Menace actors are exploiting a CMS editor discontinued 14 years in the past to compromise schooling and authorities entities worldwide to poison search outcomes with malicious websites or scams.
Open redirects are when web sites, whether or not deliberately or by way of a flaw, permit arbitrary redirection requests that take customers from the unique website to an exterior URL with out ample validation or safety checks.
For instance, if there was a URL at https://www.instance.com/?redirect=<url> that redirects guests to the required URL, and anybody might modify that URL to a website of their selecting, it will be thought of an open redirect.
Attackers abuse these open redirects to carry out phishing assaults, distribute malware, or rip-off customers whereas showing to originate from official domains. Because the URLs are hosted on trusted domains, it might permit them to bypass URL filters utilized by safety merchandise.
Moreover, search engine crawlers index the redirects and record them on Google Search results, making them an efficient technique for search engine marketing poisoning campaigns, leveraging a trusted area to rank malicious URLs larger for particular queries.
As a result of open redirect URLs don’t host the malicious content material immediately however merely level to it, they will stay energetic and visual in search outcomes for a very long time till they’re reported for takedown.
Nonetheless, many firms, together with Google and Microsoft, don’t contemplate open redirects a flaw and should not repair them until they result in a extra extreme vulnerability.
Concentrating on outdated plugin
Cybersecurity researcher @g0njxa found the malicious redirect marketing campaign after seeing Google Search outcomes for ‘Free V Bucks’ (Fortnite in-game forex) turbines hosted on college websites.
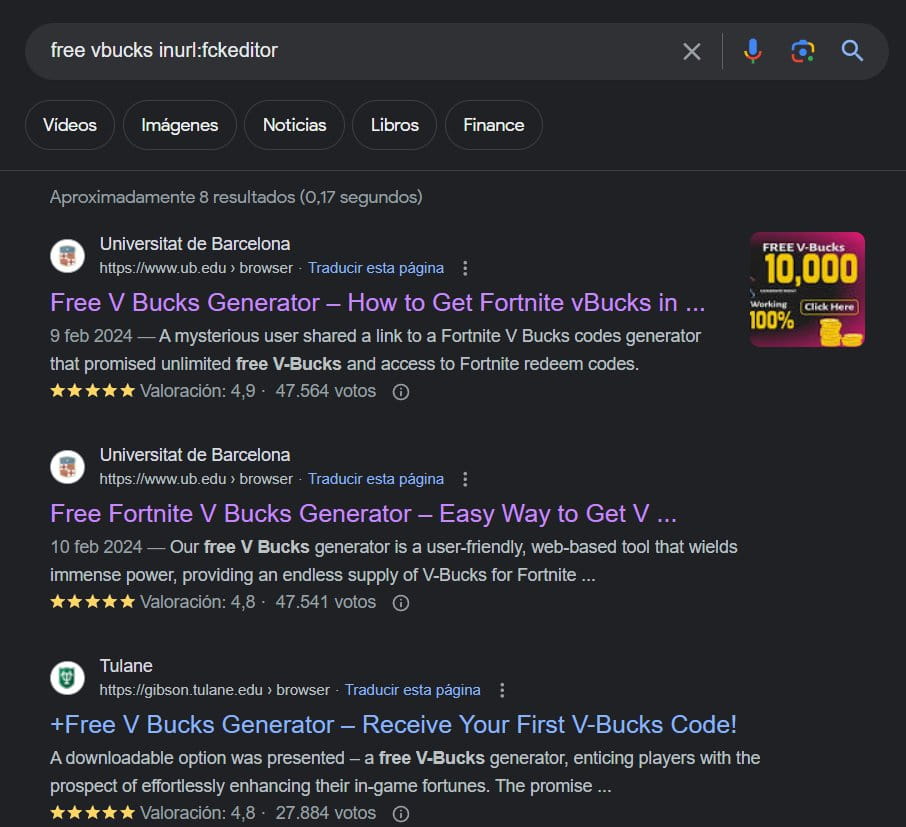
The open redirect requests utilized by the attackers on this marketing campaign are associated to FCKeditor, a once-popular net textual content editor that permits customers to edit HTML content material immediately inside an internet web page.
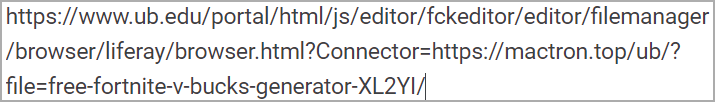
In 2009, FCKeditor was rebranded and considerably revamped, ensuing within the launch of CKEditor, which makes use of a extra trendy codebase, affords enhanced usability and compatibility with up to date net requirements, and can be actively supported by its developer.
In a Twitter thread, g0njxa lists the varied organizations focused by this marketing campaign, primarily focusing on academic establishments, reminiscent of MIT, Columbia College, Universitat de Barcelona, Auburn College, College of Washington, Purdue, Tulane, Universidad Central del Ecuador, and the College of Hawaiʻi.
Nonetheless, the marketing campaign additionally targets authorities and company websites utilizing the outdated FCKeditor plugin, together with Virginia’s authorities website, Austin, Texas’s authorities website, Spain’s authorities website, and Yellow Pages Canada.
From BleepingComputer’s checks, we found that the compromised FCKeditor cases make the most of a mixture of static HTML pages and redirects to malicious websites.
