
Safety researchers have created a information base repository for assault and protection methods based mostly on improperly organising Microsoft’s Configuration Supervisor, which might enable an attacker to execute payloads or turn out to be a website controller.
Configuration Supervisor (MCM), previously often called System Heart Configuration Supervisor (SCCM, ConfigMgr), has been round since 1994 and is current in lots of Lively Listing environments, serving to directors handle servers and workstations on a Home windows community.
It has been the item of safety analysis for greater than a decade as an assault floor [1, 2, 3] that might assist adversaries achieve administrative privileges on a Home windows area.
On the SO-CON security conference in the present day, SpecterOps researchers Chris Thompson and Duane Michael introduced the discharge of Misconfiguration Manager, a repository with assaults based mostly on defective MCM configurations that additionally supplies sources for defenders to harden their safety stance
“Our strategy extends past cataloging the techniques of identified adversaries to incorporate contributions from the realm of penetration testing, purple crew operations, and safety analysis,” the SpecterOps clarify.
The 2 researchers say that MCM/SCCM is just not simple to arrange and that most of the default configurations depart room for attackers to take benefit.
Getting area management
In a blog post, Michael illustrates that the commonest and damaging misconfiguration researchers see of their engagements are community entry accounts (NAA) with too many privileges.
Referring to MCM/SCCM, the researcher notes that “it’s overwhelming to configure, and a novice or unknowing administrator could select to make use of the identical privileged account for the entire issues.”
Throughout their work, they encountered one situation that adopted the trail from compromising the SharePoint account of a regular person to changing into a website controller, all on account of a misconfigured MCM deployment of MCM with overprivileged NAAs.
In one other instance, Michael says that Configuration Manager sites might enroll area controllers as purchasers, which introduces the danger of distant code execution if the positioning hierarchy is just not correctly arrange.
To reveal the danger of a misconfigured MCM/SCCM deployment even additional, the researcher outlined an expertise the place the crew was in a position to get into the central administration website (CAS) database of MCM/SCCM and grant themselves a full administrator position.
From there, they may compromise the surroundings additional through the use of Configuration Supervisor to execute on a payload beforehand planted on a community share on a website consumer.
Assault and protection strategies
The Misconfiguration Manager repository created by Chris Thompson, Garrett Foster, and Duane Michael goals to assist directors higher perceive Microsoft’s instrument and “simplify SCCM assault path administration for defenders whereas educating offensive professionals on this nebulous assault floor.”
Presently, the repository describes 22 methods that might be used to assault MCM/SCCM immediately or to leverage it in post-exploitation levels.
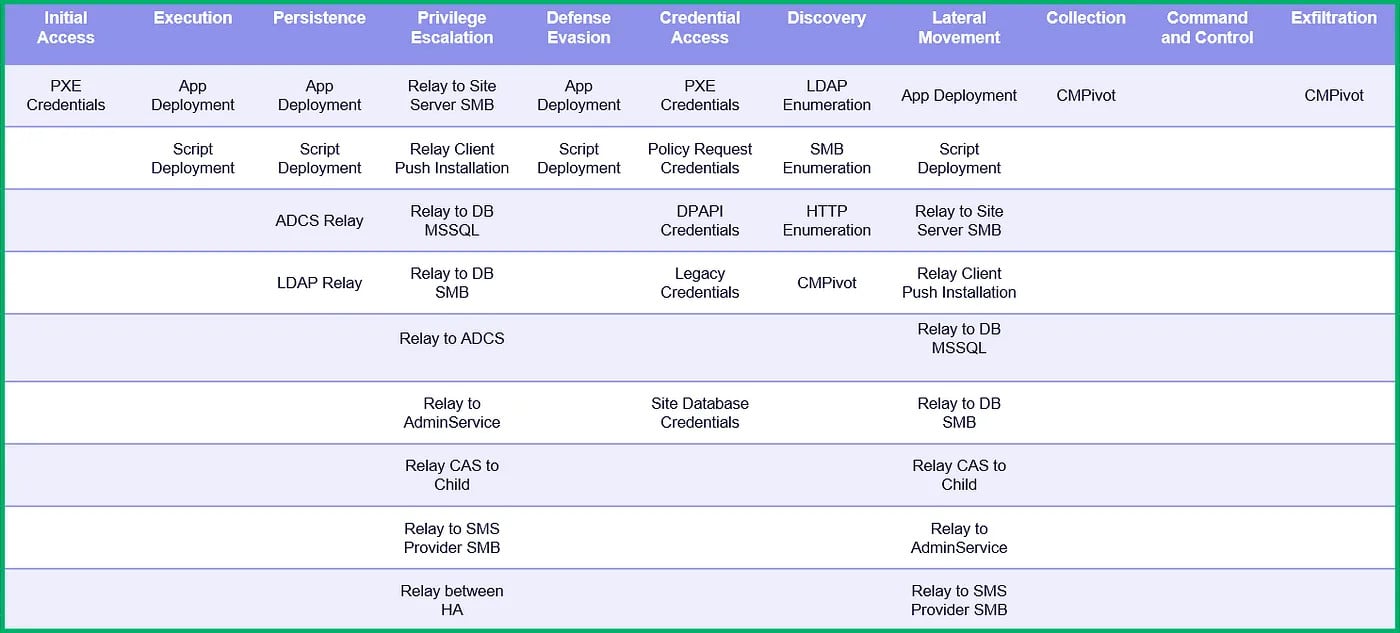
supply: Duane Michael
Relying on the surroundings, the methods described might enable entry to credentials (CRED), elevate privileges (ELEVATE), carry out reconnaissance and discovery (RECON), or achieve management of the MCM/SCCM hierarchy (TAKEOVER).
For every assault technique, the researchers additionally present data to guard the surroundings towards every of the offered offensive methods.
Protection actions are cut up into three classes:
- PREVENT: configuration adjustments that immediately mitigate or impression an assault approach
- DETECT: steerage and methods for detecting varied assault methods
- CANARY: detection methods based mostly on deception, utilizing options that attackers generally abuse
Contemplating that it’s extensively adopted and have to be put in in an Lively Listing area, MCM/SCCM can lower an organization’s safety posture if configured improperly, a job match for an skilled administrator.
Though examined by the creators of Misconfiguration Supervisor, directors are strongly suggested to check the protection strategies offered within the repository earlier than implementing them in a manufacturing surroundings.







