
Microsoft is mechanically enabling Home windows Prolonged Safety on Trade servers after putting in this month’s 2024 H1 Cumulative Replace (aka CU14).
Prolonged Safety (EP) will mechanically be toggled on by default when putting in Trade Server 2019 CU14 (or later) to strengthen Home windows Server auth performance to mitigate authentication relay and man-in-the-middle (MitM) assaults.
“This can occur when working the GUI model of Setup and when working the command line model of Setup with out utilizing both the /DoNotEnableEP or /DoNotEnableEPFEEWS setup change to decide out,” said The Trade Group.
“In case your servers aren’t prepared for utilizing EP (for instance, they use SSL bridging or there are mismatches between consumer and server TLS configuration), and you don’t decide out of EP enablement throughout Setup, it’s potential that some performance might break after putting in CU14.”
Admins are suggested to guage their environments and evaluate the problems talked about within the documentation of the Microsoft-provided ExchangeExtendedProtectionManagement PowerShell script earlier than toggling EP on their Trade servers (this script mechanically updates itself on techniques related to the Web).
If encountering points after EP is enabled, admins can both be sure that all EP stipulations are met or use the script to show off the function.
They’ll additionally allow EP on older variations of Trade Server (i.e., Trade Server 2016) utilizing the identical PowerShell script on on-line servers.
Redmond additionally launched the simple-to-follow resolution move graph embedded under to assist those that nonetheless have to allow it to additional safe their Trade surroundings.
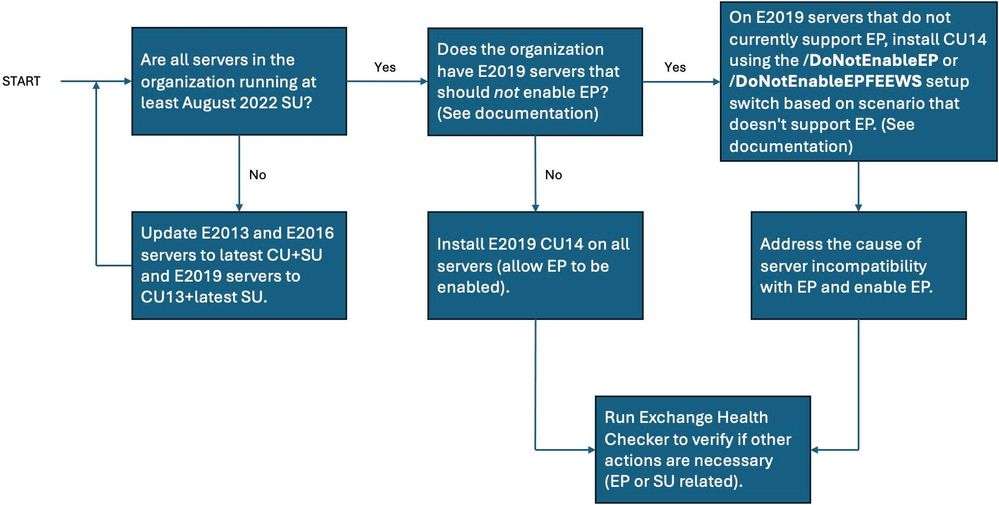
Microsoft first launched Trade Server EP help in August 2022, with cumulative updates launched as a part of the August 2022 Patch Tuesday when it mounted a number of crucial severity Trade vulnerabilities (CVE-2022-21980, CVE-2022-24477, and CVE-2022-24516), permitting for privilege escalation.
Redmond mentioned that, apart from patching these bugs, admins would additionally should allow Prolonged Safety to make sure that attackers will not have the ability to breach weak servers.
The identical request was made this Tuesday to totally deal with the CVE-2024-21410 vulnerability permitting distant risk actors to escalate privileges in NTLM relay assaults.
One 12 months later, the corporate announced that Trade Prolonged Safety can be enabled by default on all Trade servers after deploying CU14.
Microsoft’s suggestions shared in August 2023 and depending on what safety replace is put in embrace:
- Aug 2022 SU or later and EP enabled: Set up CU14 (no particular steps wanted).
- Aug 2022 SU or later, however EP not but enabled: Set up CU14 with the default of ‘Allow EP’ left on.
- Trade Server model sooner than the Aug 2022 SU: “We ship you ideas and prayers, and really sturdy however mild steerage to replace your servers to the most recent SU instantly.”
“We advocate that each one prospects allow EP of their surroundings. In case your servers are working the August 2022 SU or later SU, then they already help EP,” The Trade Group mentioned in August 2023.
“When you have any servers older than the August 2022 SU, then your servers are thought of persistently weak and must be up to date instantly. Additional, if in case you have any Trade servers older than the August 2022 SU, you’ll break server-to-server communication with servers which have EP enabled.”
Microsoft additionally urged prospects one 12 months in the past to at all times keep their on-premises Exchange servers up-to-date so that they’re able to deploy emergency safety patches.







