
Safety researchers analyzing the Alpha ransomware payload and modus operandi found overlaps with the now-defunct Netwalker ransomware operation.
Netwalker was a prolific ransomware-as-a-service (RaaS) energetic between October 2019 and January 2021, when regulation enforcement seized its dark web sites, leading to its operators going silent.
The Alpha ransomware operation (to not be confused with ALPHV/BlackCat) emerged in February 2023 however saved a low profile, did not promote on hacker boards, nor did its operators perform many assaults.
This modified not too long ago when the group launched a knowledge leak web site to record victims and publish information stolen from breached networks.
On the time of writing, Alpha reveals 9 victims on its extortion portal, and for eight of them the menace actor has already printed the stolen information.
A Neterich report from January 29 says that Alpha has steadily grown extra refined.
In the newest model, the ransomware appends a random 8-character alphanumeric extension to encrypted information.
Additionally, after many ransom be aware iterations, the newest contains directions for victims to contact the menace actor over a messaging service.
The reported ransom demand, in line with Neterich, ranges between 0.272 BTC ($13,200 by at the moment’s change price) and as much as $100,000, seemingly relying on the enterprise measurement of the sufferer.
Hyperlinks to Netwalker
A brand new report printed at the moment by Symantec’s threat analysts hyperlinks Alpha to the defunct Netwalker ransomware, based mostly on instruments and techniques, methods, and procedures utilized in assaults.
The important thing similarities the Symantec highlights embody the next:
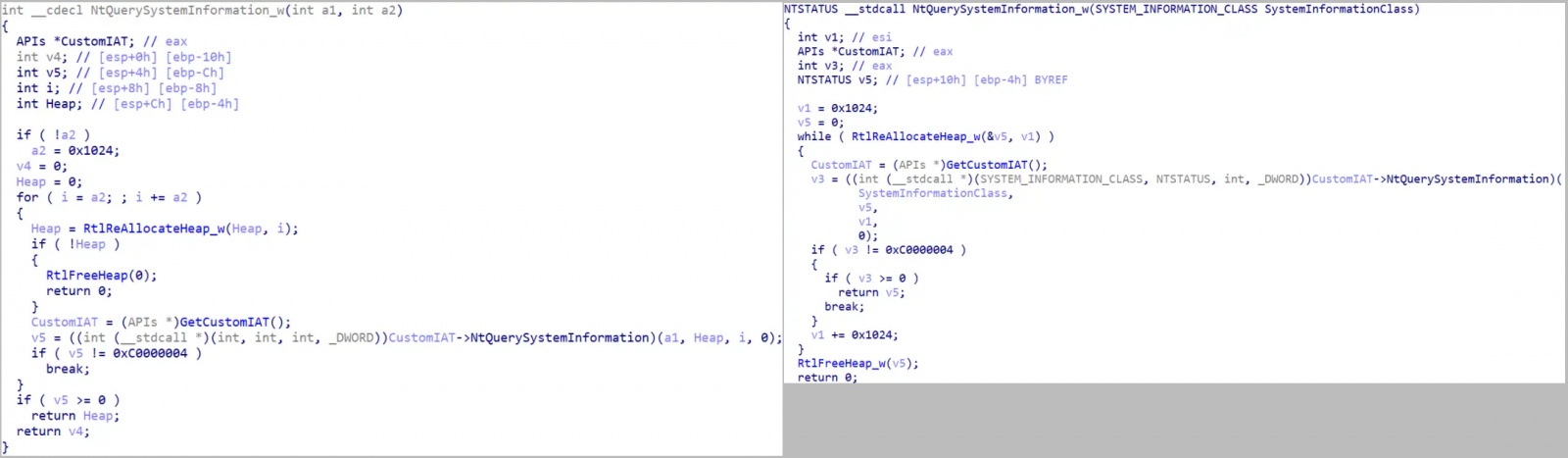
- Each Netwalker and Alpha ransomware use an identical PowerShell-based loader to ship their payloads.
- Vital code overlaps within the payload, together with the final execution stream of the principle functionalities, termination of processes and providers, and similarities in invoking system APIs.
- Configuration similarities within the record of folders, information, and extensions to be skipped, in addition to the processes and providers to be killed.
- Each delete themselves utilizing a short lived batch file after the completion of the encryption course of.
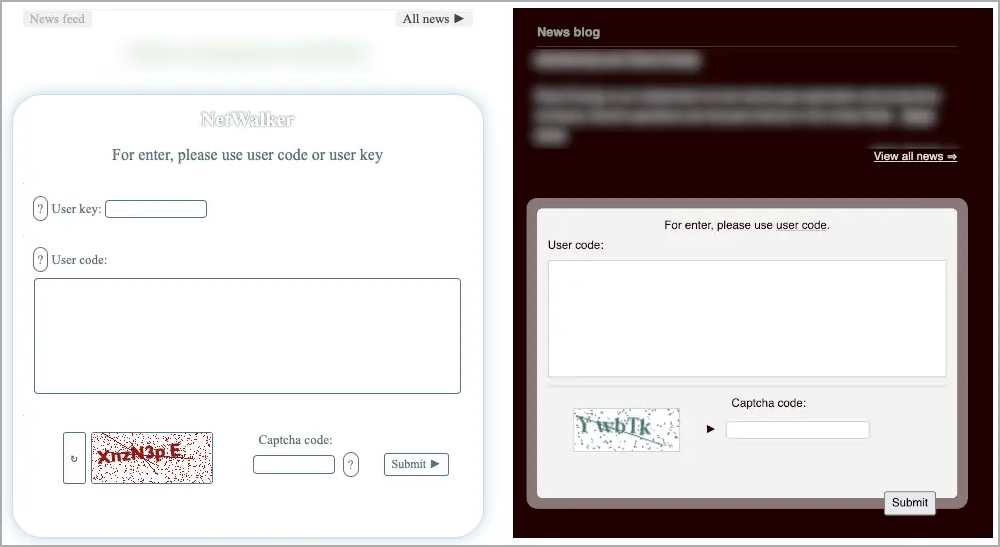
- The fee portals for each Netwalker and Alpha comprise the identical message: “For enter, please use consumer code.”
Symantec additionally stories that current Alpha assaults extensively make use of living-off-the-land instruments, together with Taskkill, PsExec, Web.exe, and Reg.exe, for evasion. Nonetheless, that is frequent to many ransomware gangs.
The above similarities point out a powerful hyperlink between NetWalker and Alpha’s builders, which might both imply a revival of NetWalker beneath the Alpha model or that its code is being reused by a brand new menace group.
Symantec notes {that a} new attacker might have acquired the NetWalker payload and tailored it for his or her ransomware operation.
Though it’s not at present a big participant on the ransomware scene, Alpha is thought to be an rising menace organizations ought to be careful for.







