
A risk actor named Savvy Seahorse is abusing CNAME DNS information Area Title System to create a site visitors distribution system that powers monetary rip-off campaigns.
The risk actor targets victims by means of Fb advertisements that direct them to pretend funding platforms the place they’re tricked into depositing funds and coming into delicate private information.
A notable facet of those campaigns is that they contain chatbots that instantly work together with the victims to persuade them of excessive funding returns, automating the scamming course of for the attackers.
Infoblox researchers who discovered this operation say it has been underway since no less than August 2021, manifesting in brief assault waves that final between 5 and ten days.
Utilizing DNS CNAME information as a TDS
Savvy Seahorse creatively makes use of Canonical Title (CNAME) information as a Site visitors Distribution System (TDS) for its operations, permitting risk actors to simply handle adjustments, resembling performing IP rotation that enhances detection evasion.
A CNAME document is a DNS document that maps a website or subdomain to a different area title as an alternative of on to an IP deal with.
This causes the CNAME to behave as an alias for the goal area, making it simpler to handle redirects and be certain that any adjustments to the goal area’s IP deal with robotically apply to the CNAME as nicely.
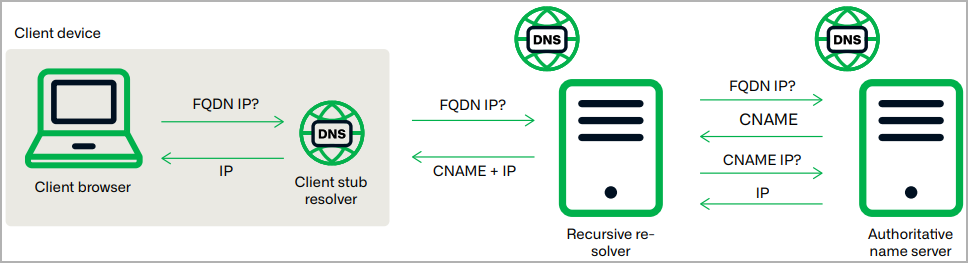
Savvy Seahorse registers a number of subdomains for its assault waves that share a standard CNAME document linking it to major/base marketing campaign area, for instance, “b36cname[.]web site.”
This permits all of those CNAME information to have the identical IP deal with inherited from the subdomain on the b36cname[.]web site, as illustrated under.
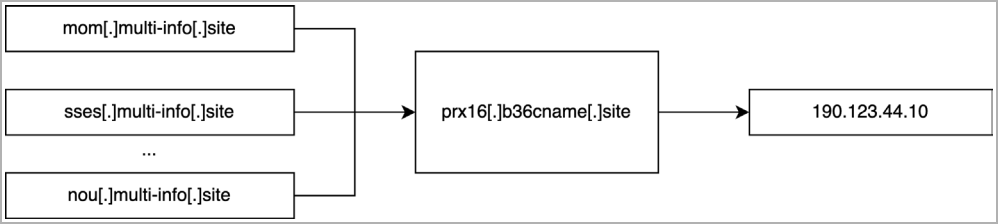
This system makes it doable to rotate to new locations when safety software program blocks a specific IP deal with or to stop detection with out altering the assault area’s DNS settings.
Infoblox says that is the primary publicly reported case of abusing DNS CNAMEs for TDS, though most definitely not the primary time it occurred, in order that they determined to call the strategy ‘CNAME TDS.’
“Savvy Seahorse is the primary publicly reported risk actor abusing DNS CNAMEs as a part of a malicious TDS,” explains Infoblox.
“Whereas it requires extra sophistication in DNS on the a part of the risk actor, it isn’t unusual—simply unrecognized up thus far within the safety literature.”
Utilizing area era algorithms (DGAs), Savvy Seahorse creates and manages 1000’s of domains utilized within the CNAME TDS system.
The risk actor makes use of wildcard DNS responses to vary the standing of those domains from “parked,” “in testing,” and in “energetic marketing campaign,” making monitoring and mapping of its infrastructure more durable.
