The pattern of world knowledge breach occasions is steep and nonetheless persevering with to tilt upwards. Mitigating these occasions includes complete administration of your complete assault floor, together with the third, and even fourth-party vendor community.
Whereas the proliferation of cybercrime is forcing organizations to enhance their cybersecurity applications, many are nonetheless overlooking one of many main causes of knowledge breaches – knowledge leaks.
To be taught the frequent causes of those important safety occasions, and the way to mitigate knowledge breaches by addressing them, learn on.
What’s a Information Leak?
A data leak is an ignored publicity of sensitive data. These exposures might happen bodily – like a post-it observe containing login data – or, extra generally, electronically – via software program vulnerabilities.
When cybercriminals uncover knowledge leaks, they may use the data to launch a profitable cyberattack – particularly if the uncovered knowledge incorporates Personal Identifiable Information (PII).
What is the Distinction Between a Information Leak and a Information Breach
Information leaks will not be initiated by cybercriminals. They fall via ignored vulnerabilities and stay unknowingly uncovered to the general public. These exposures might stay for years earlier than they’re ultimately found by both cybercriminals or safety groups.
Information breaches, alternatively, are totally brought on by cybercriminals. They’re the meant aims of deliberate cyberattacks.

When delicate knowledge is stolen from both an information breach or a ransomware assault and revealed on the darkish net, these occasions are additionally categorized as knowledge leaks.
Learn how to defend against ransomware attacks >
Although they’ve totally different origins, each knowledge leaks and knowledge breaches might consequence within the compromise of delicate knowledge. Information leaks often happen earlier than knowledge breaches and supply cybercriminals with the required ammunition to make cyberattacks occur a lot sooner.
However not all knowledge leaks turn into knowledge breaches. Some occasions might facilitate the deployment of ransomware assaults (which could be classified as data breaches).
The 6 Most Frequent Causes of Information Leaks in 2023
As a result of knowledge leaks make knowledge breaches doable, there is a tight relationship between the causes of each occasions, so the checklist under might delineate the origins of both knowledge breaches or knowledge leaks.
To intensify the effectiveness of knowledge breach prevention efforts, information security applications ought to choice a data leak detection perspective when monitoring assault surfaces. This may naturally uncover and tackle the safety points fuelling each cyber threats.
Managing vulnerabilities with purely an information breach prevention mindset narrows the sector of risk detection, furthering the neglect of important knowledge leaks.

The next occasions are a number of the main causes of knowledge leaks in 2021.
1. Misconfigured Software program Settings
Misconfigured software program settings might expose delicate buyer information. If the leaking software program is widespread, thousands and thousands of customers might then be uncovered to potential cyberattacks.
This was the reason for the Microsoft Power Apps data leak in 2021.
UpGuard initially found the info leak on Might 24, 2021. By default, a important consumer knowledge entry setting was set to ‘off’, exposing no less than 38 million information together with:
- Worker data
- COVID-19 vaccination knowledge
- COVID-19 contact tracing knowledge
By informing Microsoft of its publicity in a well timed method, UpGuard researchers initiated a fast remediation response earlier than the info leaks had been found by cybercriminals. Had this not occurred, thousands and thousands of customers and companies might have fallen sufferer to a widespread cyberattack.
This monumental discovery demonstrates the catastrophic potential of ignored knowledge leaks.
In response to Verizon’s 2020 data breach report, software program misconfiguration, reminiscent of those who precipitated the Microsoft Energy Apps publicity and the 2021 Facebook breach, are on the rise.

Learn how to reduce data leak false positives.
2. Social Engineering
Information leaks are hardly ever initiated by cybercriminals, however when they’re, it is often a results of tactical trickery through social engineering.
Social engineering is using psychological manipulation with a purpose to garnish delicate credentials from victims. Phishing is the commonest kind of social engineering assault, occurring both verbally or electronically.
An instance of a verbal phishing rip-off is a risk actor calling an worker whereas impersonating an IT technician. The risk actor might request login credentials below the pretence of reinforcing entry in response to a important inside difficulty.
When coupled with provocations to mirror a way of firm urgency, the efficiency will appear very plausible to an uneducated sufferer
Experian suffered a data breach impacting 800,000 companies from a verbal social engineering assault. A cybercriminal posing as considered one of Experian’s shoppers requested companies from the corporate, which ultimately resulted within the launch of delicate buyer knowledge.
