
Cybercriminals have been more and more utilizing a brand new phishing-as-a-service (PhaaS) platform named ‘Tycoon 2FA’ to focus on Microsoft 365 and Gmail accounts and bypass two-factor authentication (2FA) safety.
Tycoon 2FA was found by Sekoia analysts in October 2023 throughout routine menace searching, nevertheless it has been energetic since no less than August 2023, when the Saad Tycoon group supplied it via personal Telegram channels.
The PhaaS equipment shares similarities with different adversary-in-the-middle (AitM) platforms, resembling Dadsec OTT, suggesting potential code reuse or a collaboration between builders.
In 2024, Tycoon 2FA launched a brand new model that’s stealthier, indicating a steady effort to enhance the equipment. At present, the service leverages 1,100 domains and has been noticed in hundreds of phishing assaults.
Tycoon 2FA assaults
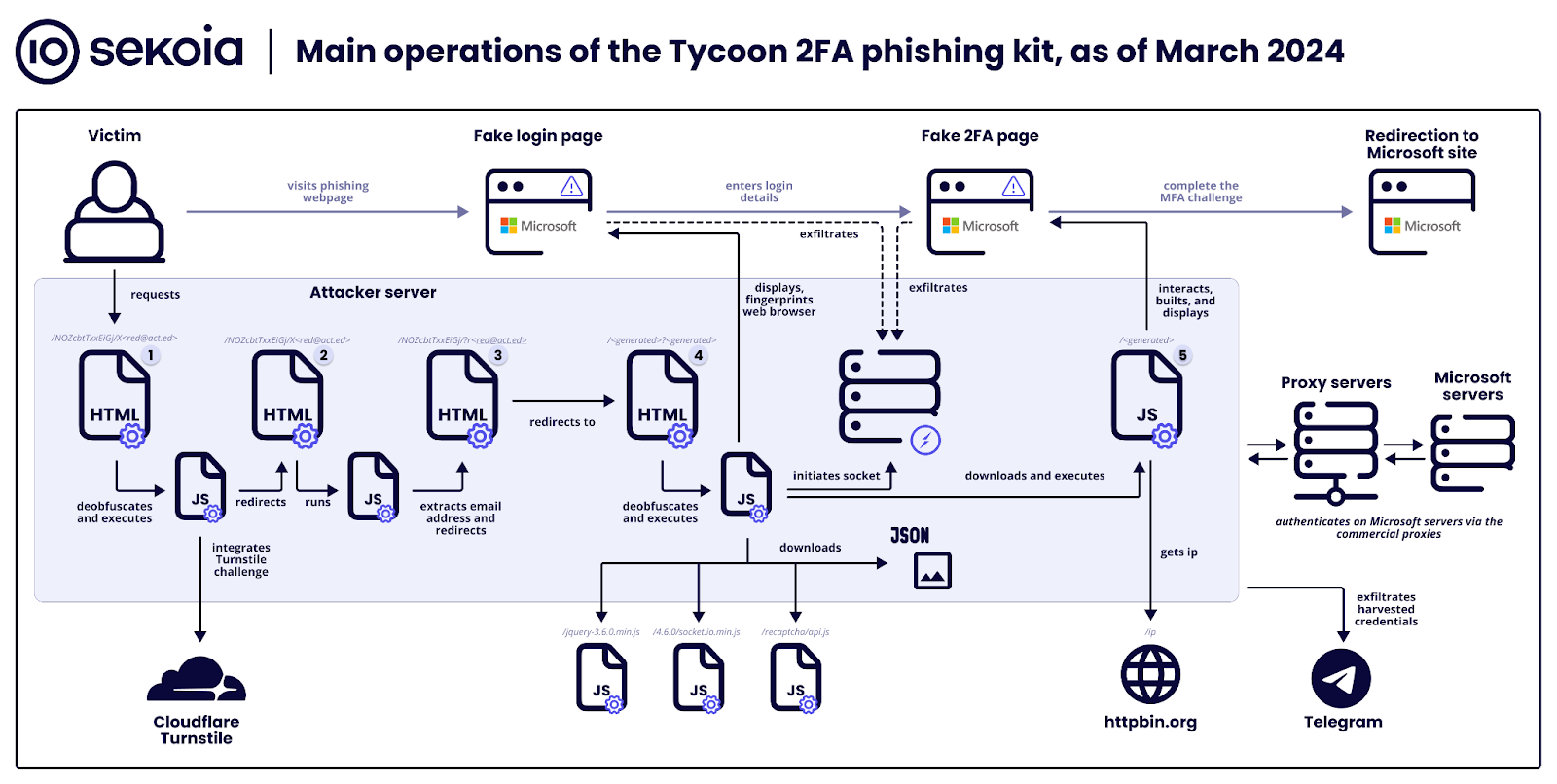
Tycoon 2FA assaults contain a multi-step course of the place the menace actor steals session cookies through the use of a reverse proxy server internet hosting the phishing net web page, which intercepts the sufferer’s enter and relays them to the official service.