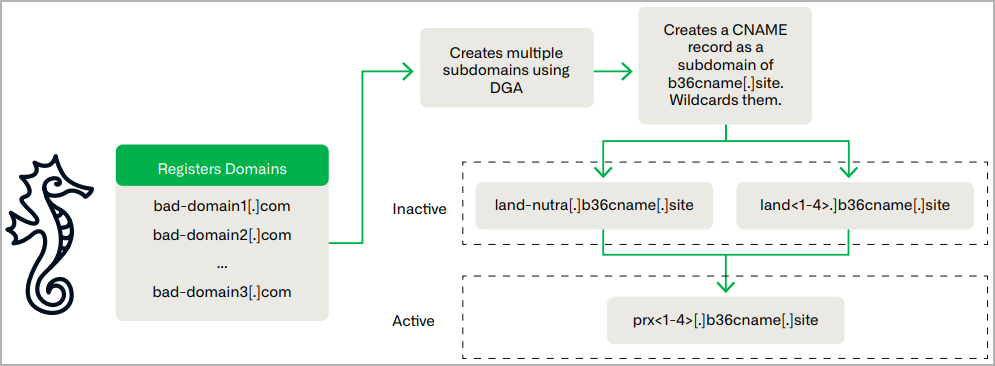
Additionally, not like most risk actors, Savvy Seahorse spreads its infrastructure throughout a number of registrars and internet hosting suppliers, which helps each evade attribution and obtain operational resilience.
Marketing campaign particulars
Savvy Seahorse promotes funding scams with lures written in English, Russian, Polish, Italian, German, French, Spanish, Czech, and Turkish, indicating the risk actor’s international concentrating on scope.
The malicious subdomains used within the assaults host registration types designed to steal the private data of the tricked victims.
As soon as that information is submitted, a secondary area validates the sufferer’s location primarily based on their IP deal with and the legitimacy of the offered data and redirects permitted customers to a pretend buying and selling platform.
There, victims can select to prime up their funding balances utilizing bank cards, cryptocurrency, and different cost strategies.
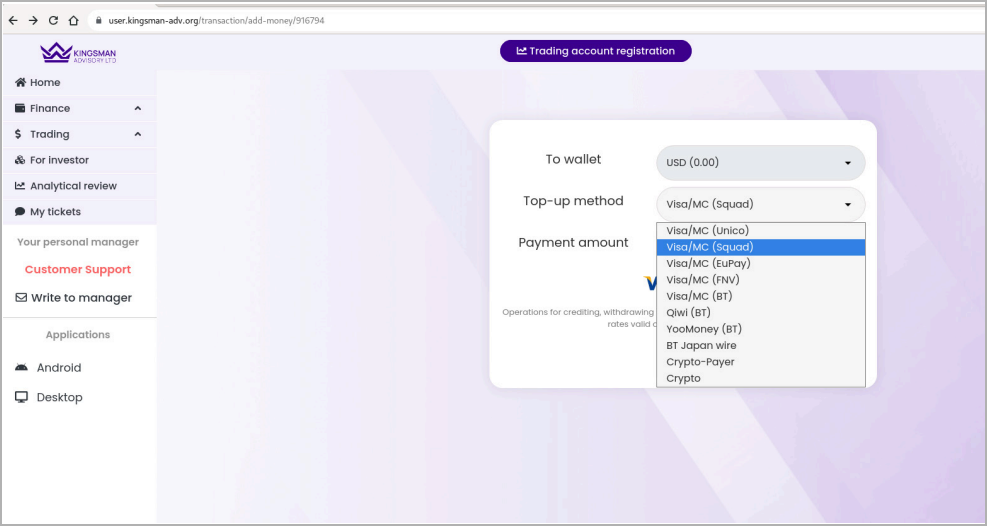
The next video demonstrates one among these fraudulent platforms intimately:
Chatbots impersonating ChatGPT, WhatsApp, and Tesla, amongst different well-known entities, enhance the obvious legitimacy and play a significant function within the social engineering facet of the assault.
Infoblox says the malicious pages additionally use Meta Pixel trackers for efficiency monitoring, which is probably going used to refine techniques.
For a whole listing of indicators of compromise and domains utilized in Savvy Seahorse campaigns, try this GitHub page.







