According to VMware, the primary half of 2020 noticed a 238% improve in cyberattacks concentrating on monetary establishments. And according to IBM and the Ponemon Institute, the typical cost of a data breach within the monetary sector in 2021 is $5.72 million.
Based mostly on these statistics, when you’re within the financial services sector, there is a very excessive likelihood that you will finally fall sufferer to a really expensive cyberattack.
Prevailing in opposition to such overwhelming odds requires a cybersecurity technique that addresses the precise cyber threats within the monetary business.
This publish outlines the highest 6 cyber threats to monetary companies and steered safety controls for mitigating every of them.
Learn how UpGuard protects the finance sector from data breaches >
1. Phishing
Phishing, a variant of social engineering, is a technique of tricking customers into divulging login credentials to realize entry to an inside community.
The most common form of phishing is e mail phishing, the place an e mail posing as reliable communication is shipped to victims.
Interacting with any of the contaminated hyperlinks or attachments in phishing emails may provoke the set up of malware on the goal pc system, or load a counterfeit net web page that harvests login credentials.
To the unsuspecting recipient, these rip-off emails appear very convincing, particularly once they’re introduced with a way of urgency.
Here is an instance of a phishing e mail posing as an pressing Coronavirus pandemic useful resource from the World Well being Group.

Track supply chain risks with this free pandemic questionnaire template >
Some phishing assaults are reply messages to an present e mail thread – a tactic often called e mail dialog thread hijacking.
The next instance demonstrates how such a cyber assault works. Joe Schmoe represents a sufferer whose e mail account will get hacked. After logging into Joe’s e mail, hackers composed a contextual reply to an present dialog, providing an contaminated attachment in response to Alice’s request for an inside doc.
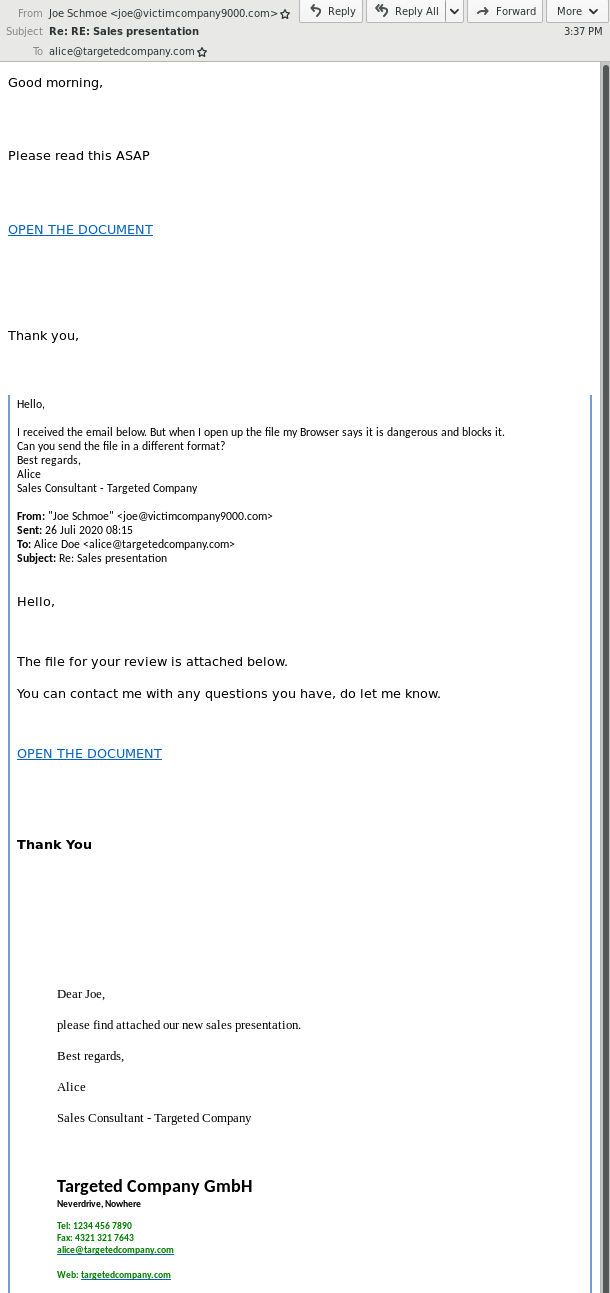
As a result of phishing emails are getting more durable to acknowledge, they’re one of the popular attack vectors for cybercrime.
