A knowledge breach happens when delicate data is uncovered to the general public with out authorization. These occasions are rising in recognition, costing companies an average of US$4.35 million per occasion. Sadly, many firms are unknowingly nonetheless repeating the identical errors inflicting among the biggest breaches in history.
To stop your enterprise from turning into one other breach static, modify your cybersecurity program to the confirmed breach prevention technique outlined on this publish.
To conveniently hold observe of every addressed merchandise, obtain this publish as a PDF right here.
The Knowledge Breach Pathway
To efficiently stop knowledge breach makes an attempt, it is important to first perceive the anatomy of a knowledge breach occasion.
The everyday cyberattack pathway resulting in a breach will be damaged down into 5 phases.
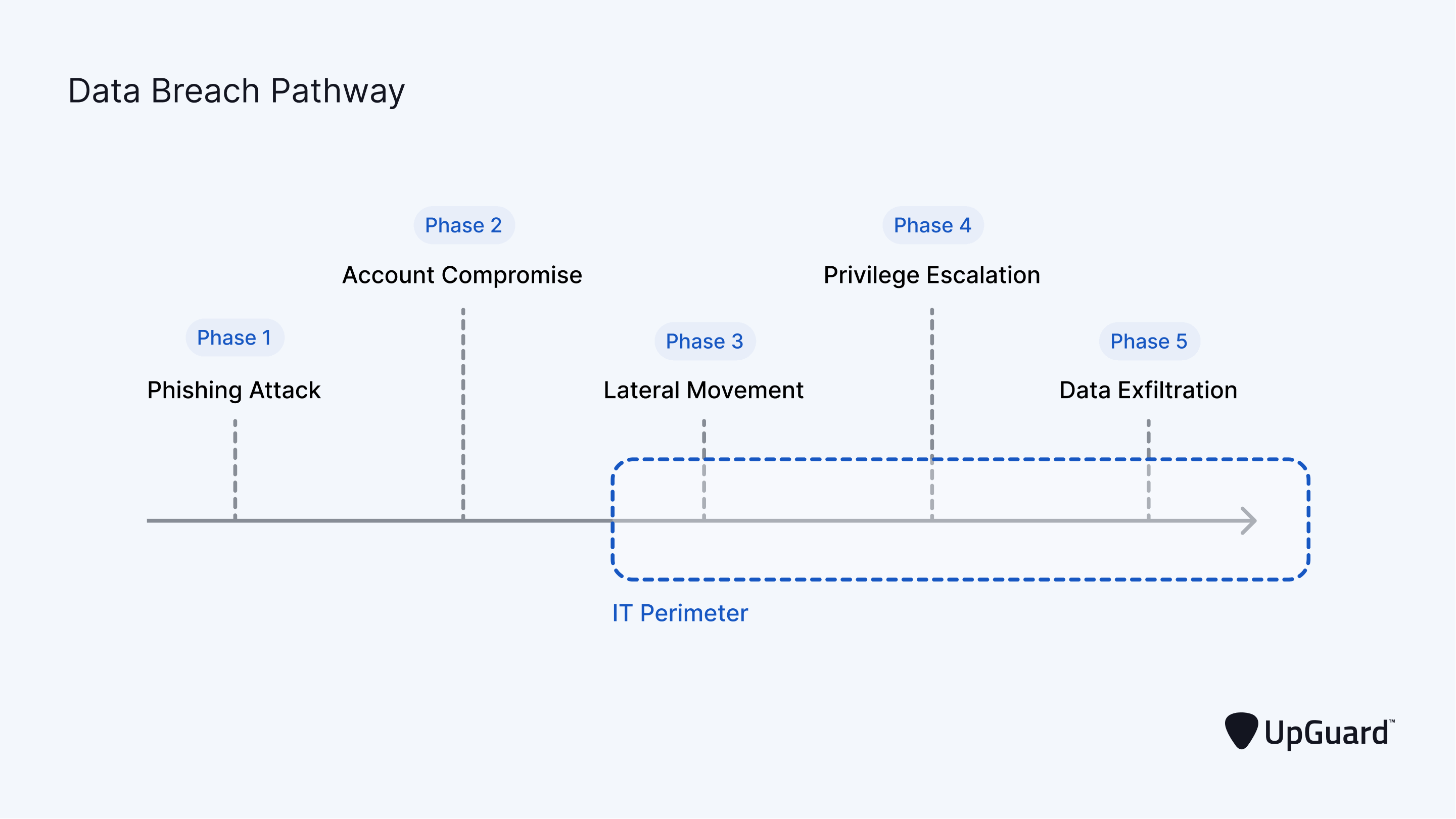
Part 1 – Phishing Assault
Throughout part 1 of the assault, an e mail posing as an vital message from an authoritative sender is distributed to a sufferer. These emails embrace malicious hyperlinks resulting in fraudulent web sites designed to steal community credentials.
In 2022, phishing was the most costly preliminary assault vector, leading to common knowledge breach harm prices of USD 4.91 million.
-2022 Value of a Knowledge Breach Report by IBM and the Ponemon Institute.
Part 2 – Account Compromise
Throughout part 2, the sufferer performs the meant motion of the phishing assault. This might contain clicking a hyperlink resulting in a credential-stealing web site or downloading a malicious file attachment that enables cybercriminals to entry the sufferer’s laptop remotely. In both case, the target is to compromise the sufferer’s account and use it to entry the group’s community.
Part 3 – Lateral Motion
After penetrating the community, hackers transfer laterally to study the community’s format. Typically hackers stay dormant for months, watching inside actions and studying person behaviors. Then, once they’re prepared, deeper community areas are accessed based mostly on these learnings utilizing beforehand compromised credentials. Hackers are additionally looking for privileged credentials to compromise on this stage to facilitate entry to extremely delicate knowledge assets.
Part 4 – Privilege Escalation
After finding and compromising privileged credentials, cybercriminals acquire deeper entry to highly-sensitive community areas that may solely be accessed with privileged accounts. As soon as inside this vital area, cybercriminals start the hunt for the next kinds of delicate knowledge:
- Private knowledge;
- Buyer knowledge;
- Social safety numbers;
- Company e mail accounts particulars;
- Private e mail account particulars, reminiscent of Gmail accounts;
- Any digital footprint particulars that may very well be utilized in an id theft marketing campaign (to probably arm additional, extra focused phishing assaults);
- Vulnerability disclosure and experiences – an inside register of all laptop system vulnerabilities safety groups are but to remediate.
Part 5 – Knowledge Exfiltration
Lastly, after invaluable knowledge assets are positioned, cybercriminals deploy trojan malware to ascertain backdoor connections to their servers (generally known as command and management servers) and start clandestinely transferring delicate knowledge out of the sufferer’s community.
Learn how to Stopping Knowledge Breaches
A easy but efficient knowledge breach prevention technique includes including resistance to the cyberattack pathway to make it more and more troublesome for hackers to progress towards their knowledge theft goal.
This technique will be damaged down into two phases.
- Stage 1 – Stopping community compromise.
- Stage 2 – Stopping entry to delicate knowledge.

