
The ALPHV/BlackCat ransomware gang has shut down its servers amid claims that they scammed the affiliate chargeable for the attack on Optum, the operator of the Change Healthcare platform, of $22 million.
Whereas BlackCat’s knowledge leak weblog has been down since Friday, BleepingComputer had confirmed that negotiation websites have been nonetheless energetic over the weekend.
At the moment, BleepingComputer confirmed the ransomware operations negotiation websites are actually shut down as effectively, indicating an additional deliberate take down of the ransomware gang’s infrastructure.
A brief standing in Russian on the messaging platform the ransomware risk actor makes use of for communication reads that they determined to show every little thing off.
It’s unclear if that is an exit rip-off or an try and rebrand the operation underneath a unique title.
Change Healthcare is a cost trade platform that connects medical doctors, pharmacies, healthcare suppliers, and sufferers within the U.S. healthcare system.
Optum allegedly pays ransom
Earlier in the present day, the Tox messaging platform utilized by the BlackCat ransomware operator contained a message that does doesn’t present any particulars about what the gang plans subsequent: “Все выключено, решаем,” which interprets to “The whole lot is off, we resolve.”
supply: BleepingComputer
This standing message has now been modified to ‘GG,’ which can imply ‘good sport.’ Nevertheless, the context of this message is unclear.
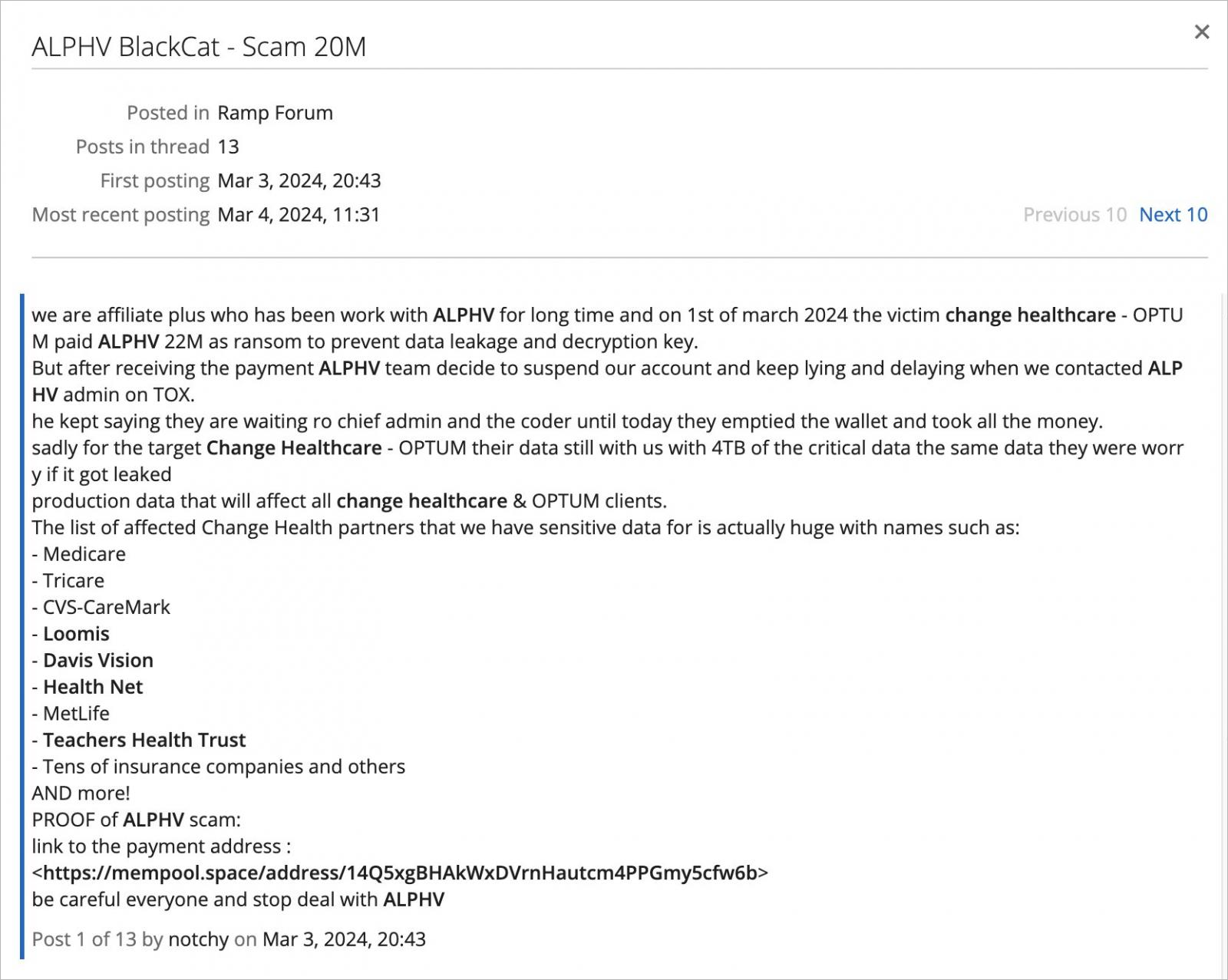
This choice could also be associated to claims from somebody describing themselves as a longtime ALPHV/BlackCat affiliate chargeable for the assault on Optum, who mentioned that ALPHV banned them from the operation and stole a $22 million ransom allegedly paid by Optum for the Change Healthcare assault.