It is estimated that over 90% of all successful cyberattacks start with a phishing attack and this unlucky conversion charge is tearing up the monetary business.
Phishing Assault Statistics within the Monetary Business
Phishing Assaults elevated by 22% within the first half of 2021
In simply the primary six months of 2021, phishing assaults within the monetary sector elevated by 22% for the reason that identical interval in 2020. Assaults concentrating on monetary apps elevated by 38% for a similar comparative interval.
Finance was essentially the most focused sector for phishing assaults in Q1 of 2021
The Anti-Phishing Working Group (APWG) discovered that phishing assaults have been most prevalent amongst monetary establishments in Q1 of 2021.

Virtually half of all phishing assaults in 2019 occurred within the finance sector
In accordance with Akamai’s 2019 State of the Internet report, virtually 50% of noticed phishing assaults have been linked to the monetary companies sector.
Phishing campaigns now harmonize with notable information alerts.
Phishing ways are evolving to harmonize with breaking new tales to focus on fashionable societal anxieties.
The Coronavirus pandemic has revealed a brand new stage of phishing sophistication the place phishing themes are aligned with world catastrophes to focus on fashionable societal anxieties.
The next chart signifies the connection between phishing frequency and notable information tales within the first quarter of 2020.

These regarding developments categorize phishing as one of many best cybersecurity threats within the monetary business.

2. Ransomware
Ransomware and Ransomware-as-a-Servce is one other crucial cyber threat to monetary companies. Throughout a ransomware assault, cybercriminals lock victims out of their computer systems by encrypting them with malware. The harm is simply reversed if a ransom is paid.
Ransomware attackers use a number of extortions to strain victims into paying a ransom. The preferred being publishing greater portions of seized sensitive data on prison boards till a ransom is paid.
Such extortion ways are, sadly, very efficient in opposition to monetary establishments as a result of their heavy regulations count on exemplary cyberattack and data breach resilience.
With ransomware assaults now evolving into knowledge breach territory, a profitable assault may have wider implications on regulatory compliance standards.
Ransomware Statistics within the Monetary Business
Paying a ransom may double remediation prices
The monetary companies business is a really enticing goal to ransomware gangs due to the precious buyer info they possess. The specter of leaking this knowledge on the dark web, and the ensuing reputational harm, compels many monetary companies organizations to adjust to ransom calls for.
Regardless of growing strain to take action among the many stress of a ransomware assault, the FBI strongly advises businesses to never pay ransoms.
Following the FBI’s recommendation may end in decrease harm prices, even when menace actors compromise the seized knowledge. In accordance with the State of Ransomware 2020 report by Sophos, remediation prices double when a ransom is paid.

Ransomware assaults elevated 9x between February and April 2020.
Final 12 months, within the house of solely 3 months – from the start of February to the tip of April 2020 – ransomware attacks against the financial sector increased by ninefold.
Learn how to reduce the impact of Ransomware attacks.
Ransomware assaults elevated by 520% between March and June of 2020
Between March and June 2020, phishing and ransomware assaults concentrating on banks increased by 520% in comparison with the identical interval in 2019.
A big spike in ransomware assaults was noticed in 2020 and the pattern continues to climb upwards in 2021.
Ransomware assaults elevated by 151% within the first 6 months of 2021
Atlas VPN, a New York-based VPN service supplier noticed a 151% improve in ransomware assaults within the first half of 2021 in comparison with the identical interval in 2020.

This knowledge reveals the increasing menace of ransomware throughout all sectors, not simply monetary companies companies.
