
Firmware safety agency Binarly has launched a free on-line scanner to detect Linux executables impacted by the XZ Utils provide chain assault, tracked as CVE-2024-3094.
CVE-2024-3094 is a provide chain compromise in XZ Utils, a set of knowledge compression instruments and libraries utilized in many main Linux distributions.
Late final month, Microsoft engineer Andres Freud discovered the backdoor within the newest model of the XZ Utils package deal whereas investigating unusually gradual SSH logins on Debian Sid, a rolling launch of the Linux distribution.
The backdoor was launched by a pseudonymous contributor to XZ model 5.6.0, which remained current in 5.6.1. Nonetheless, only some Linux distributions and variations following a “bleeding edge” upgrading strategy had been impacted, with most utilizing an earlier, secure library model.
Following the invention of the backdoor, a detection and remediation effort was began, with CISA proposing downgrading the XZ Utils 5.4.6 Steady and looking for and reporting any malicious exercise.
The XZ scanner
Binarly says the strategy taken to this point within the menace mitigation efforts depends on easy checks reminiscent of byte string matching, file hash blocklisting, and YARA guidelines, which might result in false positives.
This strategy can set off important alert fatigue and would not assist detect comparable backdoors on different tasks.
To deal with this downside, Binarly developed a devoted scanner that might work for the actual library and any file carrying the identical backdoor.
Binarly’s detection methodology employs static evaluation of binaries to establish tampering of transitions in GNU Oblique Perform (IFUNC).
Particularly, the scanner examines the transitions marked as suspicious throughout the implantation of malicious IFUNC resolvers. The GCC compiler’s IFUNC attribute permits builders to create a number of variations of the identical operate which might be then chosen at runtime primarily based on numerous standards, such because the processor kind.
“One of many core methods utilized by the XZ backdoor to achieve preliminary management throughout execution is the GNU Oblique Perform (ifunc) attribute for the GCC compiler to resolve oblique operate calls in runtime,” explains Binarly.
“The implanted backdoor code initially intercepts or hooks execution.
“It modifies ifunc calls to switch a test “is_arch_extension_supported” which ought to merely invoke “cpuid” to insert a name to “_get_cpuid” which is exported by the payload object file (i.e., liblzma_la-crc64-fast.o) and which calls malformed _get_cpuid() which is implanted into the code proven within the determine under.”
The backdoor exploits this mechanism by modifying IFUNC calls to intercept or hook execution, ensuing within the insertion of malicious code.
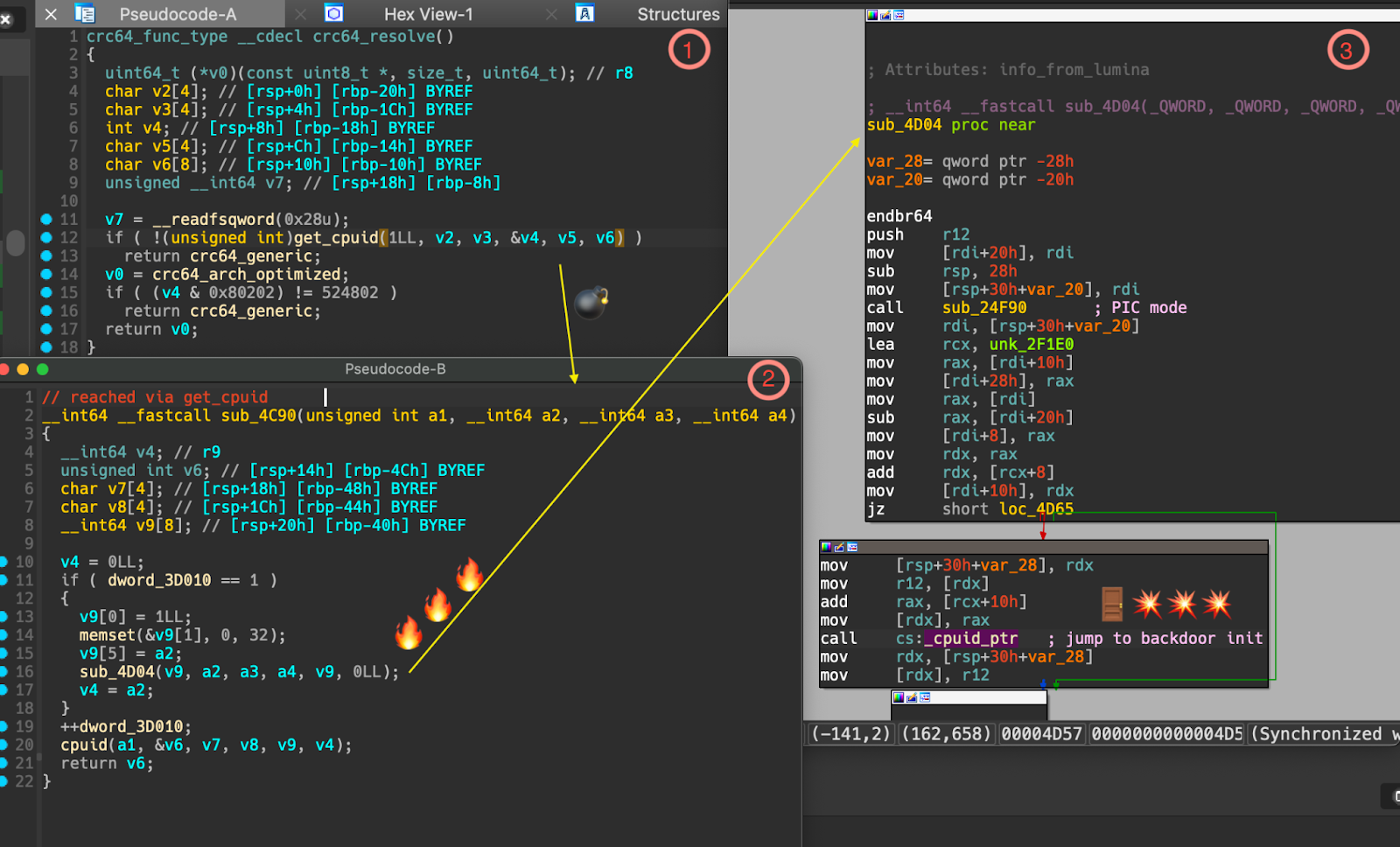
Binarly’s scanner will increase detection because it scans for numerous provide chain factors past simply the XZ Utils mission, and the outcomes are of a lot larger confidence.