Stage 1: Stopping Community Compromise

Knowledge breach makes an attempt are a lot tougher to cease after a cybercriminal has entered your personal community. The target of stage 1 is to cease knowledge breach makes an attempt earlier than your community is compromised – that’s, to forestall hackers from progressing past part 1 of the cyberattack lifecycle.
To maximise your probabilities of mitigating knowledge breaches, there ought to be a higher emphasis on safety controls stopping community penetration.
Community compromise might happen from inside community vulnerabilities or vulnerabilities throughout the third-party vendor community. A community safety technique ought to, subsequently, tackle the entire scope of assault vectors facilitating breaches – throughout each the interior and third-party assault surfaces.

This whole scope of assault floor protection is achieved via 4 cybersecurity disciplines.
1. Safety Consciousness Coaching – addresses inside assault vectors
2. Inner Vulnerability Detection – addresses inside assault vectors
3. Knowledge Leak Administration – addresses inside and third-party assault vectors
4. Vendor Danger Administration – addresses third-party assault vectors
1. Cyber Consciousness Coaching
Staff are the primary line of protection for each cybersecurity program. Regardless of how a lot you spend money on safety measures, it is ineffective if an worker will be tricked into handing over the keys to your personal community.
Cybercriminals trick staff into divulging personal community credentials in one in every of two methods:
- Phishing – The observe of sending fraudulent emails purporting to be from respected sources to coerce recipients into divulging personal data.
- Social engineering – Using emotional manipulation to pressure victims into divulging personal data. Social engineering assaults do not simply occur through e mail. They may happen over the telephone (for instance, a caller posing as a member of the IT division) and even in individual (for instance, a job applicant asking the receptionist for entry to the WI-FI community to change their resume).
Knowledge breaches occurring via compromised staff aren’t the results of fastidiously executed methods designed by inside threats. The reason being a lot less complicated. These breaches occur as a result of staff do not know find out how to acknowledge and reply to cyber threats.
Implementing cyber consciousness coaching will equip your staff to keep away from falling sufferer to phishing makes an attempt. And in case your coaching is efficient, this single effort might defend your enterprise from the main trigger of information breaches globally.
The next subjects ought to be coated in cyber consciousness coaching:
An excellent cyber consciousness coaching program ought to be coupled with frequent simulated phishing assaults to maintain cyber menace consciousness entrance of thoughts.
2. Inner Safety Vulnerability Administration
Inner safety vulnerabilities might vary from product misconfigurations, open ports, lack of MFA, and even typosquatting susceptibility. Discovering these safety threats is a collaborative effort between inside audits – utilizing danger assessments and/or safety questionnaires – and safety rankings.
Safety rankings are goal qualitative measurements of your group’s safety posture, starting from 0 to a most rating of 950. When used along side inside danger assessments, safety rankings assist you observe the influence of all required remediation efforts in your total safety posture, supporting steady alignment together with your company danger urge for food.
Learn more about security ratings >
An easy technique for minimizing community compromise danger is conserving your organization’s safety ranking as excessive as potential.
An inside safety technique targeted on mitigating community entry also needs to embrace the next frequent safety breach controls.
Safety rankings are a easy, high-level metric for monitoring knowledge breach susceptibility.
3. Knowledge Leak Administration
Most standard knowledge breach mitigation methods lack a knowledge leak administration part. That is unlucky since knowledge leaks might considerably expedite knowledge breaches by compressing the cyberattack pathway.