This world cybersecurity risk is prompting governments to implement mitigation insurance policies to defend in opposition to nation-state ransomware attackers, like Australia’s Ransomware Action Plan.
Sure ransomware strains are extra prevalent within the monetary sector
To successfully defend in opposition to ransomware, threat intelligence groups should concentrate on the most well-liked ransomware variants concentrating on monetary techniques.
Under is a breakdown of the 11 most prevalent ransomware varieties and their proportion market share. It’s important for monetary entities to replace their Incident Response Plans to deal with every of those lively threats.
To assist this effort, every ransomware pressure under is supported with assets detailing focused defence methods.
Sodinokibi Ransomware Sources
Conti V2 Ransomware Sources
Lockbit Ransomware Sources
Clop Ransomware Sources
Egregor Ransomware Sources
Avaddon Ransomware Sources
Ryuk Ransomware Sources
Darkside Ransomware Sources
SunCrypt Ransomware Sources
Netwalker Ransomware Sources
Phobos Ransomware Sources
3. SQL Injections, Native File Inclusion, Cross-Website Scripting, and OGNL Java Injections
In accordance with the annual security report by Akamai, 94% of noticed cyber assaults within the monetary sector have been facilitated by the next 4 assault vectors:
- SQL Injections (SQLi)
- Cross-Website Scripting (XSS)
- Native FIle Inclusion (LFI)
- OGNL Java Injection
Vulnerability Discoveries Impacting the Monetary Business
4. DDoS Assaults
In 2020, the monetary sector skilled the very best variety of Distributed Denial-of-Service (DDoS) assaults.
During a DDoS attack, a sufferer’s server is overwhelmed with pretend connection requests, forcing it offline.
DDoS assaults are a well-liked cyber menace in opposition to monetary companies as a result of their assault floor is various, comprising of banking IT infrastructures, buyer accounts, fee portals, and so forth.
This makes the affect of DDoS assaults penetrate deeper for monetary entities. Cybercriminals may leverage the ensuing chaos in two alternative ways:
- Extra cyberattack campaigns may be launched whereas safety groups are distracted by a DDoS assault.
- Cybercriminals may provide to identify the DDoS assault if a ransom is paid, a method with a probability of success given the strict SLA agreements amongst monetary establishments.
DDoS Assault Statistics within the Monetary Business
Finance Sector Skilled a 30% Improve in DDoS Assaults in 2020
Between 2019 and 2020, the monetary companies business experienced a 30% increase in DDoS assaults, a spike that coincided with the beginning of the pandemic.
Cost processes aren’t all the time categorized as monetary establishments as a result of they’re normally non-public firms or third-party distributors employed by banks to course of funds. However, within the eyes of cybercriminals, their affiliation with non-public banking knowledge teams them in the identical class.
Password Login Assaults & DoS Assaults Have been the Two Main Threats to Cost Processes in 2020
In 2020, the 2 main cyber threats to fee processes have been password login assaults and DoS assaults (learn about the difference between Dos and DDoS attacks).

Finance is the Third Most Goal Sector for DDoS Assaults
Finance is throughout the high three industries most focused in DDoS assaults between 2020 and 2021.