The static HTML pages open underneath the official area and are used to poison the search engine with malicious outcomes.
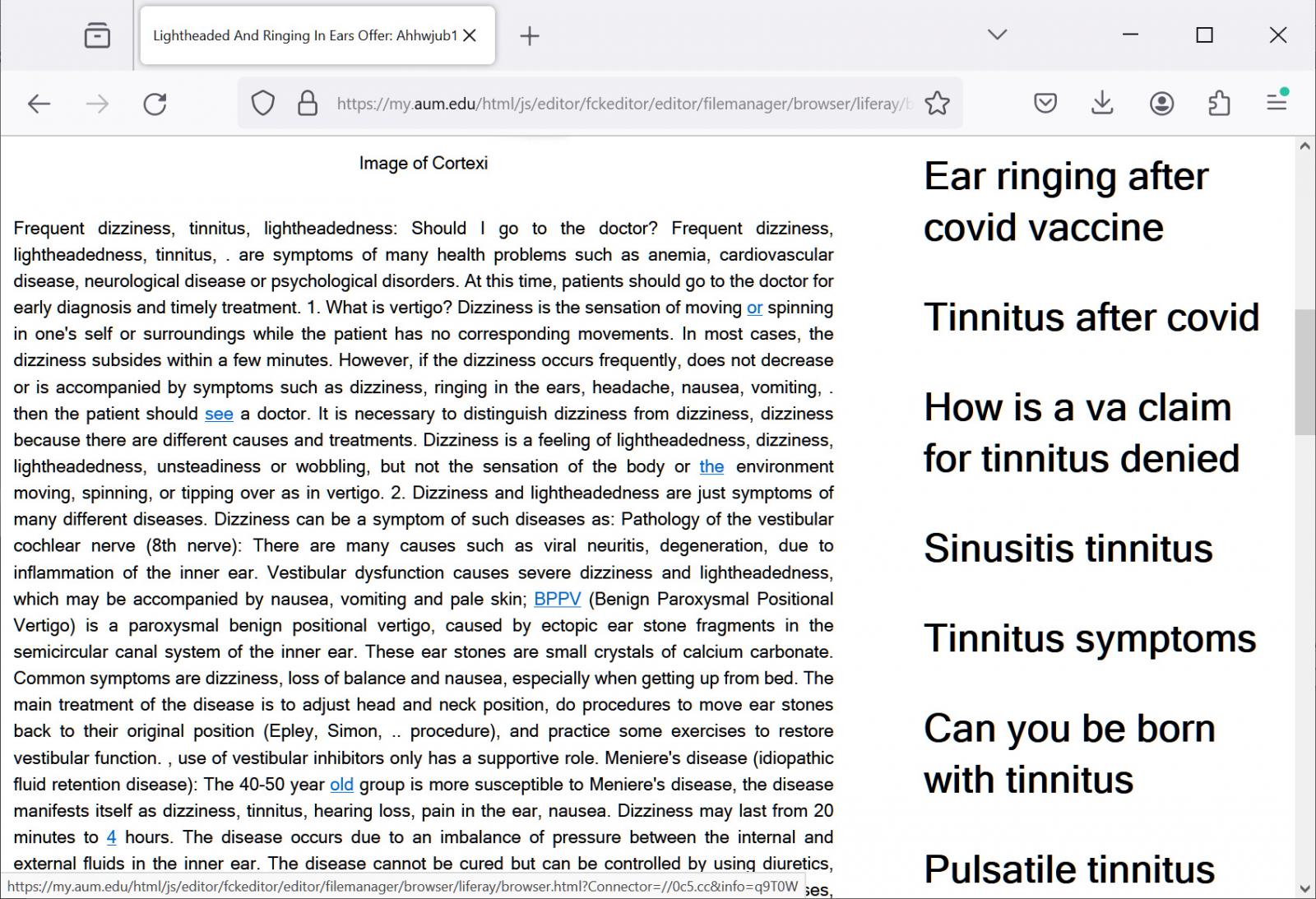
For instance, one of many hyperlinks in Google goes to the FCKeditor occasion on the aum.edu website, the place an HTML web page pretends to be a information article about tinnitus cures.
Nonetheless, the article is designed to advertise different content material pages on the compromised FCKeditor occasion put in on AUM’s web site in order that Google will index the pages. As soon as these pages are ranked in search engines like google, the risk actors will possible swap them out for redirects to malicious websites.
Supply: BleepingComputer
Different URLs on this marketing campaign will merely abuse FCKeditor to redirect guests to rip-off websites, faux information articles, phishing pages, hacking help websites, or malicious browser extensions.
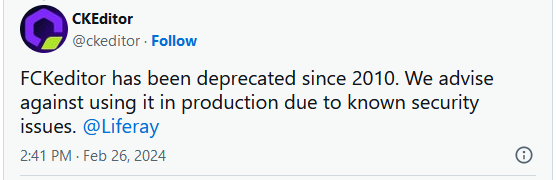
The software program maker responded to the open redirects marketing campaign report on X, saying that FCKeditor has been deprecated since 2010 and no person ought to be utilizing it anymore.
Sadly, it is not unusual to see college and authorities websites utilizing software program that has been discontinued for a very long time, on this case, over 13 years.
Previously, we noticed related campaigns the place risk actors abused open redirects on authorities websites to redirect customers to fake OnlyFans and adult sites.