After private knowledge is relinquished, hackers might then use the info leak to breach an IT perimeter and full the preliminary section of a cyberattack sequence.

As a result of unsuspecting staff are so simply tricked, any kind of knowledge that would broaden the checklist of potential victims is a big risk to knowledge safety. This contains seemingly innocuous data, reminiscent of cellphone numbers and social safety numbers.
Digital phishing assaults are extra proliferative since they’ll attain a bigger checklist of victims a lot sooner. The most well-liked type of social engineering is e mail phishing.
Phishing emails pose as respectable communications from dependable sources, however their contents include contaminated hyperlinks. When a consumer clicks on a phishing e mail hyperlink, they may both provoke the clandestine set up of malware or load a dummy net web page designed to steal knowledge.
Phishing emails have gotten more and more subtle and more durable to detect, particularly once they reap the benefits of recipient anxieties.
A sudden enhance of such immoral practices shadowed the COVID-19 pandemic. Phishing emails detailing faux security data had been despatched to victims, some even claiming to be from authorities companies and widespread healthcare entities.
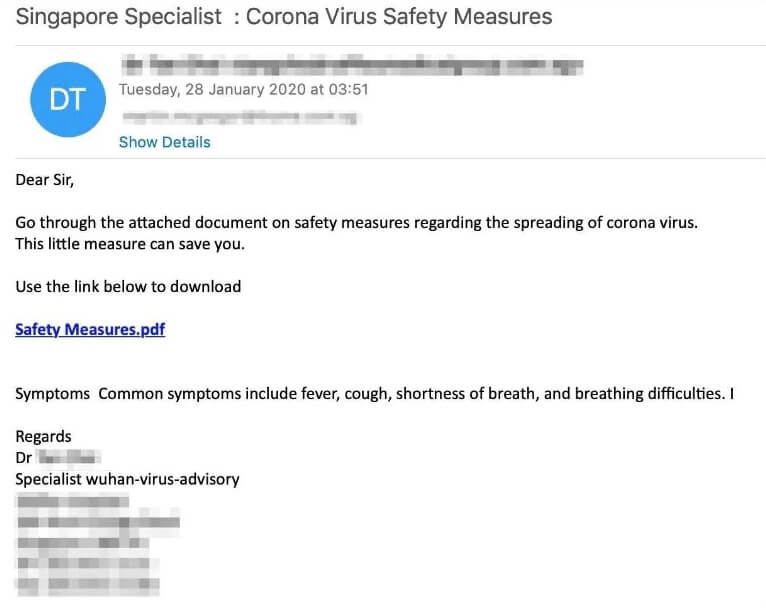
The plausible designs of those emails, coupled with the lowered skepticism fuelled by hopeful yearnings, resulted in a very high number of data breaches.
3. Recycled Passwords
In lots of instances, a single compromised password results in the compromise of a number of digital options as a result of customers have a tendency to make use of the identical password throughout all of their logins.
This poor safety observe creates a important knowledge leak as a result of stolen buyer knowledge is often bought through dark web forums.
You’ll be able to verify whether or not your emails, passwords, or cellphone numbers had been compromised in historic knowledge breaches by visiting Have I Been Pwned.
Should you’re an iPhone consumer, iOS 14’s Security Recommendations feature enables you to check if you’re reusing passwords so you possibly can change them instantly.
Even partial password data is categorized as an information leak as a result of the remaining portion may very well be uncovered via brute drive strategies.
Throughout a brute force attack, a number of username and password combos are tried with automation instruments till a match is achieved.
Having partial password data decreases the variety of required makes an attempt, serving to cybercriminals obtain success a lot sooner.
4. Bodily Theft of Delicate Gadgets
Firm units include delicate data, and when these units fall into the incorrect fingers, they are often leveraged to facilitate safety breaches, or identity theft, resulting in knowledge breaches.
For instance, a cybercriminal might contact the IT administrator from a stolen laptop computer and declare that they’ve forgotten their login data. With the suitable persuasive ways, the IT administrator will reveal this data, serving to the cybercriminal remotely log into the corporate’s personal community.
In such a situation, the compromised laptop computer is the attack vector, exposing knowledge leaks connecting the compromised worker to the corporate’s IT administrator.
5. Software program Vulnerabilities
Software program vulnerabilities, like zero-day exploits, create handy pathways into delicate assets. This circumvents the preliminary stage of the cyberattack lifecycle, propelling criminals via to the privilege escalation section of an assault lifecycle – the one remaining stage earlier than an information breach.