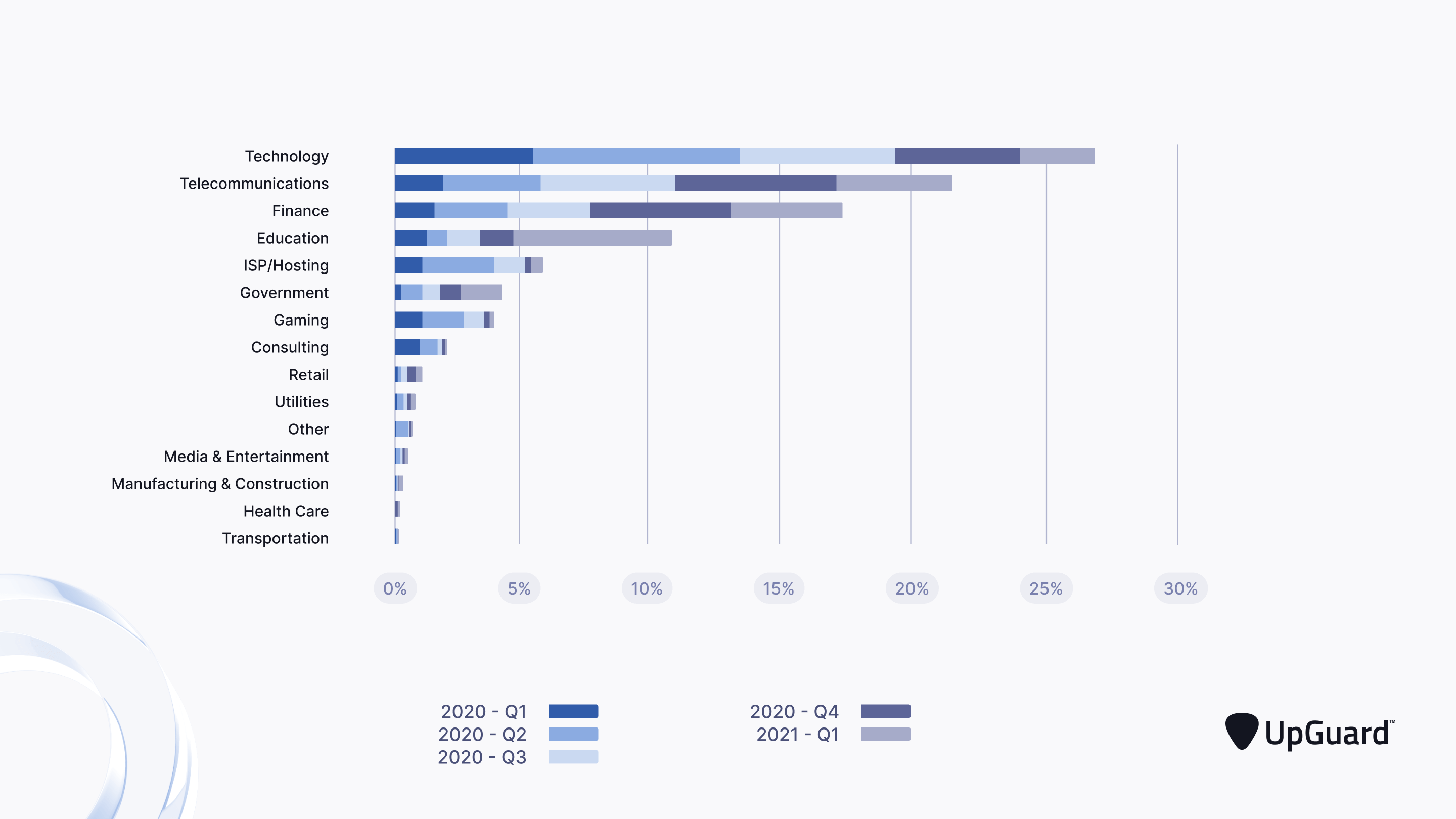
Multi-Vector DDoS Assaults Have Risen by 80% in 2021
Multi-vector DDoS assaults have risen by 80% in 2021 in comparison with the identical interval in 2020. These are DDoS assaults comprised of a number of campaigns to overwhelm safety groups.

5. Provide Chain Assaults
Throughout a supply chain attack, a sufferer is breached by means of a compromised third-party vendor of their provide chain.
Provide chain assaults make it attainable for cyber attackers to bypass safety controls by creating avenues to delicate assets by means of a goal’s third-party vendor.
As a result of, statistically, vendors don’t take cybersecurity as seriously as their clients, their compromise is normally a a lot simpler endeavour; and since third-party distributors retailer delicate knowledge for all of their shoppers, a single compromise could impact hundreds of companies.
To defend in opposition to provide chain assaults, it is really helpful for monetary companies to implement a Zero Trust Architecture with safe Privileged Access Management policies.
The inclusion of those initiatives in Biden’s cybersecurity executive order confirms their efficacy in mitigating provide chain assaults.
