key options of a super Third-Get together Danger Administration device.
(i). Third-Get together Danger Identification
On the BitSight platform, a number of third-party threat identification processes work collectively to supply a complete profile of third-risk publicity.
- Compliance Monitoring – BitSight robotically identifies dangers related to alignment gaps towards laws and cyber frameworks, together with NIS 2 and SOC 2.
- Safety Scores – Like UpGuard and SecurityScorecard, BitSight tracks third-party cybersecurity efficiency with safety scores.
- Exterior Assault Floor Administration – BitSight screens for rising cyber threats throughout the exterior assault floor by referencing a number of threat sources, together with cloud, geographies, subsidiaries, and the distant workforce.
BitSight’s assault floor monitoring characteristic can uncover cases of Shadow IT, one of the vital difficult cyber dangers to trace and handle within the office.
See how UpGuard compares with BitSight >
(ii). Third-Get together Danger Evaluation
BitSight pulls collectively perception from a number of risk sources to create an informative snapshot of a company’s full cyber threat profile. The ensuing dashboard, referred to as The BitSight Safety Score Snapshot, supplies safety groups and stakeholders with a single-pane-of-glass view of the corporate’s total cybersecurity efficiency. Among the metrics tracked in these dashboards embrace:
- Ransomware incident susceptibility
- Knowledge breach susceptibility
- Safety posture efficiency over time (for inside and exterior entities)
- Safety posture benchmarking towards trade requirements

The BitSight Safety Score Snapshot will be remodeled right into a customizable govt report for stakeholders.
(iii). Third-Get together Danger Administration
BitSight presents options supporting the whole Third-Get together Danger Administration workflow, from onboarding to threat administration and govt reporting for maintaining stakeholders knowledgeable of TPRM efforts.

(iv). Third-Get together Danger Monitoring
BitSight’s capacity to trace remediated third-party dangers is an space of concern. Based on unbiased person critiques, addressed cyber dangers take far too lengthy to be acknowledged by the platform, with some taking as much as 60 days to be faraway from stories.
“The time for us to remediate is quite a bit faster, and I do not imagine we must always have to attend the 60 days it takes for them to take away it from the report. The response again from assist on a few of the points we face could be very canned and doesn’t actually present perception.”
– Gartner assessment (read review)
“Configuration points which are fastened keep on report for 60 days, and I’ve not decided that the product acknowledges that the problem is resolved by altering standing in any means.”
– Gartner assessment (read review)
(v). TPRM Course of Automation
BitSight presents integrations with different GRC and Vendor Danger Administration options to streamline processes supporting TPRM efforts.
A few of BitSight’s VRM or GRC integration companions embrace:
Key TPRM answer Efficiency Metrics
Under is an outline of how BitSight measures towards the three major metrics of exemplary TPRM product efficiency.
(i). Consumer Friendliness
The BitSight platform could require an funding of time earlier than a assured grasp of its options is achieved. A sign of a TPRM product’s intuitiveness is whether or not customers require extra studying assets to know how you can use the platform.
The extra intuitive a TPRM device is, the quicker you possibly can leverage returns from its funding.
An excellent TPRM device is so intuitive, customers can naturally settle right into a TPRM workflow with out having to reference complete coaching movies.
“Coaching is missing. No movies.”
– 2023 Gartner assessment (read review)
(ii). Buyer Assist
BitSight has a great popularity for prime requirements of buyer assist.
“Customer support was glorious, the whole lot was defined properly, all my questions have been answered soundly.”
– G2 assessment (read review)
(iii). Danger Scoring Accuracy
BitSight’s third-party threat scoring accuracy is significantly impacted by the extreme period of time required to acknowledge remediated cyber dangers on the platform. Such delays current safety groups with an inaccurate depiction of the state of an organization’s third-party assault floor, which may considerably disrupt the effectivity of a TPRM program.







