“Prime” is a sturdy, light-weight command-line device that gives real-time reviews on system-wide useful resource utilization. It’s generally obtainable in numerous Linux distributions. Nevertheless, we now have noticed that it might not precisely report info when executed inside a Docker container. This publish goals to convey this subject to your consideration.
CPU Stress Take a look at in Docker Container
Let’s perform an easy experiment. We’ll deploy a container utilizing an Ubuntu picture and deliberately enhance CPU consumption. Execute the next command:
docker run -ti --rm --name tmp-limit --cpus="1" -m="1G" ubuntu bash -c 'apt replace; apt set up -y
stress; stress --cpu 4'The supplied command performs the next actions:
- Initiates a container utilizing the Ubuntu picture
- Establishes a CPU restrict of 1
- Units a reminiscence restrict of 1G
- Executes the command ‘
apt replace; apt set up -y stress; stress –cpu 4’, which conducts a CPU stress check
CPU utilization reported by the highest within the host
Now, let’s provoke the highest device on the host the place this Docker container is working. The output of the highest device is as follows:
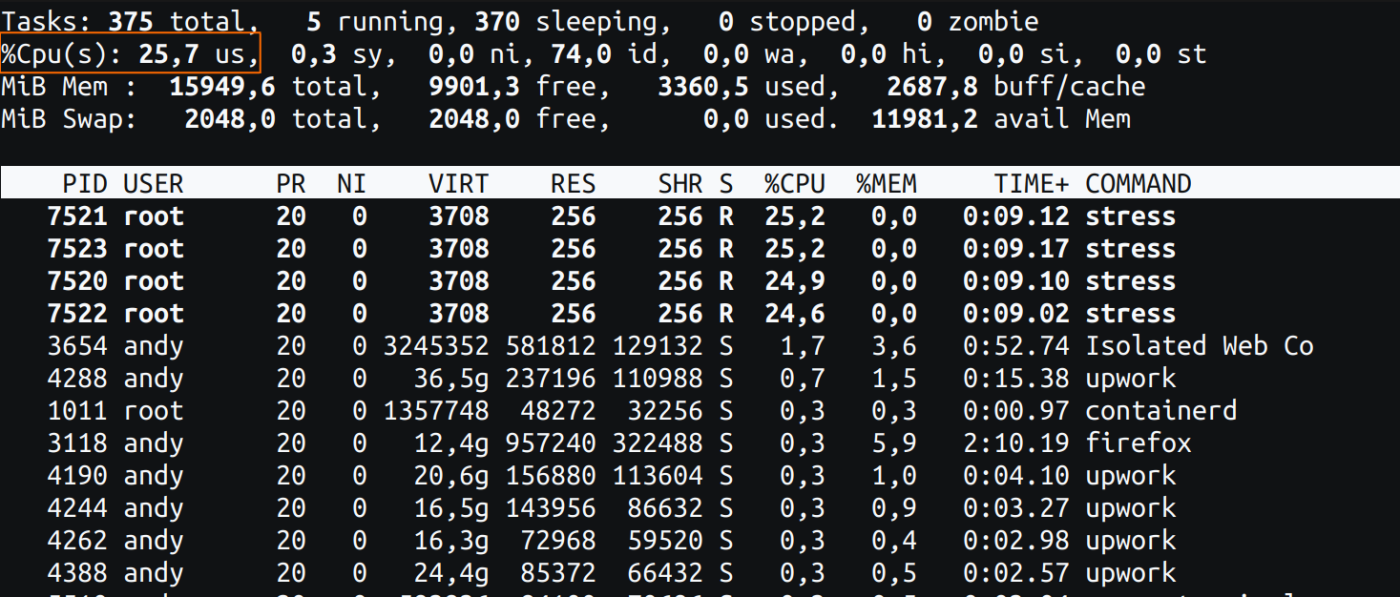
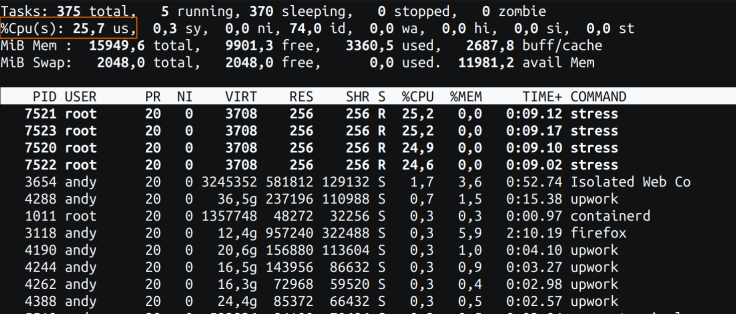 Fig 1: high command from the host
Fig 1: high command from the hostPlease be aware of the orange rectangle in Fig 1. This metric is indicated as 25% CPU utilization, and it’s the right worth. The host has 4 cores, and we now have allotted our container with a restrict of 1 core. As this single core is totally utilized, the reported CPU utilization on the host degree is 25% (i.e., 1/4 of the full cores).
