
A hacking group tracked as ‘UAC-0184’ was noticed using steganographic picture information to ship the Remcos distant entry trojan (RAT) onto the techniques of a Ukrainian entity working in Finland.
UAC-0184 are menace actors Pattern Micro noticed finishing up assaults in late 2023 in opposition to the Armed Forces of Ukraine, additionally utilizing the identical malware.
The menace group’s newest exercise, which began in early January 2024 and was noticed by Morphisec analysts, illustrates that they’ve expanded to focus on organizations exterior of Ukraine which are affiliated with their strategic goal.
Morphisec opted to not present technical data or particular particulars in regards to the sufferer attributable to confidentiality however nonetheless shared some knowledge on the employed assault strategies.
Utilizing photographs for loading malware
Steganography is a well-documented however hardly ever seen tactic that includes encoding malicious code into the pixel knowledge of photographs to evade detection by options utilizing signature-based guidelines.
Sometimes, the small payload chunks within the picture pixels don’t lead to an altered picture look, however within the case seen by Morphisec, the picture appears to be like visibly distorted.
This distortion, nevertheless, would solely be damaging for the attackers within the case of guide inspection, and assuming there’s none, it nonetheless works in evading detection from automated safety merchandise.
The assault chain noticed by Morphisec begins with a fastidiously crafted phishing e mail supposedly from Ukraine’s third Separate Assault Brigade or the Israel Protection Forces.
Tricked recipients opening the shortcut file attachment set off an an infection chain that launches an executable (DockerSystem_Gzv3.exe), which in flip prompts a modular malware loader named ‘IDAT.’
“Distinguished by its modular structure, IDAT employs distinctive options like code injection and execution modules, setting it other than typical loaders,” describes Morphisec.
“It employs subtle strategies corresponding to dynamic loading of Home windows API capabilities, HTTP connectivity exams, course of blocklists, and syscalls to evade detection.”
To stay stealthy, API calls aren’t written within the code in plaintext type however are as a substitute resolved at runtime utilizing a decryption key that’s a part of the assault chain.
IDAT extracts the encoded payload that’s embedded within the malicious PNG picture file after which decrypts and executes it in reminiscence, a course of that includes a number of levels and extra modules which are injected into reputable processes (Explorer.exe) and DLL information (PLA.dll).
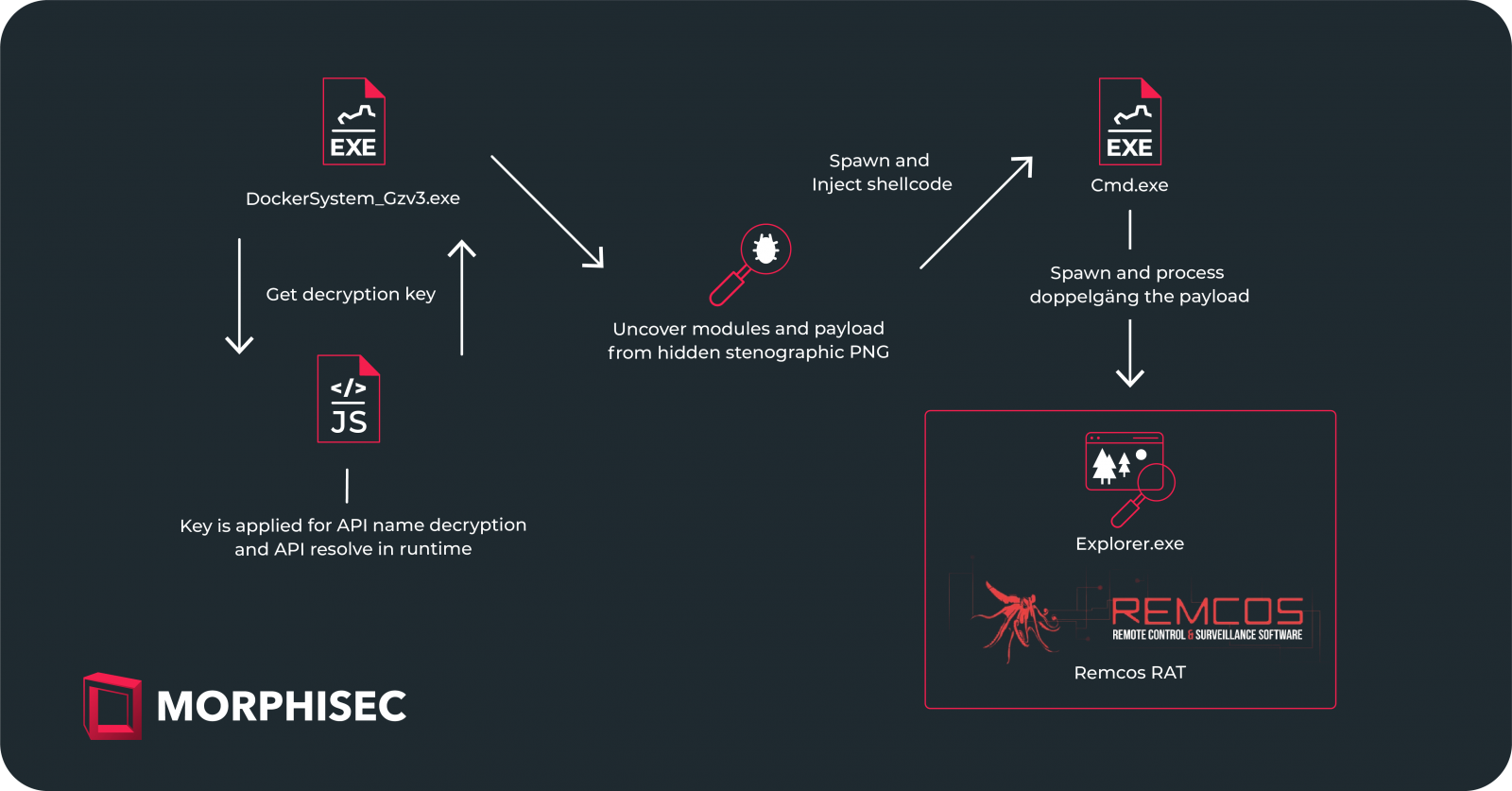
The ultimate stage includes the decryption and execution of the Remcos RAT, a commodity malware that hackers make use of as a backdoor on compromised techniques, permitting stealthy knowledge theft and sufferer exercise monitoring.
Morphisec says IDAT additionally delivers malware like Danabot, SystemBC, and RedLine Stealer, however it’s unclear if these households have been seen within the Finland-based computer systems or in numerous assaults.
The whole checklist of the symptoms of compromise (IoC) for this marketing campaign will be discovered on this report by CERT-UA.