Dmitry Smilyanets of risk intelligence firm Recorded Future shared the message from the alleged ransomware affiliate, which claimed that Optum paid ALPHV/BlackCat a ransom on March 1st to delete the information stolen from the Change Healthcare platform and to obtain a decryptor.
supply: Dmitry Smilyanets
Ransomware-as-a-service (RaaS) operations sometimes work by partnering with exterior associates, who perform assaults utilizing the operation’s encryptors.
Ransoms acquired from victims are shared between the RaaS directors and the affiliate chargeable for the breach and deploying the ransomware or stealing knowledge.
On this case, evidently the affiliate that stole knowledge from Change Healthcare acquired scammed. They declare that after Optum paid a $22 million ransom ALPHV suspended their accomplice’s account and took all the cash from the pockets.
Underneath the username “notchy,” the alleged ALPH affiliate says that they nonetheless have 4TB of Optum’s “crucial knowledge,” describing it as “manufacturing knowledge that can have an effect on all Change Healthcare and Optum shoppers.”
They declare to have knowledge from “tens of insurance coverage corporations” and different suppliers of a spread of providers from healthcare to money administration, and pharmacies.
To show their declare, notchy shared a cryptocurrency payment address with a complete of 9 transactions, an preliminary incoming switch of 350 bitcoins (a bit over $23 million), and eight outgoing ones.
The deal with sending the bitcoin has solely two transactions, one receiving 350 bitcoins and one other sending them to the alleged ALPHV pockets.
BleepingComputer contacted Optum’s mother or father firm UnitedHealth Group relating to the claims they paid a ransom cost and was instructed, “We’re centered on the investigation” and that no further feedback can be found.
Whereas it’s unclear what route BlackCat is taking, this exercise may level to the beginning of an exit rip-off, the place the ransomware operations steal their associates’ cryptocurrency after which shut down their operations.
BlackCat is a rebrand of the DarkSide ransomware operation, who additionally shut down after claiming regulation enforcement transferred cryptocurrency from their wallets. After the latest regulation enforcement operation that disrupted BlackCat’s servers, it will not be stunning to seek out that they make an identical declare in the event that they shut down.
From DarkSide to BlackMatter to ALPHV
ALPHV/BlackCat began in 2020 as DarkSide. A 12 months later, the gang attacked the Colonial Pipeline, resulting in panic and fuel outages within the US.
The ransomware gang misplaced entry to their infrastructure shortly after the assault, claiming their internet hosting supplier blocked entry to the servers.
On the time, the gang additionally mentioned that the funds on their cost server mysteriously disappeared into an unknown account.
The ransomware operation re-emerged just a few months later as BlackMatter solely to shut down four months later, in November 2021, as a result of “strain from the authorities.”
The gang resumed operations as soon as extra in February 2022 underneath the ALPHV/BlackCat title and expanded its partnership to English-speaking associates.
On the finish of final 12 months, the FBI introduced that it had breached the ransomware gang’s servers, monitored their exercise, and obtained non-public decryption keys that helped greater than 400 victims to get better their knowledge without spending a dime.
ALPHV restored its infrastructure, although, and continued breaching corporations and leaking knowledge from victims that didn’t pay a ransom.
Nevertheless, a rebrand could also be imminent.







