
A brand new large-scale StrelaStealer malware marketing campaign has impacted over 100 organizations throughout america and Europe, making an attempt to steal e-mail account credentials.
StrelaStealer was first documented in November 2022 as a brand new information-stealing malware that steals e-mail account credentials from Outlook and Thunderbird.
One notable attribute of the malware was utilizing a polyglot file an infection technique to evade detection from safety software program.
On the time, StrelaStealer was seen concentrating on predominately Spanish-speaking customers. Nonetheless, in line with a current report by Palo Alto Networks’ Unit42, this has modified because the malware now targets folks from the U.S. and Europe.
StrelaStealer is distributed by phishing campaigns that confirmed a big uptick in November 2023, some days concentrating on over 250 organizations within the U.S.
The elevated phishing e-mail distribution volumes continued into 2024, with a big wave of exercise being recorded by Unit42 analysts between late January and early February 2024.
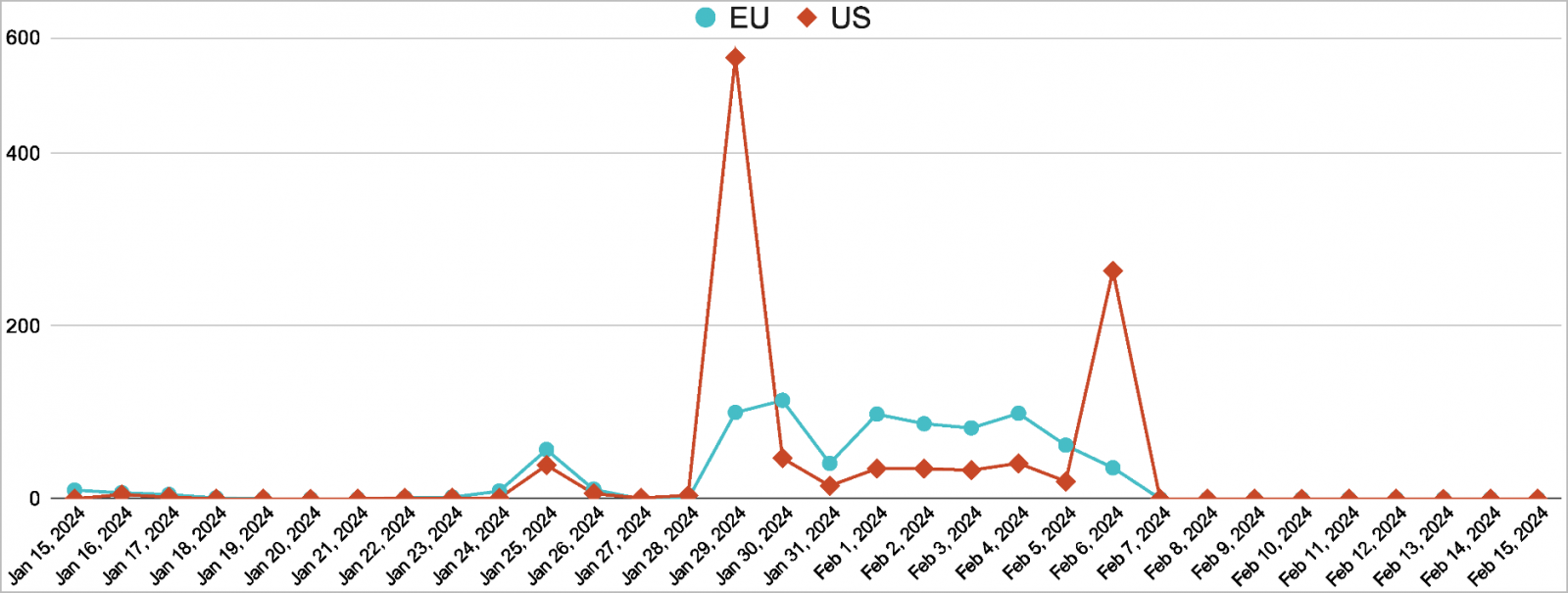
In some days throughout that interval, the assaults within the U.S. surpassed 500, whereas Unit42 says it has confirmed at the very least 100 compromises within the nation in addition to Europe.
The malware operators used English and different European languages to regulate their assaults as wanted.