Knowledge leaks exposing inside credentials might assist cybercriminals to avoid all safety controls stopping unauthorized community entry, permitting them to leap straight to part 4 of the cyberattack pathway. Leaked privileged credentials compress the cyberattack pathway even additional, permitting hackers to leap straight to the ultimate knowledge exfiltration part.

Based on the 2022 Cost of a Data Breach report by IBM and the Ponemon Institute, victims that reply to knowledge breaches in lower than 200 days spend a mean of $1.1 million much less on knowledge breach damages. So in the event you’re presently a sufferer of information leaks, not solely are you rising your danger of struggling an expedited knowledge breach, you are additionally rising your danger of paying extra in knowledge breach damages.
Widespread darkish net knowledge leaks hosts embrace:
- Ransomware blogs – ransomware gang noticeboards displaying public bulletins and hyperlinks to stolen knowledge.
- Darkish net marketplaces – cybercriminals marketplaces promoting stolen knowledge from cyberattacks.
- Darkish net boards – cybercriminal boards internet hosting discussions about cybercrime.
- Telegram teams – Personal message teams between cybercriminals.
When selecting a knowledge leak detection resolution, there are two vital concerns:
False positives
Not all knowledge leak bulletins are respectable. Cybercriminals typically falsify such bulletins in ransomware blogs to mislead and divert safety investigations. Because of the excessive chance of this taking place, detected knowledge leaks ought to at all times be manually reviewed for false positives – both by inside IT safety groups or externally if leveraging the help of managed knowledge leak detection providers.
Third-Get together Knowledge Leaks
Virtually 60% of information breaches are attributable to a compromised third-party vendor (third-party breaches). Since third-party knowledge leaks facilitate third-party breaches, overlooking these assault vectors means overlooking occasions most certainly to lead to your group struggling a knowledge breach.
The scope of information leak dumps is huge and ever-expanding. Monitoring knowledge leaks at a fee that matches their look throughout hundreds of potential hosts can solely be efficiently managed with the help of an automatic scanning resolution.
UpGuard’s knowledge leak detection resolution combines an AI-assisted search engine with handbook critiques from cybersecurity analysts to cut back false positives and pointless response efforts.
For essentially the most complete protection of potential knowledge leaks linked to your enterprise or any of your distributors, UpGuard repeatedly displays frequent knowledge leak hosts on the darkish net, together with ransomware blogs and knowledge assortment releases.

4. Vendor Danger Administration
Vendor Danger Administration (VRM) is the method of mitigating safety dangers from third-party distributors and repair suppliers. VRM packages tackle the distinctive safety dangers and exposures confronted at every stage of a vendor relationship.
- Onboarding – Utilizing a mix of danger evaluation and safety rankings, a VRM program evaluates the safety postures of potential distributors to make sure alignment with danger appetites.
- Regulatory Compliance – By mapping safety questionnaire responses to widespread cybersecurity frameworks, a VRM program can establish compliance gaps to help ongoing compliance and stop expensive violations.
- Steady Monitoring – With steady third-party assault floor monitoring, a VRM program detects rising vendor safety dangers that might result in third-party breaches.
- Termination – With bespoke danger assessments scrutinizing entry ranges, a VRM program ensures offboarded distributors now not have entry to delicate assets.
A vital part of Vendor Danger Administration is third-party assault floor monitoring. This characteristic identifies potential safety vulnerabilities that might facilitate third-party breaches and, by extension, the compromise of your inside delicate knowledge.
Detecting and addressing third-party safety dangers prevents hackers from penetrating your community via a compromised vendor.
Stage 2 – Stopping Entry to Delicate Knowledge
Ought to a cybercriminal circumvent all stage 1 controls and penetrate your inside community, a knowledge breach might nonetheless be prevented with the next stage 2 controls.

