
The Black Basta and Bl00dy ransomware gangs have joined widespread assaults concentrating on ScreenConnect servers unpatched towards a most severity authentication bypass vulnerability.
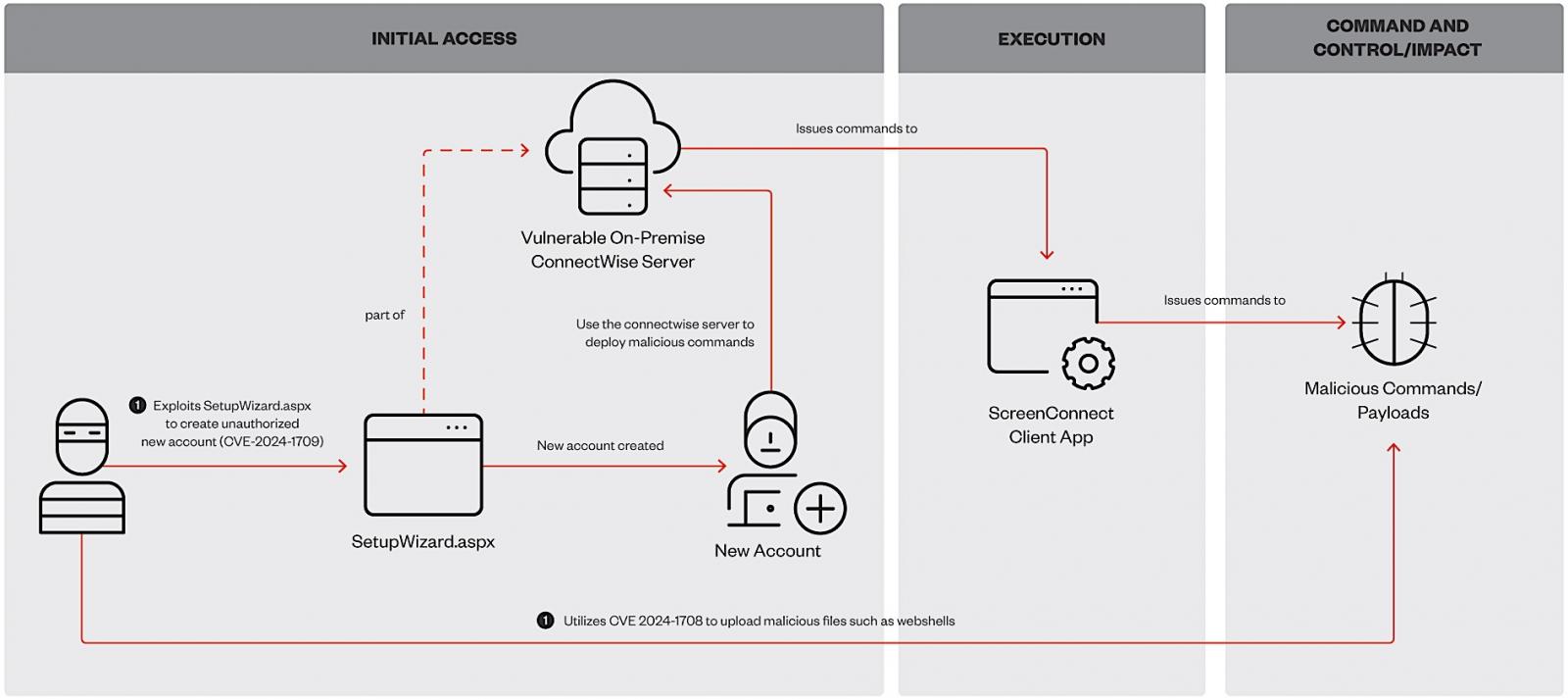
This important flaw (CVE-2024-1709) permits attackers to create admin accounts on Web-exposed servers, delete all different customers, and take over any weak occasion.
CVE-2024-1709 has been below energetic exploitation since final Tuesday, someday after ConnectWise released security updates and proof-of-concept exploits had been launched by a number of cybersecurity firms.
Final week, ConnectWise additionally mounted a high-severity path traversal vulnerability (CVE-2024-1708) that may solely be abused by menace actors with excessive privileges.
The corporate removed all license restrictions final week so clients with expired licenses can safe their servers from ongoing assaults provided that these two safety bugs affect all ScreenConnect variations.
On Thursday, CISA additionally added CVE-2024-1709 to its Known Exploited Vulnerabilities Catalog, ordering U.S. federal businesses to safe their servers by February 29.
Shadowserver says that CVE-2024-1709 is now widely exploited in assaults, with dozens of IPs concentrating on servers uncovered on-line, whereas Shodan presently tracks over 10,000 ScreenConnect servers (only one,559 working the ScreenConnect 23.9.8 patched version).
Whereas analyzing these ongoing assaults, Pattern Micro found that the Black Basta and Bl00dy ransomware gangs have additionally began exploiting the ScreenConnect flaws for preliminary entry and backdooring the victims’ networks with net shells.
Whereas investigating their assaults, Trend Micro observed reconnaissance, discovery, and privilege escalation exercise after the attackers gained entry to the community and Black Basta-linked Cobalt Strike beacons being deployed on compromised methods.
The Bl00dy ransomware gang used payloads constructed utilizing leaked Conti and LockBit Black builders. Nevertheless, their dropped ransom notes recognized the attackers as a part of the Bl00dy cybercrime operation.
Pattern Micro additionally noticed attackers deploying the multi-purpose XWorm malware with distant entry trojan (RAT) and ransomware capabilities.
Different menace actors used the newly gained entry to compromised ScreenConnect servers to deploy varied distant administration instruments, resembling Atera and Syncro, or a second ConnectWise occasion.
Sophos first revealed in a Thursday report that the not too long ago patched ScreenConnect flaws are exploited in ransomware assaults.
They noticed a number of ransomware payloads constructed utilizing the LockBit ransomware builder leaked online in late September 2022, together with a buhtiRansom payload discovered on 30 completely different networks and a second LockBit variant created utilizing the leaked Lockbit builder.
Cybersecurity firm Huntress additionally confirmed their findings final week and instructed BleepingComputer that “a neighborhood authorities, together with methods possible linked to their 911 Methods” and a “healthcare clinic” have additionally been hit by ransomware attackers who exploited the CVE-2024-1709 auth bypass to breach the victims’ networks.
“Following our detailed examination of varied menace actors exploiting vulnerabilities in ConnectWise ScreenConnect, we emphasize the urgency of updating to the newest model of the software program,” Pattern Micro mentioned at this time.
“Fast patching is not only advisable; it’s a important safety requirement to guard your methods from these recognized threats.”