“As soon as the person completes the MFA problem, and the authentication is profitable, the server within the center captures session cookies,” Skoia explains. This manner, the attacker can replay a person’s session and bypass multi-factor authentication (MFA) mechanisms.
Sekoia’s report describes the assaults in seven distinct levels as described beneath:
- Stage 0 – Attackers distribute malicious hyperlinks by way of emails with embedded URLs or QR codes, tricking victims into accessing phishing pages.
- Stage 1 – A safety problem (Cloudflare Turnstile) filters out bots, permitting solely human interactions to proceed to the misleading phishing web site.
- Stage 2 – Background scripts extract the sufferer’s e mail from the URL to customise the phishing assault.
- Stage 3 – Customers are quietly redirected to a different a part of the phishing web site, shifting them nearer to the pretend login web page.
- Stage 4 – This stage presents a pretend Microsoft login web page to steal credentials, utilizing WebSockets for knowledge exfiltration.
- Stage 5 – The equipment mimics a 2FA problem, intercepting the 2FA token or response to bypass safety measures.
- Stage 6 – Lastly, victims are directed to a legitimate-looking web page, obscuring the phishing assault’s success.
An summary of the assault is described with the diagram beneath, which incorporates all of the steps of the method.
Evolution and scale
Sekoia reviews that the most recent model of the Tycoon 2FA phishing equipment, launched this 12 months, has launched vital modifications that enhance the phishing and evasion capabilities.
Key adjustments embody updates to the JavaScript and HTML code, alterations within the order of useful resource retrieval, and extra intensive filtering to dam visitors from bots and analytical instruments.
For instance, the equipment now delays loading malicious assets till after the Cloudflare Turnstile problem is resolved, utilizing pseudorandom names for URLs to obscure its actions.
Additionally, Tor community visitors or IP addresses linked to knowledge facilities at the moment are higher recognized, whereas visitors is rejected based mostly on particular user-agent strings.
Relating to the size of operations, Sekoia reviews that it is substantial, as there’s proof of a broad person base of cybercriminals presently using Tycoon 2FA for phishing operations.
The Bitcoin pockets linked to the operators has recorded over 1,800 transactions since October 2019, with a notable increment beginning August 2023, when the equipment was launched.
Over 530 transactions have been over $120, which is the entry worth for a 10-day phishing hyperlink. By mid-March 2024, the menace actors’ pockets had acquired a complete of $394,015 value of cryptocurrency.
Tycoon 2FA is only a current addition to a PhaaS house that already presents cybercriminals loads of choices. Different notable platforms that may bypass 2FA protections embody LabHost, Greatness, and Robin Banks.
For a list of the indicators of compromise (IoCs) linked to the Tycoon 2FA operation, Sekoia makes accessible a repository with over 50 entries.







