
The RansomHouse ransomware operation has created a brand new device named ‘MrAgent’ that automates the deployment of its knowledge encrypter throughout a number of VMware ESXi hypervisors.
RansomHouse is a ransomware-as-a-service (RaaS) operation that emerged in December 2021 and is utilizing double extortion techniques. In Could 2022, the operation arrange a devoted victim extortion page on the darkish net.
Though the RansomHouse gang was not as energetic as extra notorious teams like LockBit, ALPHV/Blackcat, Play, or Clop, Trellix reports that it focused large-sized organizations all through final yr.
MrAgent vs. ESXi
Ransomware teams goal ESXi servers as a result of they deploy and serve digital computer systems that usually maintain precious knowledge that can be utilized within the subsequent extortion course of.
Additionally, ESXi servers typically run essential functions and companies for companies, together with databases and e mail servers, so the operational disruption from the ransomware assault is maximized.
Trellix analysts in collaboration with Northwave have noticed a brand new binary utilized in RansomHouse assaults that seems to be particularly designed for streamlining the gangs assaults on ESXi techniques.
The pattern was first found by researcher Florian Roth, whereas MalwareHunterTeam was the primary to tweet about it in September 2023.
MrAgent’s core perform is to determine the host system, flip off its firewall, after which automate the ransomware deployment course of throughout a number of hypervisors concurrently, compromising all managed VMs.
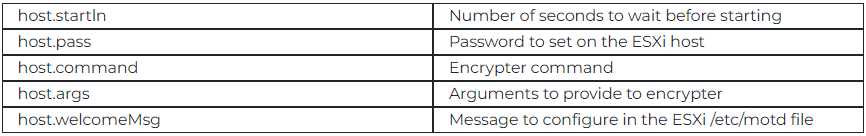
The device helps customized configurations for ransomware deployment acquired instantly from the command and management (C2) server.
These configurations embrace setting passwords on the hypervisor, configuring the encrypter command and its arguments, scheduling an encryption occasion, and altering the welcome message displayed on the hypervisor’s monitor (to show a ransom discover).
MrAgent may also execute native instructions on the hypervisor acquired from the C2 once more to delete information, drop energetic SSH periods to stop interference in the course of the encryption course of and ship again details about the operating VMs.
By disabling the firewall and probably dropping non-root SSH periods, MrAgent minimizes the possibilities of detection and intervention by directors whereas concurrently growing the affect of the assault by concentrating on all reachable VMs directly.
Trellix says it has noticed a Home windows model of MrAgent, which retains the identical core performance however options OS-specific diversifications similar to utilizing PowerShell for sure duties.
Utilizing the MrAgent device throughout completely different platforms reveals RansomHouse’s intention to increase the device’s applicability and maximize the affect of their campaigns when the goal makes use of each Home windows and Linux techniques.
“The efforts to (additional) automate the steps which are in any other case typically executed manually reveals each the curiosity and willingness of the attacking affiliate to focus on giant networks,” Trellix says within the report.
The safety implications of instruments like MrAgent are extreme, so defenders should implement complete and sturdy safety measures, together with common software program updates, robust entry controls, community monitoring, and logging to defend towards such threats.
Replace 2/16 – Publish up to date to provide credit score to researchers recognizing MrAgent first







