
A brand new phishing-as-a-service (PhaaS) named ‘Darcula’ makes use of 20,000 domains to spoof manufacturers and steal credentials from Android and iPhone customers in additional than 100 international locations.
Darcula has been used towards numerous companies and organizations, from postal, monetary, authorities, taxation departments, to telcos, airways, utility, providing fraudsters over 200 templates to select from.
One factor that makes the service stand out is that it approaches the targets utilizing the Wealthy Communication Companies (RCS) protocol for Google Messages and iMessage as a substitute of SMS for sending phishing messages.
Darcula phishing service
Darcula was first documented final summer season by safety researcher Oshri Kalfon however Netcraft analysts report that the platform has been gaining popularity on the cybercrime area, and was not too long ago utilized in a number of high-profile instances.
In contrast to conventional phishing strategies, Darcula employs trendy applied sciences like JavaScript, React, Docker, and Harbor, enabling steady updates and new function additions with out purchasers needing to reinstall the phishing kits.
The phishing equipment presents 200 phishing templates that impersonate manufacturers and organizations in additional than 100 international locations. The touchdown pages are high-quality and use the right native language, logos, and content material.
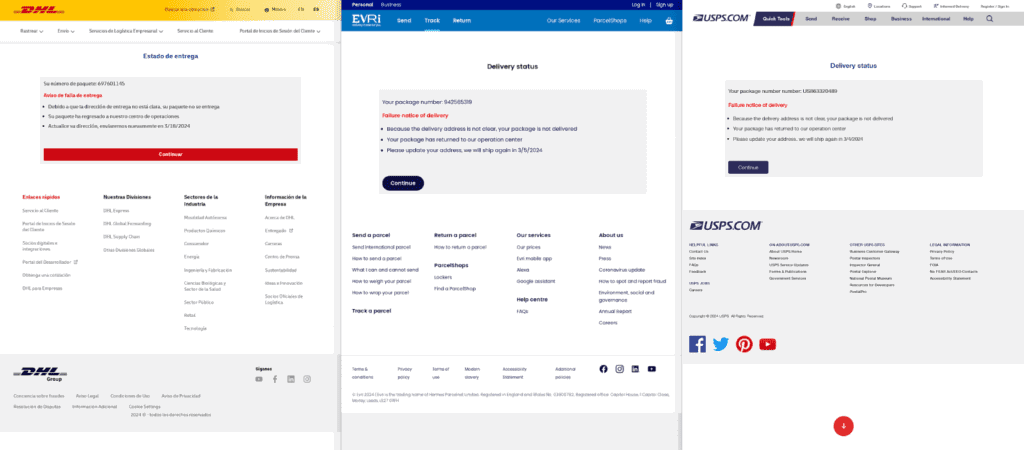
The fraudsters choose a model to impersonate and run a setup script that installs the corresponding phishing web site and its administration dashboard instantly right into a Docker atmosphere.
The system makes use of the open-source container registry Harbor to host the Docker picture, whereas the phishing websites are developed utilizing React.
The researchers say that Darcula service sometimes makes use of “.high” and “.com” top-level domains to host purpose-registered domains for the phishing assaults, whereas roughly one-third of these are backed by Cloudflare.
Netcraft has mapped 20,000 Darcula domains throughout 11,000 IP addresses, with 120 new domains being added day by day.
Abandoning SMS
Darcula diverges from conventional SMS-based techniques and as a substitute makes use of RCS (Android) and iMessage (iOS) to ship victims messages with hyperlinks to the phishing URL.
The benefit from this is that the recipients usually tend to understand the communication as professional, trusting the extra safeguards that aren’t out there in SMS.
Furthermore, since RCS and iMessage assist end-to-end encryption, it’s inconceivable to intercept and block phishing messages based mostly on their content material.
Netcraft feedback that latest world laws efforts geared toward curbing SMS-based cybercrime by blocking suspicious messages are seemingly pushing PhaaS platforms in direction of various protocols similar to RCS and iMessage.
Nonetheless, these protocols include their very own units of restrictions that cybercriminals have to beat.
For instance, Apple bans accounts sending excessive volumes of messages to a number of recipients, and Google not too long ago implemented a restriction stopping rooted Android gadgets from sending or receiving RCS messages.
.png)
The cybercriminals try to override these limitations by creating a number of Apple IDs and utilizing gadget farms to ship a small variety of messages from every gadget.
A tougher impediment is a safeguard in iMessage that solely permits recipients to click on on a URL hyperlink if they’ve replied to the message.
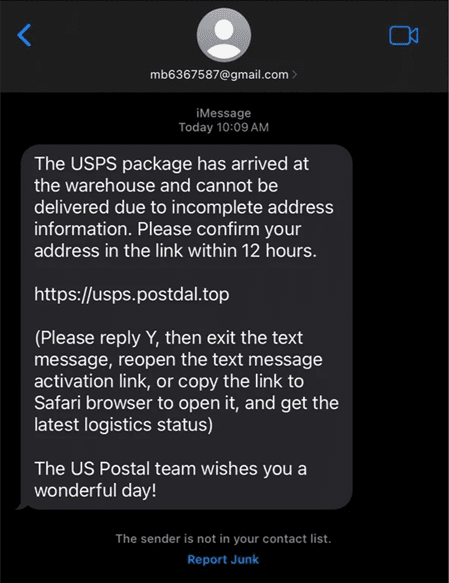
To go round this measure, the phishing message instructs the recipient to answer with a ‘Y’ or ‘1’ after which reopen the message to comply with the hyperlink. This course of might create friction that would scale back the effectiveness of the phishing assault.
Customers ought to deal with all incoming messages urging them to click on on URLs with suspicion, particularly if the sender is just not acknowledged. Whatever the platform or app, phishing menace actors will hold experimenting with new supply strategies.
Netcraft researchers additionally advocate paying consideration at inaccurate grammar, spelling errors, overly engaging presents, or calls to pressing actions.







