
Japan’s Laptop Safety Incident Response Group (JPCERT/CC) is warning that the infamous North Korean hacking group Lazarus has uploaded 4 malicious PyPI packages to contaminate builders with malware.
PyPI (Python Bundle Index) is a repository of open-source software program packages that software program builders can make the most of of their Python initiatives so as to add further performance to their applications with minimal effort.
The shortage of strict checks on the platform permits menace actors to add malicious packages like information-stealing malware and backdoors that infect builders’ computer systems with malware when added to their initiatives.
This malware permits the hacking group to entry the developer’s community, the place they conduct monetary fraud or compromise software program initiatives to conduct provide chain assaults.
Lazarus beforehand leveraged PyPI to distribute malware in August 2023, when the North Korean state-sponsored hackers submitted packages camouflaged as a VMware vSphere connector module.
Lazarus’ new PyPi packages
Right this moment, JPCERT/CC is warning that Lazarus has as soon as once more uploaded packages to PyPi that may set up the ‘Comebacker’ malware loader.
The 4 new packages that JPCERT/CC attributes to Lazarus are:
The primary two packages’ names create a false hyperlink to the legit ‘pycrypto‘ mission (Python Cryptography Toolkit), a set of safe hash capabilities and numerous encryption algorithms downloaded 9 million occasions each month.
Not one of the 4 packages are at present accessible on PyPI, as they had been faraway from the repository as just lately as yesterday.
Nevertheless, obtain stats monitoring platform PePy reviews a complete set up rely of three,252, so 1000’s of techniques have been compromised by Lazarus malware.
The malicious packages share the same file construction, containing a ‘check.py’ file that is not actually a Python script however an XOR-encoded DLL file executed by the ‘__init__.py’ file, which can be included within the bundle.
The execution of check.py triggers the decoding and creation of further DLL information that falsely seem as database information, as proven within the following diagram.
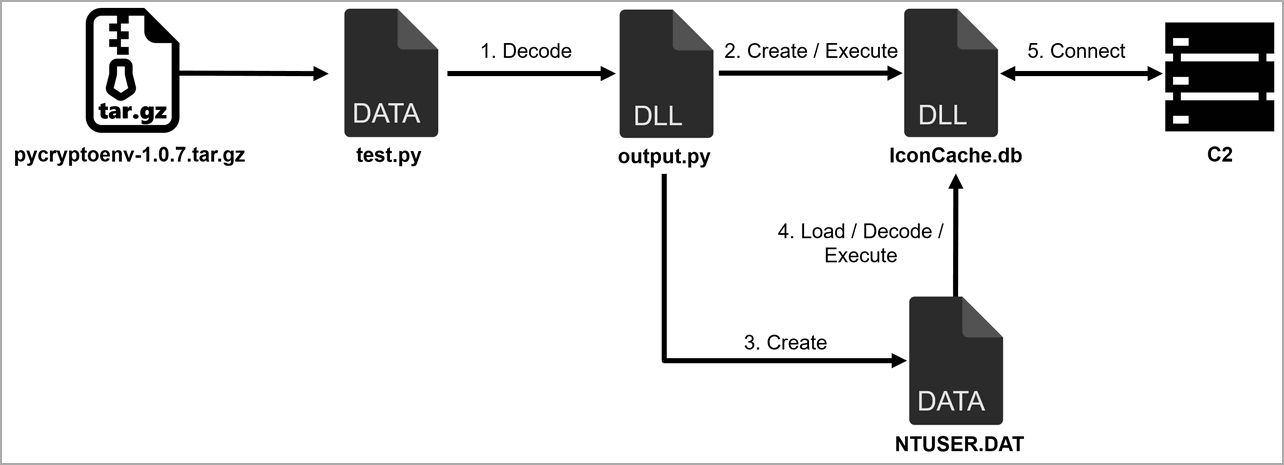
The Japanese cybersecurity company says that the ultimate payload (IconCache.db), executed in reminiscence, is a malware generally known as “Comebacker,” first recognized by Google analysts in January 2021, who reported that it was used towards safety researchers.
The Comebacker malware connects to the attacker’s command and management (C2) server, sends an HTTP POST request with encoded strings, and waits for additional Home windows malware to be loaded in reminiscence.
Primarily based on numerous indicators, JPCERT/CC says this newest assault is one other wave of the identical marketing campaign Phylum reported in November 2023 involving 5 crypto-themed npm packages.
Lazarus has an extended historical past of breaching company networks to conduct monetary fraud, often to steal cryptocurrency.
Earlier assaults attributed to Lazarus embrace the theft of $620 million worth of Ethereum from Axie Infinity’s Ronin community bridge and different crypto thefts on Harmony Horizon, Alphapo, CoinsPaid, and Atomic Wallet.
In July, GitHub warned that Lazarus was targeting developers at blockchain, cryptocurrency, on-line playing, and cybersecurity corporations utilizing malicious repositories.







