
ConnectWise warned clients to patch their ScreenConnect servers instantly in opposition to a most severity flaw that can be utilized in distant code execution (RCE) assaults.
This safety bug is because of an authentication bypass weak point that attackers can exploit to realize entry to confidential knowledge or execute arbitrary code remotely on susceptible servers in low-complexity assaults that do not require person interplay.
The corporate additionally patched a path traversal vulnerability in its distant desktop software program, which may solely be abused by attackers with excessive privileges.
“Vulnerabilities have been reported February 13, 2024, by our vulnerability disclosure channel through the ConnectWise Belief Middle,” ConnectWise warned.
“There isn’t any proof that these vulnerabilities have been exploited within the wild, however rapid motion should be taken by on-premise companions to handle these recognized safety dangers.”
ConnectWise has but to assign CVE IDs to the 2 safety flaws that impression all servers working ScreenConnect 23.9.7 and prior.
Whereas ScreenConnect cloud servers hosted on screenconnect.com cloud or hostedrmm.com are already secured in opposition to potential assaults, admins utilizing on-premise software program are suggested to update their servers to ScreenConnect model 23.9.8 instantly.
Huntress safety researchers reported earlier at this time that they’ve already created a proof-of-concept (PoC) exploit that can be utilized to bypass authentication on unpatched ScreenConnect servers.
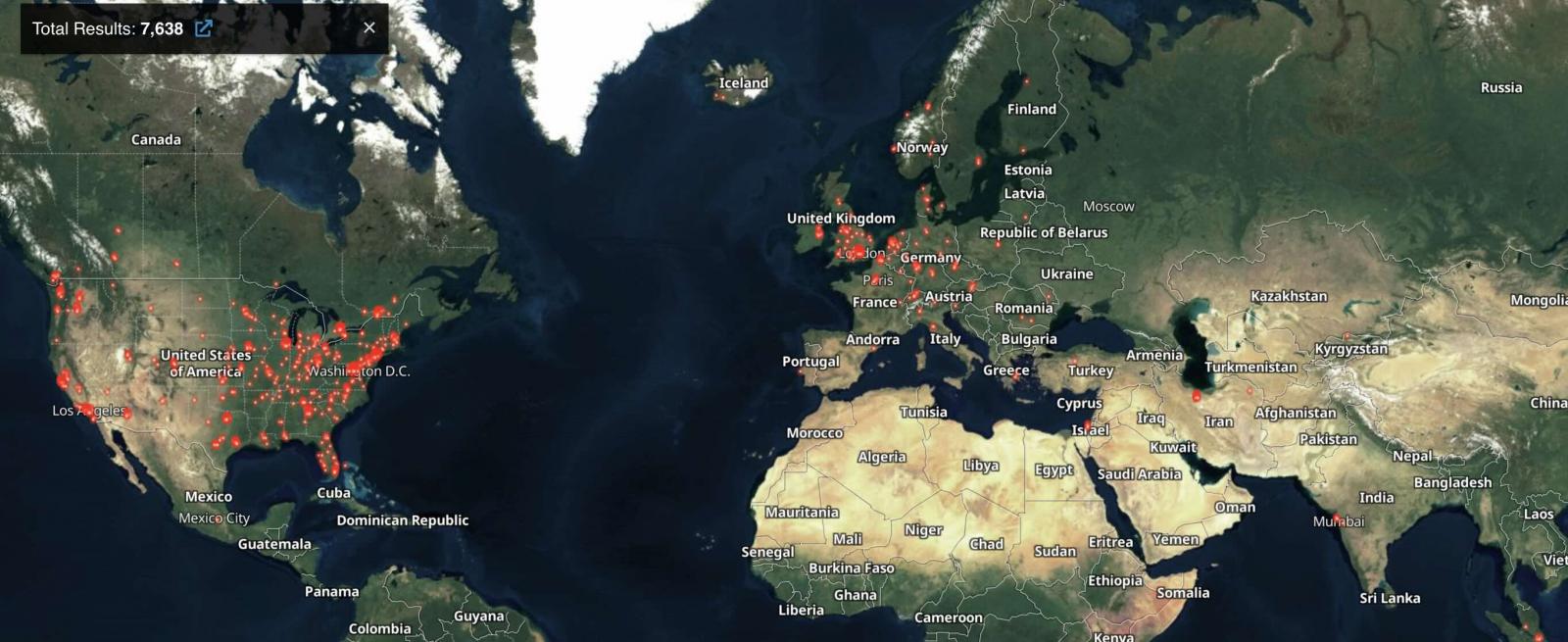
Huntress added {that a} search on the Censys publicity administration platform allowed them to seek out greater than 8,800 servers susceptible to assaults.
Shodan additionally tracks over 7,600 ScreenConnect servers, with solely 160 at present working the patched ScreenConnect 23.9.8 version.
Final month, CISA, the NSA, and MS-ISAC issued a joint advisory warning that attackers more and more use respectable distant monitoring and administration (RMM) software program reminiscent of ConnectWise ScreenConnect for malicious functions.
Through the use of distant desktop software program as an entry level into their targets’ networks, risk actors can entry their programs as native customers with out requiring admin permissions or new full software program installations.
This permits them to bypass safety controls and acquire entry to different gadgets on the community by benefiting from the compromised person’s permissions.
Attackers have been utilizing ScreenConnect for malicious functions for years, together with stealing knowledge and deploying ransomware payloads throughout victims’ breached programs.
Extra lately, Huntress additionally noticed risk actors utilizing native ScreenConnect situations for persistent access to hacked networks.