Multi-Issue Authentication (MFA)
Multi-Issue Authentication (MFA) introduces a sequence of extra user-identify affirmation steps between a login request and entry approval.
Probably the most safe type of multi-factor authentication features a biometric authentication technique. Biometric knowledge, reminiscent of fingerprints, or superior types of facial recognition, may be very troublesome for cybercriminals to steal or replicate.
A strong person authentication protocol typically used along side MFA is Passwordless Authentication. Passwordless Authentication requires customers to submit proof of their id with out coming into a password. Widespread authentication strategies embrace the submission of fingerprints or {hardware} token codes.
Privileged Account Administration (PAM)
Privileged Entry Administration is the method of monitoring and securing customers with authority to entry delicate enterprise assets. With PAM controls in place, a hacker may very well be prevented from progressing past the fourth stage of the cyberattack pathway (privilege escalation).

A Privileged Account Administration technique protects delicate assets from unauthorized entry via a 4-pilar framework.

- Monitor – Determine and monitor all privileged accounts.
- Safe – Safe all privileged accounts.
- Observe – Observe all privileged entry exercise.
- Scale – Automate privileged administration.
Learn more about Privileged Access Management >
Zero-Belief Structure (ZTA)
Zero Belief is a Cybersecurity structure developed by the NIST (Nationwide Institute of Requirements and Technology). This framework assumes all community exercise, whether or not inside or exterior, is a safety menace. To show in any other case, person accounts are repeatedly authenticated every time delicate assets are requested.
A Zero Belief Structure contains different account compromise controls, reminiscent of Multi-Issue Authentication and privileged escalation administration insurance policies.
A zero-trust mannequin is so efficient at stopping knowledge breaches it is specified as the best cybersecurity structure for the Federal Authorities underneath President Biden’s 2021 Cybersecurity Executive Order.
Community Segmentation
After a hacker has breached a community, they begin shifting laterally to establish the place all of the delicate assets are positioned. Lateral motion will be disrupted by segmenting delicate community areas from normal person pathways.
To maximise obfuscation, all person accounts with entry to those closed areas ought to be guarded with Multi-Issue Authentication, with all connection requests accredited from inside leap bins (hardened machines in an remoted community internet hosting privileged credentials).
Learn network segmentation best practices >
Knowledge Encryption
Ought to all of the above stage 2 controls fail and hackers acquire entry to a delicate buyer database, the information contained therein will probably be of little or no use to hackers if it is encrypted. Ideally, goal to encrypt knowledge with the Superior Encryption Commonplace – the encryption normal trusted by authorities entities.
A knowledge encryption safety coverage ought to apply to all inside knowledge at relaxation and in movement – not simply the delicate areas, together with knowledge saved in onerous drives and laptops. Encrypting all inside knowledge might stop hackers from studying person behaviors to arm their lateral motion and privilege compromise efforts, thereby disrupting the assault’s development between phases three and 4 of the assault pathway.

The next knowledge safety measures might additionally defend extremely confidential data, reminiscent of monetary data, from compromise:
- Safety Data and Occasion Administration (SIEM) – A cybersecurity self-discipline targeted on real-time monitoring of community exercise probably resulting in breaches.
- A password supervisor – This resolution helps implement sturdy password insurance policies stopping privileged credential compromise.
The Significance of an Incident Response Plan
An Incident Response Plan (IRP) is a cyberattack handbook outlining how to answer particular cyberattacks to reduce their influence. A well-designed IRP will assist your safety group shortly reply to knowledge breach assaults, which might significantly reduce the damage costs of these events.
Learn how to create an Incident Response Plan >
Defend Your Group from Knowledge Breaches with UpGuard
UpGuard’s suite of options reduces knowledge breach dangers throughout a number of menace classes to create essentially the most complete knowledge breach prevention resolution.
- Inner and Third-Get together Danger Discovery – Based mostly on an evaluation of 70+ assault vectors, UpGuard presents a repeatedly up to date quantitative measurement of your inside safety posture and the safety postures of all of your distributors.
- Knowledge Leak Detection – With an AI-powered search engine additionally addressing third-party knowledge leaks, and a group of cybersecurity specialists assessing for false positives, UpGuard helps you effectively detect and shut down the entire scope of information leaks earlier than they’re abused by cybercriminals.







