The Digital Operational Resilience ACT (DORA) regulation turns into enforceable within the European Union on 17 January 2025. With stress testing on 109 banks already underway by the European Central Financial institution (ECB), the remainder of the EU monetary sector ought to comply with swimsuit to keep away from speeding by means of last-minute compliance efforts.
This text outlines the DORA compliance necessities, together with a helpful guidelines that will help you pave a path to compliance earlier than the deadline.
What’s DORA?
The Digital Operational Resilience ACT, or DORA, is an EU regulation that goals to ascertain digital operational resilience throughout the monetary ecosystem to cut back enterprise disruptions within the occasion of a cyberattack or information breach. DORA enhances present EU cybersecurity laws, such because the GDPR and NIS2 Directive.
Who should adjust to the DORA regulation?
All monetary establishments doing enterprise within the EU member states should adjust to the DORA necessities, together with:
- The Monetary Companies Business
- Cost establishments
- Funding companies
- Insurance coverage firms
- Credit standing businesses
- Crypto-asset service suppliers
- Crowdfunding service suppliers
- Knowledge analytics and audit providers
- Fintech
- Buying and selling venues
- Monetary system suppliers
- Credit score establishments
Third-party vendors who present data and communication expertise (ICT) providers for finance establishments should additionally obtain DORA compliance.
DORA compliance dates
The DORA laws grew to become efficient on 16 January 2023, permitting a 24-month implementation interval for in-scope organizations.
On 17 January 2024, the three European supervisory authorities, the EBA (European Banking Authority), EIOPA (European Insurance coverage and Occupational Pensions Authority), and ESMA (European Securities and Markets Authority), finalized drafted Regulatory Technical Requirements (RTS) outlining ICT threat administration necessities beneath DORA.
Affected establishments have till 17 January 2025 to adjust to DORA necessities.
On 3 January 2024, the European Central Financial institution (ECB) introduced the graduation of digital operational resilience testing throughout 109 banks within the EU.
What are the penalties for DORA non-compliance?
Enforcement of penalties for DORA non-compliance falls within the palms of designated regulators in every EU state, referred to as “competent authorities. Potential penalties for non-compliance embody administrative fines, remedial measures, public reprimands, withdrawal of authorization, and compensation for damages incurred.
In-scope entities that don’t adjust to the DORA are topic to penalty funds of as much as 1% of the common each day worldwide turnover within the previous enterprise yr.
DORA compliance necessities
The DORA regulation consists of 5 key pillars that set out necessities for finance entities to face up to, reply to, and get well from ICT-related threats. Beneath are the 5 pillars of DORA compliance.
1. ICT threat administration
Finance entities are required to ascertain and keep complete ICT risk management frameworks. These frameworks ought to cowl all levels of an ICT system’s lifecycle and embody applicable cybersecurity measures for cyber menace identification, safety, detection, response, and restoration plans throughout the group and all through the availability chain. This pillar additionally mandates continuous testing and monitoring to make sure the continued effectiveness of the applied measures.
2. ICT incident reporting
Corporations should report main ICT-related incidents to their respective regulators promptly. The goal is to allow a greater understanding of the ICT threat panorama throughout the monetary sector and encourage a coordinated response to main incidents.
3. Digital operational resilience testing
DORA mandates that companies conduct common testing to evaluate their capability to face up to numerous sorts of ICT disruptions. This pillar requires in-scope entities to bear routine threat-led penetration testing (TLPT) to simulate cyberattacks and assess their cybersecurity defenses.
4. ICT third-party threat administration
DORA introduces guidelines for managing cyber dangers from outsourcing crucial monetary operations to third-party ICT service suppliers. The regulatory framework stipulates that finance entities should topic ICT third-party service suppliers to correct oversight and due diligence processes. They need to additionally make sure that third-party threat administration processes are in place to cut back the probability of main incidents like information breaches.
5. Data and intelligence sharing
DORA encourages the sharing of cyber threat information and intelligence amongst finance entities. This collaboration goals to boost the sector’s potential to determine, defend in opposition to, reply to, and get well from ICT-related incidents. The regulation supplies an information-sharing framework whereas guaranteeing information safety stays a precedence.
By establishing these pillars, DORA goals to standardize and strengthen the digital operational resilience of the EU’s monetary sector, guaranteeing that it stays strong, aggressive, and able to dealing with the evolving panorama of ICT dangers.
DORA compliance guidelines
The Digital Operational Compliance Act is a complete regulatory framework that requires finance entities to take a structured method to implementation. This guidelines maps out key actions to take to realize DORA compliance sooner.