.png)
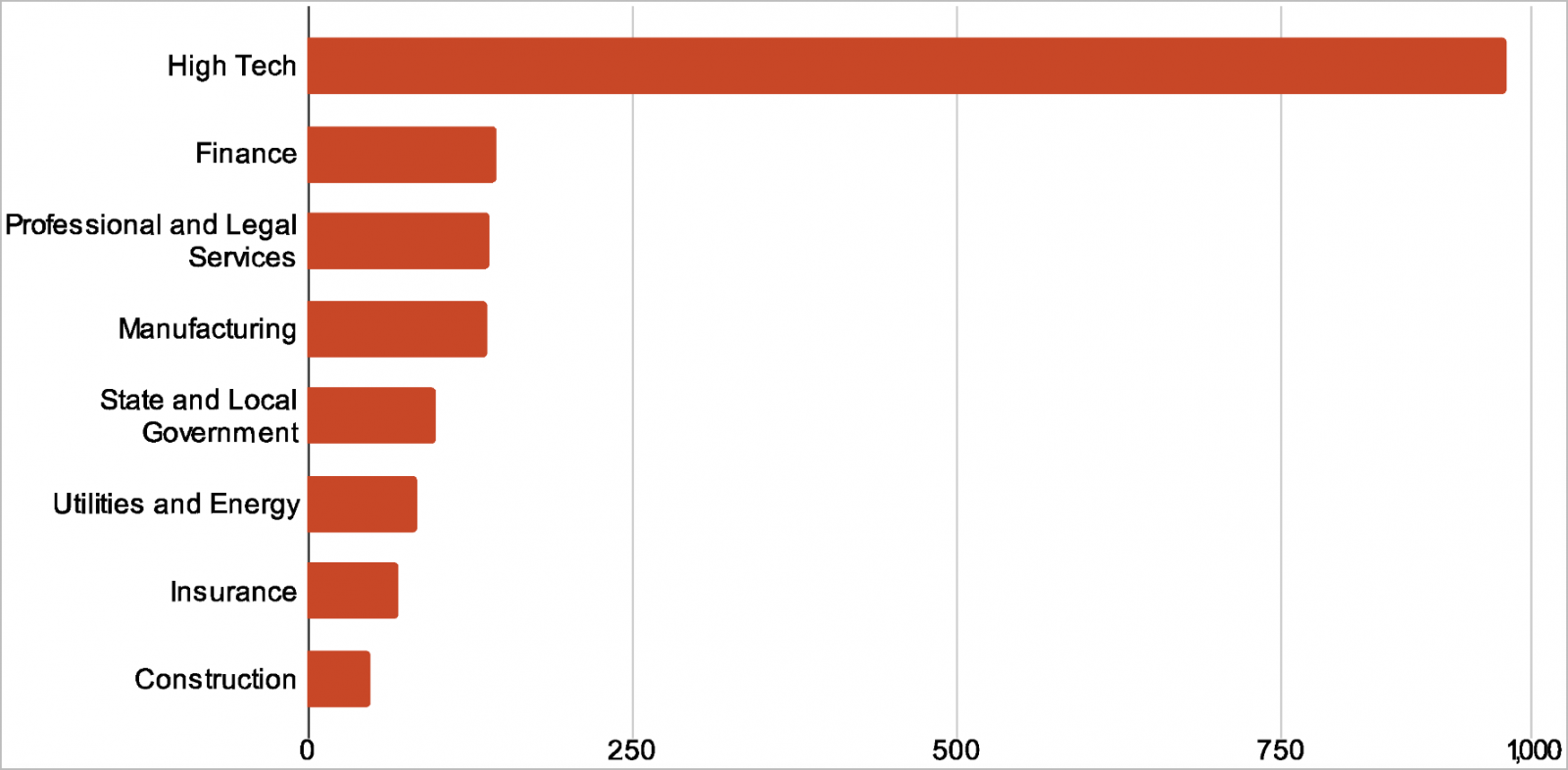
Most focused entities function within the ‘excessive tech’ area, adopted by sectors like finance, authorized companies, manufacturing, authorities, utilities and power, insurance coverage, and building.
New an infection technique
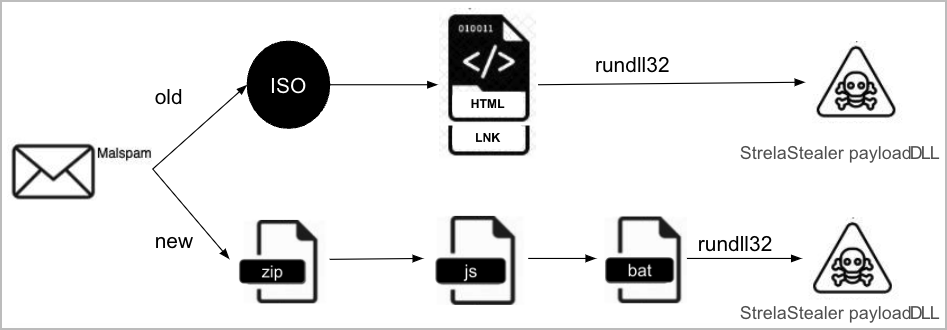
StrelaStealer’s authentic an infection mechanisms from late 2022 have advanced, although the malware nonetheless makes use of malicious emails as the first an infection vector.
Beforehand, the emails hooked up .ISO recordsdata containing a .lnk shortcut and an HTML file, which utilized polyglotism to invoke ‘rundll32.exe’ and execute the malware payload.
The most recent an infection chain makes use of ZIP attachments to drop JScript recordsdata on the sufferer’s system. When executed, the scripts drop a batch file and a base64-encoded file that decodes right into a DLL. That DLL is executed through rundll32.exe once more to deploy the StrelaStealer payload.
Moreover, the most recent model of the malware employs management movement obfuscation in its packing to complicate evaluation and removes PDB strings to evade detection by instruments counting on static signatures.
StrelaStealer’s major operate stays the identical: to steal e-mail login info from common e-mail shoppers and ship it to the attackers’ command and management (C2) server.
Customers ought to train vigilance when receiving unsolicited emails that purport to contain funds or invoices and chorus from downloading attachments from unknown senders.