Provide Chain Assault Statistics within the Monetary Business
Most third-party distributors usually are not ready for cyberattacks
From the availability chain assaults analyzed by the European Union Agency for Cybersecurity, 66% of compromised suppliers both didn’t know or did not report that they have been breached.
This statistic highlights the regarding deficiency of cyber resilience amongst distributors and the determined want for a third-party risk management program to deal with this deficit.
Learn how the financial industry can better manage vendor risks.
Superior Persistent Threats Account for 50% of Provide Chain Assaults
In accordance with a report by The European Union Cybersecurity Company (ENISA), 50% of noticed provide chain assaults have been linked to the next Advanced Persistent Threats (APTs):
- APT29
- APT41
- Thallium
- Lazarus
- TA413
- TA428
Provide chain Assaults Anticipated to Improve by four-fold between 2020 and 2021
The European Union Cybersecurity Agency (ENISA) predicts that 2021 will see a 4x improve in provide chain assaults in comparison with 2020.
6. Financial institution Drops
To obfuscate their location from authorities, cybercriminals usually retailer stolen funds in pretend financial institution accounts (financial institution drops) opened with stolen buyer credentials.
Amongst cybercriminals, the gathering of buyer credentials required to create a financial institution drop is known as ‘fullz.’
A sufferer’s fullz knowledge may embody the next info:
- Full Identify
- Tackle
- DOB
- Drivers License particulars
- Credit score Rating
- Social Safety particulars
The schemes fueling standard financial institution drops are prone to adapt to digital pockets necessities as extra cybercriminals desire the superior anonymity of cryptocurrency.
In response to this cyber menace, monetary entities ought to implement safety controls particularly for the credentials generally required to open new accounts.
Financial institution Drop Stats within the Monetary Sector
The Common Value Vary for Fullz Knowledge on the Darkish Internet is $15-$60 per file.
In accordance with the Armor Dark Market Report, the typical value ranges of fullz knowledge being offered on the darkish net are as follows:
- Generic Fullz Knowledge: $15-$60
- Enterprise Fullz Knowledge: $35-$60
Generic fullz knowledge may embody:
- Identify
- DOB
- Tackle
- Mom’s maiden identify
- SSN
- Driver’s license quantity
Enterprise fullz knowledge may embody:
- Checking account numbers
- EIN
- DOB
- SSN
- Enterprise certificates
- Company officers’ names
Methods to Defend In opposition to Monetary Providers Cyber Threats
In lots of situations, cyberattacks recycle the identical assault sequence as a result of there are common security vulnerabilities throughout totally different monetary entities.
The next safety controls may tackle many of the exposures facilitating knowledge breaches within the monetary companies sector:
- Third-Occasion Threat Administration (TPRM) – A third-party risk management program will determine safety vulnerabilities for all third-party cloud companies to forestall provide chain assaults.
- Multi-Issue Authentication – Implementing an MFA coverage on all endpoints, together with cell gadgets, will make it very troublesome for menace actors to compromise privileged credentials – a crucial step previous delicate info theft for monetary companies.
- Firewall – A recurrently up to date firewall is able to detecting and blocking malware injection makes an attempt.
- Assault Floor Administration – An assault floor administration resolution able to detecting knowledge leaks will considerably cut back the probabilities of a profitable knowledge breach, each internally and all through the seller community.
- Be taught TTP (Tactics, Techniques, & Procedures) – Risk actors usually use related assault methods attributable to related vulnerabilities throughout the business. Studying widespread suspicious exercise patterns may show you how to intercept an assault try earlier than any malicious codes are injected.
- Safety scores – This characteristic helps real-time monitoring for rising safety dangers created by digital transformation. When combines with an attack surface management tool, security ratings assist uncover one of the best safety measures for a lot of widespread forms of assaults, together with malware assaults and buyer knowledge compromise.
- Common knowledge backups – Having a clear system backup available will show you how to restore enterprise continuity throughout a ransomware assault.