1. Decide DORA scope
▢ Confer with Article 2 of the DORA laws to find out in case your group is an in-scope entity, i.e., a finance establishment or crucial ICT service supplier to a monetary establishment.
2. Carry out a DORA hole evaluation
▢ Conduct a maturity evaluation in opposition to the DORA compliance necessities to determine gaps throughout all ICT programs.
▢ Assess your ICT third-party threat by conducting vendor risk assessments.
💡 How UpGuard helps
UpGuard provides a free DORA assessment workbook that maps related controls from the NIST CSF and ISO 27001 frameworks to the DORA necessities. The UpGuard platform automates compliance mapping and reporting for these frameworks for you and your distributors.

3. Create a remediation roadmap
▢ Use evaluation findings to determine compliance gaps and create a roadmap of remediation activities.
💡 How UpGuard helps
UpGuard contains automated remediation workflows that allow you to request vendor remediation based mostly on automated scanning and questionnaire responses.
💡Compliance tip: ‘The roadmap ought to embody recognized actions on a yearly timeline (e.g., divided into quarters), based mostly on motion precedence and feasibility.’ – Cindy Ruan, Governance Threat and Compliance Specialist
4. Determine crucial third-party ICT suppliers
▢ Confer with Article 31 of the DORA necessities to grasp which of your third-party ICT suppliers are deemed ‘crucial’ and should additionally comply.
💡 How UpGuard helps
UpGuard helps you discover, observe, and monitor the safety posture of any group immediately. You possibly can categorize distributors, evaluate them in opposition to business benchmarks, and see how their safety posture modifications over time.

5. Implement a threat-led penetration testing (TLPT) framework
As per Article 26 of the DORA regulation, monetary entities should conduct TLPT testing a minimum of each three years.
▢ Use an authorised TLPT framework, equivalent to TIBER-EU.
▢ Guarantee your TLPT framework covers a number of or all crucial capabilities of the monetary entity.
▢ Outline the scope of the TLPT framework and obtain approval of the scope by a reliable authority (as outlined in Article 46 of the DORA).
▢ When ICT third-party service suppliers are deemed in-scope for TLPT testing, take the required measures and safeguards to make sure the service supplier’s participation.
▢ Carry out testing on dwell manufacturing programs.
▢ Guarantee testing is carried out a minimum of each three years, relying on threat portfolio and operational circumstances.
▢ Submit a abstract of related findings, corrective motion plans, and documentation demonstrating that the take a look at meets necessities.
💡 Compliance tip: ‘TLPT is also referred to as Purple Crew Testing or “Purple Teaming” within the business. It’s a managed (and approved) try by moral hackers to compromise an entity’s programs and total cyber resilience by simulating the techniques, strategies, and procedures (TTPs) of real-life menace actors.’ – Cindy Ruan, Governance Threat and Compliance Specialist
6. Develop an incident response plan
Article 17 of the DORA requires monetary entities to outline, set up, and implement an ICT-related incident administration course of to detect, handle, and notify ICT-related incidents.
▢ Put in place early warning indicators.
▢ Set up procedures for figuring out, monitoring, logging, and classifying ICT-related incidents.
▢ Assign roles and obligations for incident administration.
▢ Create plans for communication and notification of ICT-related incidents between all key stakeholders and senior administration.
▢ Report main ICT-related incidents to related senior administration and the administration physique.
💡 How UpGuard helps
UpGuard notifies you of exterior vulnerabilities and exposures placing you and your distributors in danger with real-time safety score alerts.

7. Repeatedly monitor ICT programs
Based on Article 8 of the DORA, monetary entities should repeatedly determine all sources of threat as a part of an ICT threat administration framework.
▢ Determine, classify, and correctly doc ICT enterprise capabilities, data property, roles, and dependencies.
▢ Assess cyber threats and vulnerabilities related to ICT-supported enterprise capabilities.
▢ Carry out further threat assessments upon main modifications within the community or infrastructure.
▢ Keep inventories of knowledge property, processes that depend upon ICT third-party service suppliers, and legacy ICT programs and applied sciences.
▢ Carry out common ICT threat assessments on all legacy ICT programs.
💡 How UpGuard helps
UpGuard repeatedly displays your exterior assault floor to determine vulnerabilities, detect modifications, and uncover potential threats across the clock.

8. Perceive the obligations of the Board
Article 5 of the DORA stipulates that board administrators and government administration should settle for final duty for managing ICT threat and guaranteeing digital operational resilience.
▢ Set information security policies to make sure the upkeep of information safety.
▢ Outline roles and obligations for ICT-related capabilities and the institution of governance preparations.
▢ Outline and approve a digital operational resilience technique.
