
GitHub has enabled push safety by default for all public repositories to stop unintentional publicity of secrets and techniques akin to entry tokens and API keys when pushing new code.
In the present day’s announcement comes after the corporate introduced push protection in beta virtually two years in the past, in April 2022, as a simple approach to stop delicate data leaks mechanically. The characteristic turned generally available for all public repos in Might 2023.
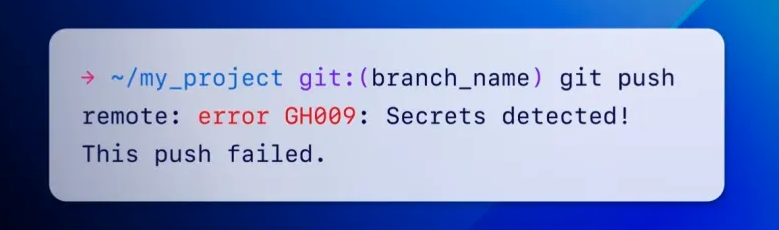
Push safety proactively prevents leaks by scanning for secrets and techniques earlier than ‘git push’ operations are accepted and blocking the commits when a secret is detected.
GitHub says that the key scanning characteristic mechanically prevents secrets and techniques from leaking by recognizing over 200 token sorts and patterns from over 180 service suppliers (API keys, personal keys, secret keys, authentication tokens, entry tokens, administration certificates, credentials, and extra).
“This week, we started the rollout of push safety for all customers. Because of this when a supported secret is detected in any push to a public repository, you should have the choice to take away the key out of your commits or, if you happen to deem the key protected, bypass the block,” GitHub’s Eric Tooley and Courtney Claessens said.
“It’d take every week or two for this variation to use to your account; you may confirm standing and opt-in early in code safety and evaluation settings.”
Even with push safety toggled on by default for all public repos, GitHub customers can circumvent the automated commit block. Whereas not beneficial, they will fully deactivate push safety of their safety settings.
Organizations subscribed to the GitHub Enterprise plan can use GitHub Superior Safety, which safeguards delicate data inside personal repositories. This additionally provides a set of different secret scanning options, in addition to code scanning, AI-driven code recommendations, and different static software safety (SAST) capabilities.
“Unintentional leaks of API keys, tokens, and different secrets and techniques threat safety breaches, popularity injury, and authorized legal responsibility at a mind-boggling scale,” Tooley and Claessens mentioned.
“In simply the primary eight weeks of 2024, GitHub has detected over 1 million leaked secrets and techniques on public repositories. That is greater than a dozen unintentional leaks each minute.”
Extra particulars on utilizing push safety from the command line or permitting some secrets and techniques to be pushed can be found on this GitHub documentation page.
As BleepingComputer has reported lately, uncovered credentials and secrets and techniques have led to a number of high-impact breaches [1, 2, 3].







