
LockBit ransomware builders have been secretly constructing a brand new model of their file encrypting malware, dubbed LockBit-NG-Dev – more likely to change into LockBit 4.0, when regulation enforcement took down the cybercriminal’s infrastructure earlier this week.
On account of the collaboration with the Nationwide Crime Company within the UK, cybersecurity firm Pattern Micro analyzed a pattern of the newest LockBit growth that may work on a number of working techniques.
LockBit next-gen
Whereas earlier LockBit malware is in-built C/C++, the newest pattern is a work-in-progress written in .NET that seems to be compiled with CoreRT, and filled with MPRESS.
Pattern Micro says that the malware features a configuration file in JSON format that outlines the execution parameters equivalent to execution date vary, ransom observe particulars, distinctive IDs, RSA public key, and different operational flags.
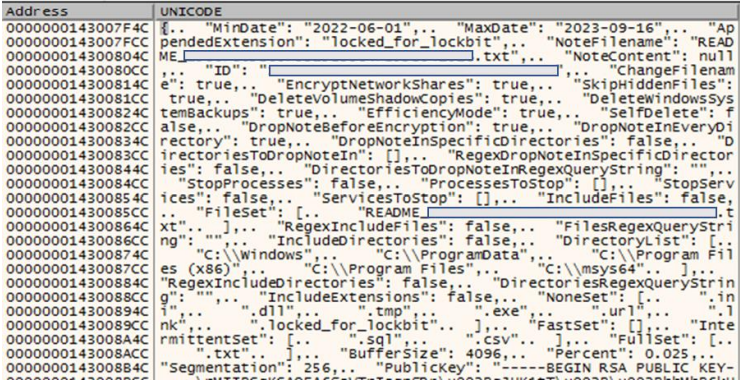
Though the safety agency says the brand new encryptor lacks some options current in earlier iterations (e.g. skill to self-propagate on breached networks, printing ransom notes on sufferer’s printers), it seems to be in its last growth phases, already providing a lot of the anticipated performance.
It helps three encryption modes (utilizing AES+RSA), particularly “quick,” “intermittent,” and “full,” has customized file or listing exclusion, and may randomize the file naming to complicate restoration efforts.
Extra choices embrace a self-delete mechanism that overwrites LockBit’s personal file contents with null bytes.
Pattern Micro has printed a deeply technical analysis of the malware, which reveals the total configuration parameters for LockBit-NG-Dev.
The invention of the brand new LockBit encrypter is one other blow regulation enforcement dealt to LockBit operators by Operation Cronos. Even when backup servers are nonetheless managed by the gang, restoring the cybercriminal enterprise must be a troublesome problem when the supply code for the encrypting malware is thought to safety researchers.







