
A menace researcher has disclosed a brand new arbitrary command injection and hardcoded backdoor flaw in a number of end-of-life D-Hyperlink Community Hooked up Storage (NAS) gadget fashions.
The researcher who found the flaw, ‘Netsecfish,’ explains that the difficulty resides inside the’/cgi-bin/nas_sharing.cgi’ script, impacting its HTTP GET Request Handler part.
The 2 fundamental points contributing to the flaw, tracked as CVE-2024-3273, are a backdoor facilitated by way of a hardcoded account (username: “messagebus” and empty password) and a command injection downside through the “system” parameter.
When chained collectively, any attacker can remotely execute instructions on the gadget.
The command injection flaw arises from including a base64-encoded command to the “system” parameter through an HTTP GET request, which is then executed.
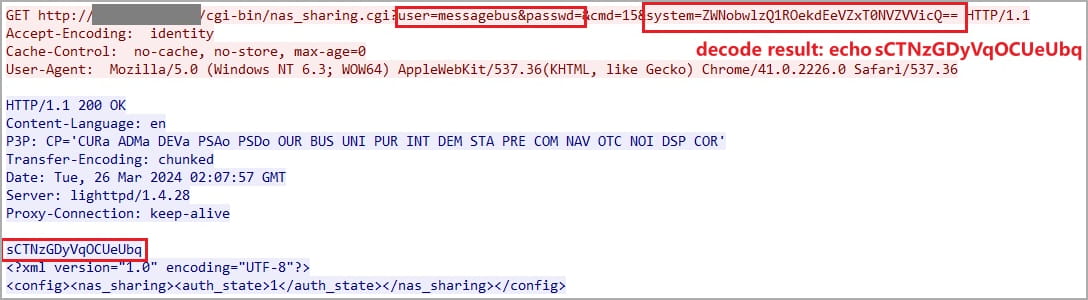
“Profitable exploitation of this vulnerability might permit an attacker to execute arbitrary instructions on the system, probably resulting in unauthorized entry to delicate info, modification of system configurations, or denial of service situations,” warns the researcher.
The gadget fashions impacted by CVE-2024-3273 are:
- DNS-320L Model 1.11, Model 1.03.0904.2013, Model 1.01.0702.2013
- DNS-325 Model 1.01
- DNS-327L Model 1.09, Model 1.00.0409.2013
- DNS-340L Model 1.08
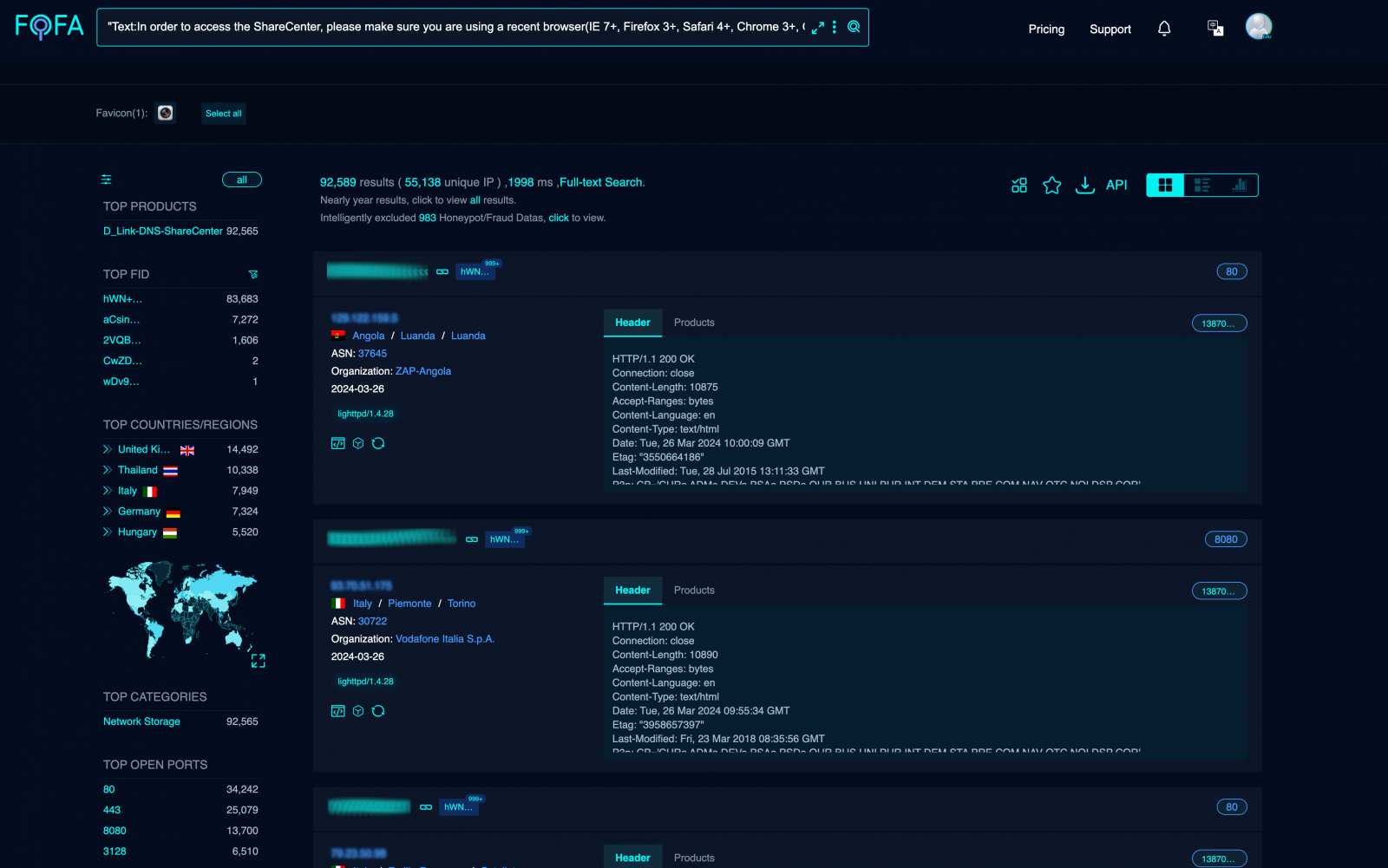
Netsecfish says community scans present over 92,000 susceptible D-Hyperlink NAS units uncovered on-line and inclined to assaults by way of these flaws.
No patches out there
After contacting D-Hyperlink concerning the flaw and whether or not a patch can be launched, the seller advised us that these NAS units had reached the tip of life (EOL) and are not supported.
“All D-Hyperlink Community Hooked up storage has been Finish of Life and of Service Life for a few years [and] the assets related to these merchandise have ceased their growth and are not supported,” acknowledged the spokesperson.
“D-Hyperlink recommends retiring these merchandise and changing them with merchandise that obtain firmware updates.”
The spokesperson additionally advised BleepingComputer that the impacted units would not have automated on-line updating capabilities or buyer outreach options to ship notifications, like present fashions.
Therefore, the seller was restricted to a security bulletin printed yesterday to lift consciousness concerning the flaw and the necessity to retire or exchange these units instantly.
D-Hyperlink has arrange a dedicated support page for legacy devices the place house owners can navigate archives to seek out the most recent safety and firmware updates.
Those that insist on utilizing outdated {hardware} ought to at the least apply the most recent out there updates, even when these will not handle newly found issues like CVE-2024-3273.
Moreover, NAS units ought to by no means be uncovered to the web as they’re generally focused to steal knowledge or encrypt in ransomware attacks.