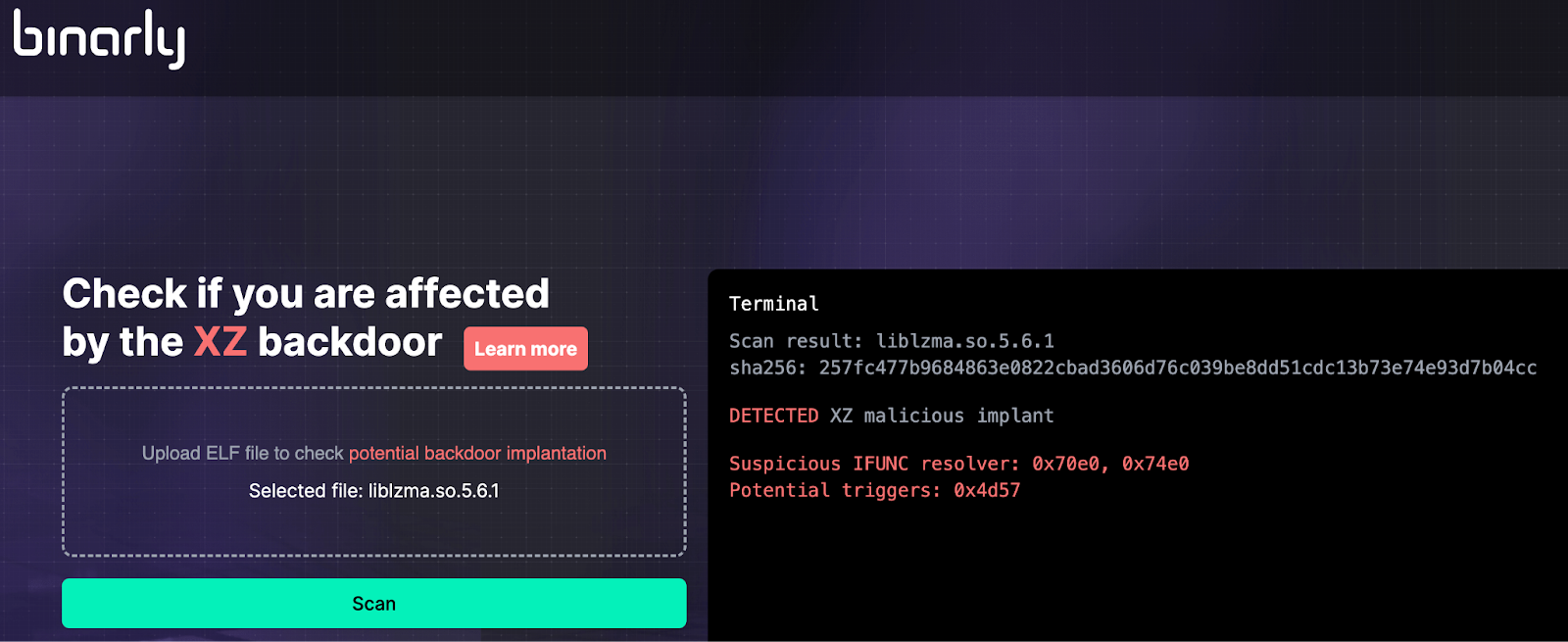
“This detection is predicated on behavioral evaluation and might detect any variants routinely if an identical backdoor is implanted someplace else,” Binarly’s lead safety researcher and CEO, Alex Matrosov, informed BleepingComputer.
“Even after recompilation or code adjustments, we are going to detect it,” Matrosov additional informed BleepingComputer.
The backdoor scanner is offered on-line at xz.fail, the place individuals can add their binary recordsdata for limitless free checks.
Replace 4/2 – Binarly has made a free API available to accomodate bulk scans for many who want it.







