
The alleged supply code for the third iteration of the Knight ransomware is being provided on the market to a single purchaser on a hacker discussion board by a consultant of the operation.
Knight ransomware launched on the finish of July 2023 as a re-brand of the Cyclops operation, focusing on Home windows, macOS, and Linux/ESXi techniques.
It gained some traction as a result of it offered info-stealers and a ‘lite’ version of its encryptor for lower-tier associates that attacked smaller organizations.
Menace analysts at cyber-intelligence agency KELA noticed the commercial two days in the past posted on RAMP forums by somebody utilizing the alias Cyclops, often known as a consultant of the Knight ransomware gang.
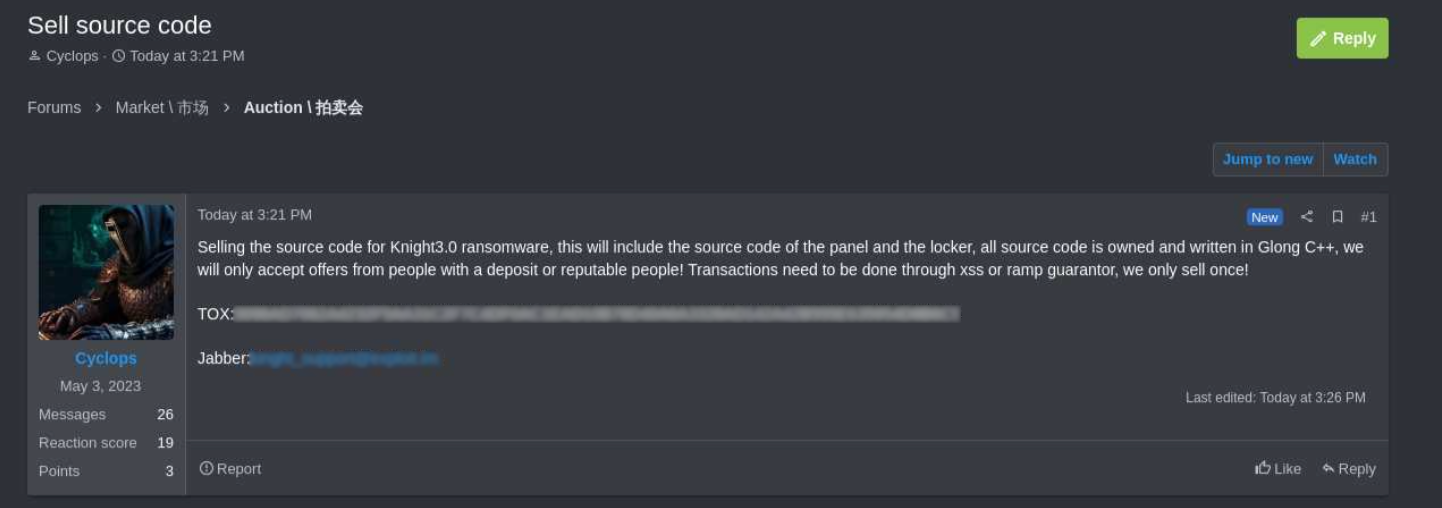
“Promoting the supply code for Knight 3.0 ransomware, this may embody the supply code of the panel and the locker, all supply code is owned and written in Glong C++,” says Cyclops within the submit.
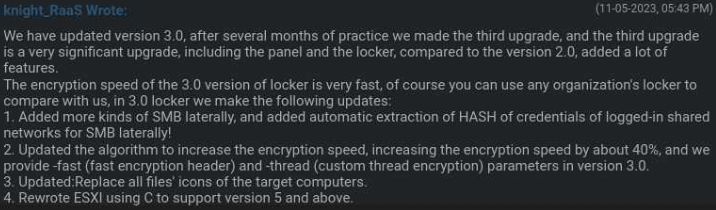
Model 3.0 of Knight’s locker was launched on November 5, 2023, with 40% sooner encryption, a re-written ESXi module so as to add help for newer variations of the hypervisor, and numerous different enhancements.
The menace actor didn’t specify a value however emphasised that the supply code would solely be offered to a single purchaser, preserving its worth as a personal instrument.
Cyclops stated they might prioritize respected customers with a deposit and that the acquisition can be carried out by way of a transaction guarantor both on RAMP or XSS hacker discussion board.
The vendor has posted contact addresses for Jabber and TOX messaging companies for potential consumers to succeed in out and negotiate a remaining deal.
KELA advised BleepingComputer that the Jabber is new however the TOX ID listed on the discussion board submit is understood and beforehand related to Knight, which provides legitimacy to the sale.
The explanation behind promoting the supply code for Knight ransomware stays unclear however KELA’s darkish internet monitoring instruments have logged no actions from Knight’s representatives on numerous boards since December 2023.
Additionally, the ransomware operation’s sufferer extortion portal is at the moment offline, the final sufferer being listed on February 8. Since July 2023, Knight claimed to have breached 50 organizations.
Primarily based on the small print from KELA, the Knight ransomware operation seems to have gone inactive for some time now, so it’s potential that the group is trying to shut store and promote their property.