▢ Assessment and approve ICT business continuity plans, ICT inner audit plans, and using ICT providers offered by third events.
▢ Sustain-to-date on the newest information and abilities about ICT dangers.
▢ Allocate adequate funds to ICT sources, safety consciousness applications, and digital operational resilience coaching.
💡 How UpGuard helps
With UpGuard, you’ll be able to generate downloadable PDFs that summarize your safety posture and that of your distributors. The studies present a high-level overview appropriate for gaining buy-in with non-technical stakeholders.
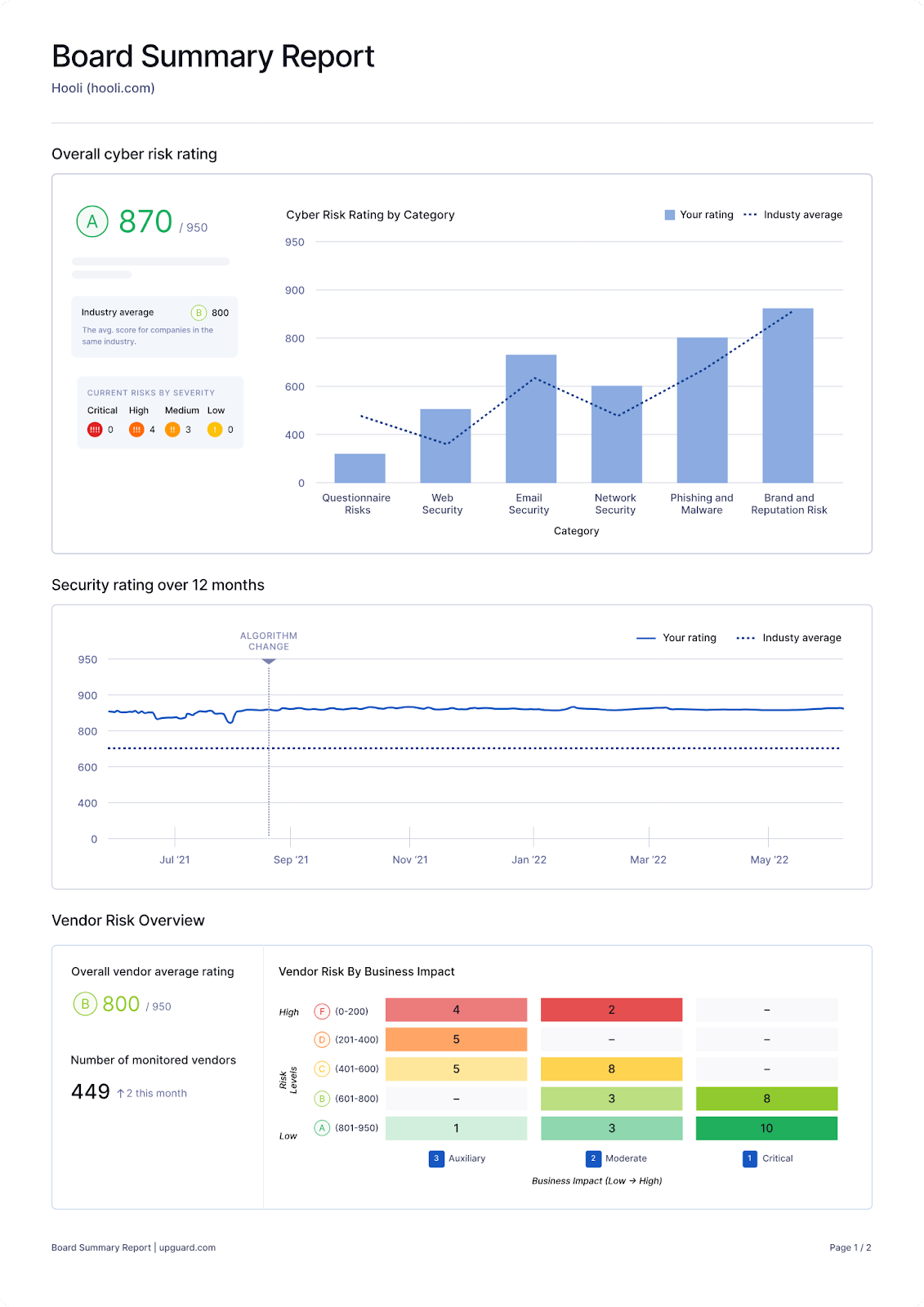
How UpGuard helps organizations adjust to the DORA framework
UpGuard supplies computerized compliance mapping and reporting in opposition to DORA by means of NIST CSF and ISO 27001 for you and your distributors. Assess your DORA compliance right now. Start your free 7-day trial.







