
A straightforward phishing assault utilizing a Flipper Zero machine can result in compromising Tesla accounts, unlocking automobiles, and beginning them. The assault works on the newest Tesla app, model 4.30.6, and Tesla software program model 11.1 2024.2.7.
Safety researchers Talal Haj Bakry and Tommy Mysk reported their discovering to Tesla saying that linking a automotive to a brand new cellphone lacks correct authentication safety. The automotive maker decided the report back to be out of scope.
Phishing assault
An attacker at a Tesla supercharger station may deploy a WiFi community known as”Tesla Visitor,” an SSID that’s generally discovered at Tesla service facilities and automotive house owners are aware of it.
Mysk used a Flipper Zero to broadcast the WiFi community however notes that the identical might be achieved utilizing a Raspberry Pi or different units that include WiFi hotspot capabilities.
As soon as the sufferer connects to the spoofed community, they’re served a pretend Tesla login web page asking to log in utilizing their Tesla account credentials. Regardless of the sufferer enters on the phishing web page, the attacker can see on the Flipper Zero in actual time.
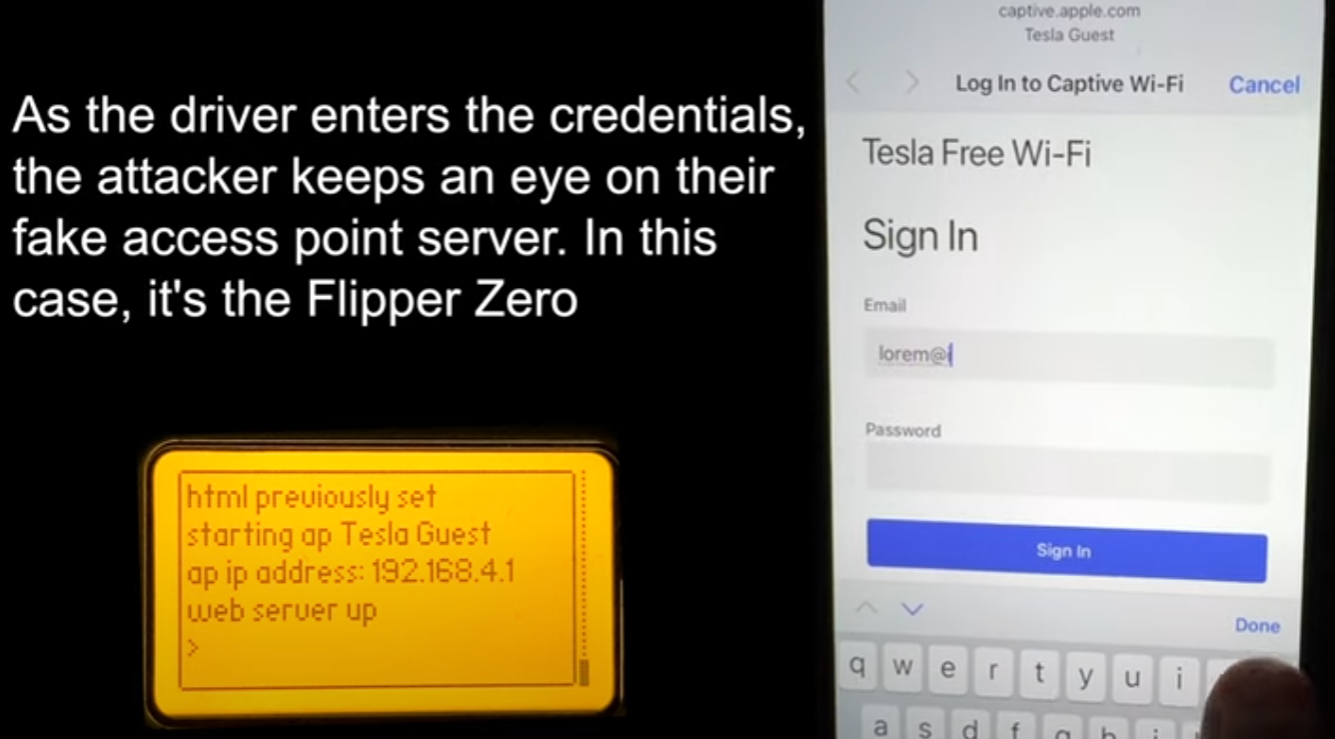
After getting into the Tesla account credentials, the phishing web page requests the one-time password for the account, to assist the attacker bypass the two-factor authentication safety.
The attacker has to maneuver earlier than the OTP expires and log into the Tesla app utilizing the stolen credentials. As soon as within the account, the risk actor can monitor the car’s location in actual time.
Including a brand new key
Entry to the sufferer’s Tesla account permits the attacker so as to add a brand new ‘Telephone Key.’ For this, they should be in shut proximity of the automotive, just some meters away.
Telephone Keys use Tesla’s cellular app together with the automotive proprietor’s smartphone to permit locking and unlocking the car robotically, over a safe Bluetooth connection.
Tesla automobiles additionally use Card Keys, that are slim RFID playing cards that should be positioned on the middle console’s RFID reader to begin the car. Though safer, Tesla treats them as a backup choice if the Telephone Secret is unavailable or out of battery.
Mysk says that including a brand new Telephone Key by the app doesn’t require the automotive to be unlocked or the smartphone to be contained in the car, which makes for vital safety hole.
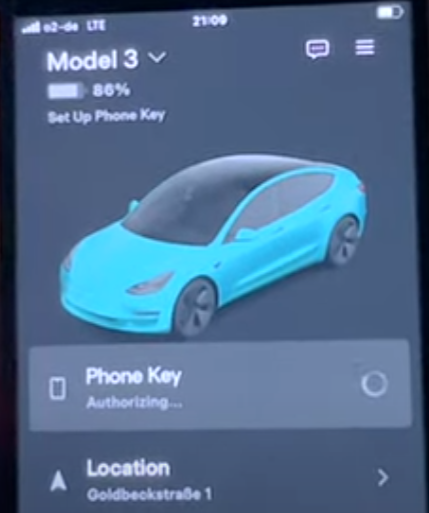
To make issues worse, as soon as a brand new Telephone Secret is added, the Tesla proprietor doesn’t obtain a notification in regards to the truth by the app, and no alert is proven on the automotive’s touchscreen.
With the brand new Telephone Key, the attacker can unlock the automotive and activate all its methods, permitting them to drive away as in the event that they had been the proprietor.
Mysk notes that the assault is profitable on a Tesla Mannequin 3. Within the report back to the automotive firm, the researcher notes that the hijacked Tesla account should belong to the principle driver and that the car should already be linked to a Telephone Key.
The researchers argue that requiring a bodily Tesla Card Key when including a brand new Telephone Key would enhance safety by including an authentication layer for the brand new cellphone.
“I used to be ready so as to add a second cellphone key on a brand new iPhone with out the Tesla app prompting me to make use of a key card to authenticate the session on the brand new iPhone. I solely signed in on the brand new iPhone with my username and password, and as quickly as I granted the app entry to the placement providers, it activated the cellphone key,” Tommy Mysk and Talal Haj Bakry wrote within the report back to Tesla.
The corporate replied by saying that its investigation decided that it was the meant habits and that the Tesla Mannequin 3 proprietor’s handbook doesn’t state {that a} key card is required so as to add a cellphone key.
BleepingComputer has contacted Tesla with questions on the above and whether or not they plan to challenge an OTA replace that introduces safety measures to forestall these assaults, however we’ve not heard again but.