CPU Utilization Reported by the Prime within the Container
Now, let’s execute the highest command throughout the container. The next is the output reported by the highest command:
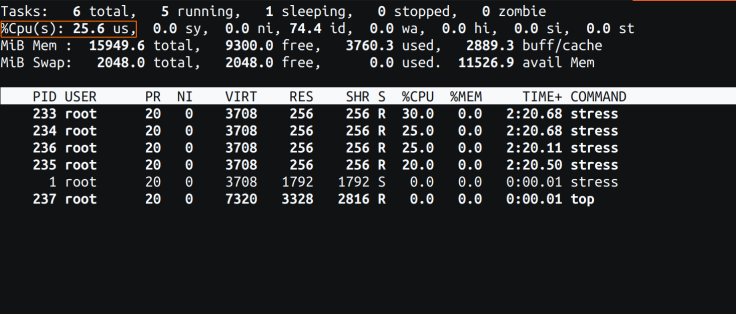 Fig 2: high command from the container
Fig 2: high command from the containerPlease observe the orange rectangle in Fig 2. The CPU utilization is famous as 25%, mirroring the host’s worth. This, nevertheless, is inaccurate from the container’s viewpoint because it has totally utilized its allotted CPU restrict of 100%.
However, it’s essential to notice that the processes listed in Fig 2 are correct. The device appropriately reviews solely the processes operating inside this container and excludes processes from your entire host.
How To Discover Correct CPU Utilization in Containers
In such a situation, to acquire correct CPU utilization throughout the container, there are a number of options:
- Docker Container Stats (docker stats)
- Container Advisor (cAdvisor)
- yCrash
1. Docker Stats
The docker stats command gives elementary useful resource utilization metrics on the container degree. Right here is the output of `docker stats` for the beforehand launched container:
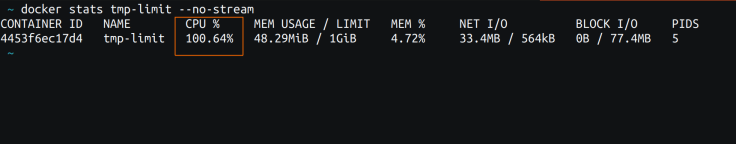 Fig 3: docker stats output
Fig 3: docker stats outputWord the orange rectangle in Fig 3. The CPU utilization is indicated as 100.64%. Nevertheless, the problem lies in the truth that `docker stats` can’t be executed throughout the container (except the docker socket is handed into the container, which is rare and poses a safety threat). It should be run from the host.
2. cAdvisor
You possibly can make the most of the cAdvisor (Container Advisor) device, which inherently helps Docker containers, to furnish container-level useful resource utilization metrics.
3. yCrash
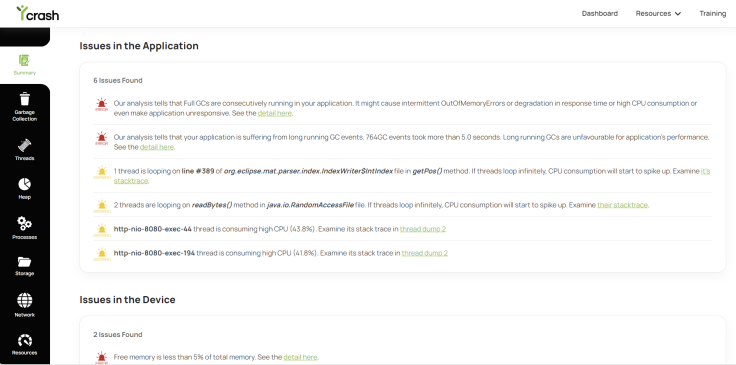 Fig 4: yCrash – root trigger evaluation report
Fig 4: yCrash – root trigger evaluation reportMoreover, you may have the choice to make use of the yCrash device, which not solely gives container-level metrics but additionally analyzes application-level dumps (corresponding to Rubbish Assortment logs, software logs, threads, reminiscence dumps, and so on.) and presents a complete root trigger evaluation report.
Conclusion
Whereas “high” serves as a dependable device for monitoring system-wide useful resource utilization, its accuracy inside Docker containers could also be compromised. This discrepancy can result in deceptive insights into container efficiency, particularly concerning CPU utilization. As demonstrated in our experiment, “high” reported 25% CPU utilization throughout the container regardless of full utilization of the allotted CPU restrict.
To acquire exact metrics inside Docker containers, various instruments corresponding to Docker Container Stats, cAdvisor, and yCrash supply beneficial insights into useful resource utilization. By leveraging these instruments, customers can guarantee correct monitoring and optimization of containerized environments, in the end enhancing efficiency and operational effectivity.