As soon as exploited, these exposures might result in quite a few safety incidents, together with unauthorized entry, malware assaults, social media account compromise, and even bank card theft (see the Equifax data breach).
6. Use of Default Passwords
Lots of the factory-standard login credentials that accompany new units are publically identified, even to cybercriminals. Due to this, unchanged factory-standard credentials are categorized as knowledge leaks.
IoT (internet of things) units are most impacted by such exposures. When bought, these units include normal login combos to help fast setup.
Frequent username and password combos embrace “admin” or “12345.”
Producer directions often embrace a daring warning to alter these credentials prior to make use of, however, sadly, they’re seldom adopted – a nasty behavior of each small companies and enormous enterprises.
As a result of IoT units are often networked collectively, these knowledge leaks might facilitate a large-scale DDoS attack.
That is precisely what occurred in 2016. One of the largest DDoS attacks ever documented was launched towards the cybersecurity weblog Kerbs on Safety.
The botnet that executed the assault comprised of 380,000 IoT units that had been seamlessly hacked via their default passwords.
How Do I Stop Information Leaks?
To prevent data leaks, cybersecurity applications should embrace an information safety technique. Not solely will this help consumer knowledge safety compliance with regulatory requirements, reminiscent of the GDPR, it should additionally regulate incident response plans to incorporate an information leak remediation technique.
The next finest practices might mitigate knowledge leaks and the info breaches they make doable.
1. Simplify Entry Permissions
This should not be confused with forsaking Privileged Access Management. Privileged entry administration is important for cybersecurity, the workflow that manages the entry ranges of every consumer must be simplified.
Advanced entry permission workflows make it troublesome to trace every consumer’s entry degree, making it very straightforward to by accident grant a consumer deeper entry than they require.
Audit every consumer’s entry ranges to make sure that solely those who completely require it have entry to delicate assets.
After that is full, run your consumer entry workflow via a really advantageous filter to eradicate pointless complexities.
2. Educate Employees
A knowledge leak prevention technique ought to embrace a main give attention to probably the most important safety risk to a company – human error.
To forestall employees from falling for frequent social engineering ways, they need to be skilled on the way to precisely acknowledge when an assault is happening.
The perfect type of coaching is expertise. Set up a coaching program the place employees are routinely focused with managed social engineering assaults delivered by your safety staff.
“Failing” a check creates a really impactful and teachable second that can be remembered for a few years.
3. Use Multi-Issue Authentication
Ought to an worker nonetheless fall for cybercriminal trickery after coaching, compromise might nonetheless be averted with multi-factor authentication.
Multi-factor authentication creates an extra hurdle that would trigger staff to rethink their actions throughout a social engineering assault.
This may very well be sufficient to reset a manipulated mindset and encourage employees to hunt verification from inside safety groups.
3. Encrypt All Information
If knowledge is by accident leaked, it might have little use to cybercriminals whether it is successfully encrypted.
Be sure you use probably the most safe types of encryption reminiscent of AES encryption and PGP encryption.
4. Use a Password Supervisor
Default passwords are used as a result of companies have too many passwords to recollect. A password supervisor conveniently shops all passwords in a single platform. It additionally creates extremely advanced password solutions for every new login, stopping using recycled passwords.
5. Implement a Information Leak Detection Resolution
Every of the above methods encourages finest practices that would keep away from knowledge exposures, however they fail to detect the advanced knowledge leaks which may nonetheless fall via superior safety loopholes.
To tie off an information leak prevention technique, finest practices ought to be accompanied by a data leak detection solution.
Data leak detection options scan each the floor and the darkish net to find knowledge leaks inside cybercriminal interactions. These options can both be absolutely automated or supported by cybersecurity analysts.
The caveat of a fully-automated knowledge leak resolution is that, in lots of cases, these discoveries are false positives that can be ignored. Including an inside knowledge leak filtering technique will solely overwhelm the already restricted bandwidth of safety groups, distracting them from critical security tasks requiring immediate attention.
To keep away from this, an information leak resolution ought to be supported by cybersecurity analysts that manually consider and filter out knowledge leak false positives on behalf of the sufferer.
UpGuard affords a managed knowledge leak detection service had been all found inside and third-party leaks are analysed by cybersecurity specialists to take away false positives, earlier than being categorized as safety threats.
Watch the video under for an summary of UpGuard’s knowledge leak detection options.
For extra knowledge leak detection and prevention steering, consult with the next assets:







